This page summarizes new and enhanced features for Cisco GMM, as well as bug fixes.
Note: For information about the Gateway Provisioning Tool (GPT) used to build a supported Cisco gateway for use with GMM, see the Cisco GMM GPT Release Notes.
Release 2.3.0
Updated April 30, 2020
Enhancements
- You can now create API keys that match the user roles permissions for your organization.
- Up to 100 simultaneous firmware upgrades can be performed by each organization. The firmware installation steps are also completed faster.
- The gateway summary page now includes the cellular firmware version (in the cellular details section).
- Diagnostics now supports the following commands (in addition to show commands):
- The more command used to view the content of files on the flash.
- The service-module wlan-ap 0 status command used to check the AP (access point) status on an IR829 gateway.
Updated April 23, 2020
Enhancements
- In advanced templates, you can now specify the custom variable type, such as text, password or dropdown. This helps render the required fields in the UI while entering the values for the variables.
- IR1101 gateways now support firmware upgrades to 17.01.01.
- You can now request that a user role be created with permissions to claim, but not delete, gateways.
Release 2.2.0
Updated January 24, 2020
Single Sign-on (SSO) integration
GMM now supports Single Sign-on (SSO), which allows users to log in to GMM using their corporate account credentials.
To enable SSO, your corporate identity provider must be integrated with GMM. Your corporate identity provider must be compliant with the SAML 2.0 protocol.
Firmware upgrade enhancements
Firmware upgrades can now be uploaded at a different time than the installation process. This allows you to upload the firmware image to gateway(s) without impacting gateway operation, and then schedule the installation for a later time, such as during a planned maintenance window when impact will be minimal.
If an upload fails (for example due to a network outage), the upload can be retried until a date and time you specify, such as 24 hours after the original attempt.
Learn more
Support for Cisco Plug and Play (PnP) IR 1101 gateway provisioning
Cisco Network Plug and Play Solution (PnP) can now be used to provision Cisco routers for use with Cisco Kinetic GMM gateways. PnP applies the required GMM certificates and bootstrap configuration to make the router a Kinetic GMM gateway. Once provisioned, the gateway can register and be claimed on GMM by your organization.
PnP is used to provision IR1101 gateways that are ordered with GMM on Cisco Commerce Workspace (CCW). PnP can also be used to provision existing and RMA replacement gateways.
Learn more
Support for additional modules on IR 1101
The following module attachments are now supported by GMM for IR1101 gateways.
- Cellular module — P-LTE-MNA
- Expansion modules — IRM-1100-SPMI / IRM-1100-SP
### Updated December 03, 2019
Enhancements
- The login flow has changed to require you to enter your email and password in separate steps. This was done to support the Single Sign-On feature available in a future update.
- "Last heard time" was added to the gateway details. This indicates the time the gateway last communicated with GMM.
Updated October 31, 2019
Enhancements
- Enhanced the look and feel of the gateway details and Current Config pages.
Bug Fixes
- Fixed the issue where a warning was not shown when editing an advanced template that was in use.
- Fixed the issue where pagination was not working for advanced templates.
Release 2.1.0
Updated October 10, 2019
Bug Fixes
- Fixed the issue where gateway status was incorrect when unified AP was enabled.
- Fixed the issue where SSH to gateway failed if AP session was cleared manually.
Updated September 26, 2019
Bug Fixes
- Stale AP config is now cleared when a gateway is unclaimed and re-claimed.
- An error occurs if Site-2-Site VPN and Dual LTE Active/Active are enabled in a template, which is not supported.
Updated September 19, 2019
Enhancements
- Added a refresh option in the gateway event log.
- Minor UX enhancements to the Gateways>Summary tab.
Bug Fixes
- Fixed the issue where LAN ports status was incorrect in the Gateways>Summary page.
Updated September 5, 2019
Bug Fixes
- Fixed the issue where status was incorrect for gateways that went down during configuration.
Updated August 29, 2019
Enhancements
- Added API support to retrieve the last-heard-time of a gateway.
Bug Fixes
- All gateways can now be selected for firmware upgrades.
Updated August 22, 2019
Bug Fixes
- Fixed the issue where user role could not be changed if owner of the org was not an admin.
Updated August 15, 2019
Bug Fixes
- Fixed an issue where the gateway count was incorrect in the application templates page.
- Fixed an issue where a certificate could not be added as an application parameter in the application template.
- Fixed an issue where the application status was incorrect when a running application was unhealthy.
Updated August 8, 2019
Bug Fixes
- Fixed an issue where an IOx application upgrade sometimes failed when using application templates and policies.
- Fixed an issue where events were not published to RabbitMQ while using the gateway update_tags API.
- Fixed an issue where the LAN ports state in the UI was incorrect while using a custom subnet configuration.
Updated August 6, 2019
Application configuration and deployment enhancements
Application management templates and deployment policies have been enabled for all new organizations.
Application templates allow you to define app settings that can be applied to multiple gateways. The deployment policies apply those template settings to gateway apps based on the gateways' custom field definitions. Learn more.

Updated August 01, 2019
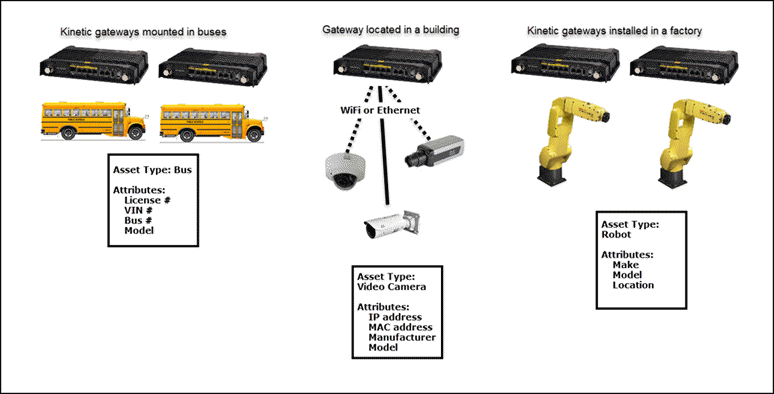
New Asset Registry feature
Asset Types can now be used to describe and group assets for management and identification.
For example, you can create an Asset Type for buses that include a license plate number, VIN number, and other attributes that describe the vehicle. An Asset Type for a DVR could include attributes for an IP address, MAC address, etc. See Manage Assets for more information.
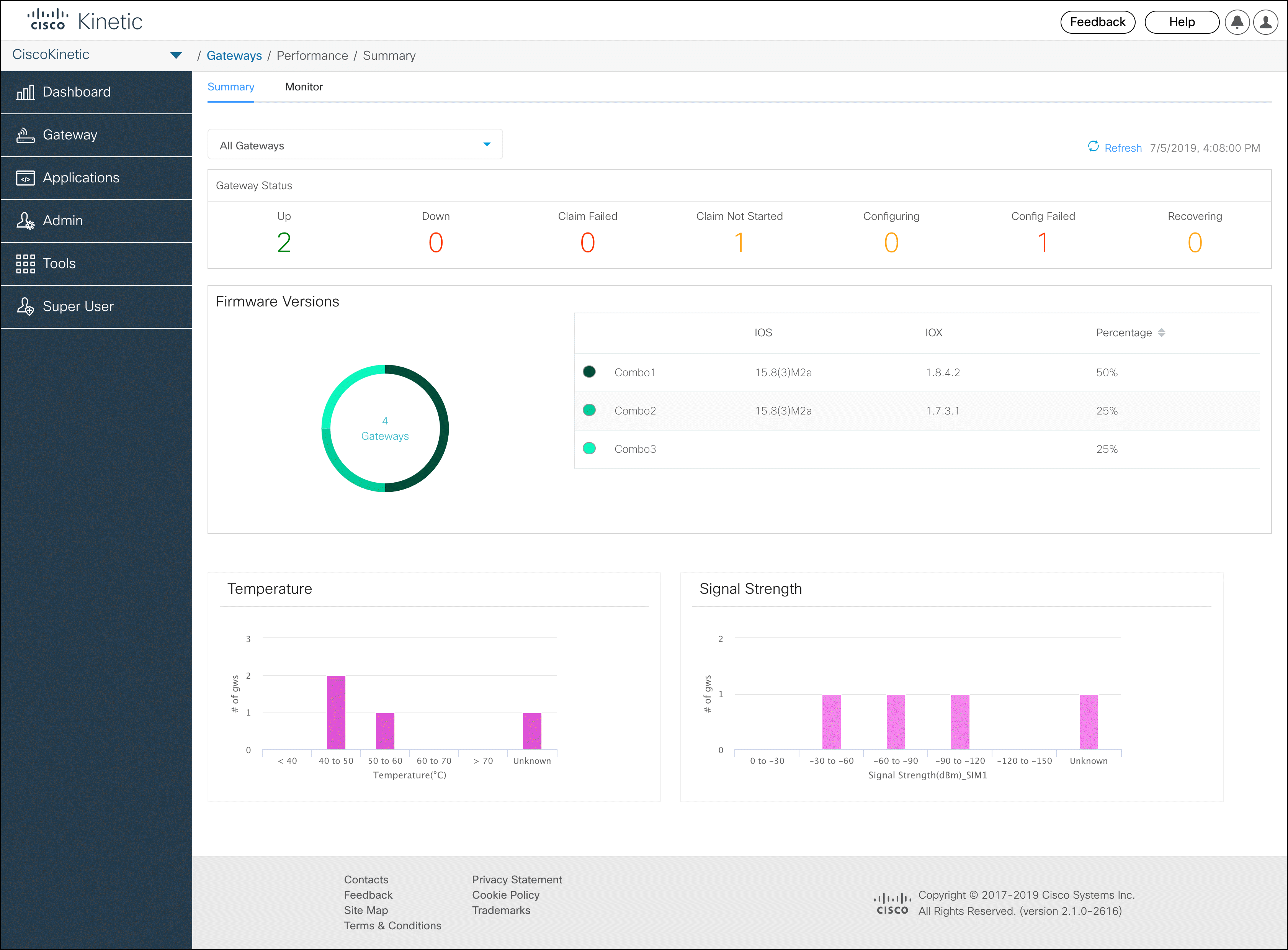
Enhanced gateway status
Improved gateway status reports provide more granular information about gateway health and logs. See the Gateway > Gateways page and Gateway status for more information.
Bug Fixes
Fixed the issue where advanced template cannot be modified when applied to a gateway.
Updated July 25, 2019
Bug Fixes
- Fixed an issue where some error messages during a firmware upgrade did not include the gateway name or serial number.
Updated July 18, 2019
Bug Fixes
- Fixed the issue where no error message is seen while installing an application without specifying gateways.
Enhancements
- Minor UX enhancements to GMM emails.
Updated July 11, 2019
Enhancements
- Show commands enhancement in Gateway Diagnostics:
Users can now execute show commands as part of gateway diagnostics. This is an enhancement from previous releases, where the list of show commands were predefined. For more details, refer to Diagnostic Operations. - Gateway Remote Access (Remote VPN) enhancements:
To provide greater security, starting with this release, a one-time username and password with a set expiration time must be requested. This is an enhancement from previous releases where the VPN credentials were fixed and common to all gateways. For more details, refer to Remote management using VPN.
Bug Fixes
- An IOx application running on a gateway prior to a firmware upgrade can now be restarted.
- IR1101 gateways can now call home to GMM using the LTE module plugged into the expansion module.
Updated June 27, 2019
Bug Fixes
- Fixed the issue with numerical operations not working within Advanced templates.
- Fixed the issue in the GPS history screen where icons appear incorrectly in the time picker.
Updated June 20, 2019
New Features
- Cisco IR1101 Integrated Services Router Rugged (IR1101) can now be managed through GMM. For more details on the features supported in IR1101, refer to GMM documentation.

- Advanced Templates that add flexible configuration capabilities for router and Access Point (WiFi-enabled gateways). For more information, see Advanced Templates.
Bug Fixes
- Fixed the issue where timestamps in the GPS history are not formatted.
Updated June 13, 2019
Bug Fixes
- Fixed the issue where formatting is lost while composing reply or forwarded emails in Outlook on Mac OS.
- Fixed the issue where a gateway takes too long to recover when deleted during a power off.
Updated June 06, 2019
Enhancements
- Improved the look and feel of the emails that are sent out by GMM.
Bug Fixes
- Fixed an issue where Dual LTE active/active support was not working with certain cellular providers.
- Fixed an issue where WiFi was intermittently configured incorrectly after a gateway recovery.
Updated May 30, 2019
Bug Fixes
- Fixed an issue where unknown error was intermittently reported while loading the CPU and memory usage of an application.
Updated May 23, 2019
Enhancements
- The user interface font family and sizes are now consistent.
Updated May 21, 2019
Firmware release
- The firmware image 15.8(3)M2a is now available for upgrading the IR8xx gateways. This upgrade addresses a Cisco Security Advisory. The previous image 15.8(3)M0a has been removed and is not available for new upgrades.
Updated May 16, 2019
Enhancements
- Improved the time taken to load the gateway names in the dropdown menus that list gateways by group.
Bug Fixes
- Fixed an issue where the Dual LTE Active/Active setting was initially Disabled when claiming a gateway.
- Fixed an issue where data destination logs were not getting displayed.
Updated May 09, 2019
Enhancements
- Gateways can be searched by template name.
- The cellular usage chart in the dashboard loads faster.
- Configuration changes can be pushed to gateways that use advanced templates without reclaiming the gateways or resetting the config of the gateways. The changes are not applied until the gateway is rebooted. After making config changes, a warning message appears with the option to reboot and apply the changes, or cancel the operation.
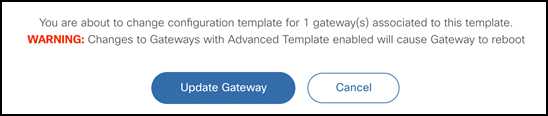
__
- Fixed the issue where internal template change was not picked up after a Reset Config.
Updated May 02, 2019
Bug fixes
- Fixed a loading issue for 15 / 30 days cellular usage metrics in the dashboard and gateway monitor pages.
Updated April 25, 2019
Enhancements
A single field can now be used to enter either an address or latitude and longitude for a gateway.
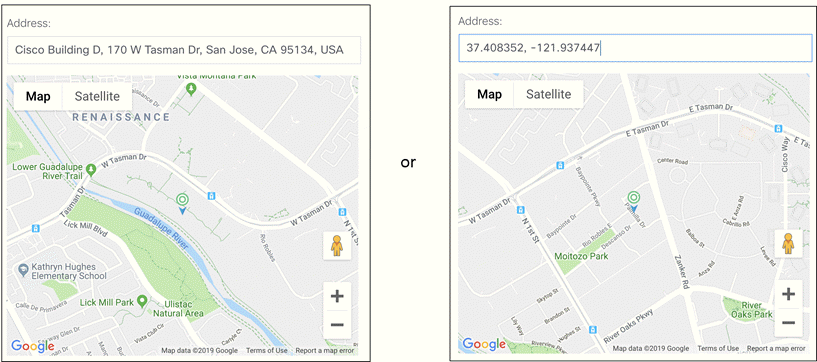
Previously, multiple fields were used, and accepted only addresses.
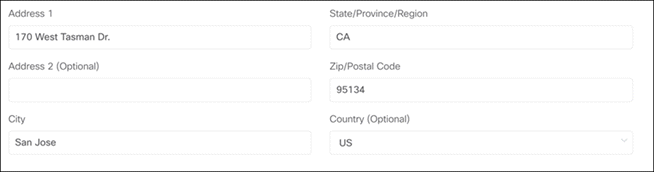
Bug fixes
- The fog app installation instance page now shows more than 100 gateways.
- Changes for customizing the columns in the gateways page now reflects immediately instead of having to wait for 30 seconds.
- Fixed an issue where data diagnostics logs were not showing up.
Updated April 18, 2019
Bug fixes
- Fixed the issue where firmware upgrade completion status was shown incorrectly after an upgrade was completed.
- Fixed issue where audit logs were not getting retrieved using API Key based authorization.
- Fixed the issue where the AP status was not shown correctly when a gateway was claimed while the AP state was in Unified mode.
### Updated April 11, 2019
New features
- Performance improvements were implemented in the gateway configuration background job to help speed up configuration changes across multiple gateways.
Bug fixes
- Site-2-site VPN status is now accurately displayed. This fix corrected an issue where the status was Up even if not configured on the gateway.
- Fixed an issue that prevented port forwarding from being reconfigured after a gateway reset and reboot.
Release 2.0.4
Updated April 4, 2019
New features
- You can now change the amount of time your session can be inactive before you are automatically logged out. Go to
 > Profile Settings > Session Timeout.
> Profile Settings > Session Timeout.
Bug fixes
- Gateways cannot be deleted when a firmware upgrade is scheduled. This fix displays the correct message if you attempt to do so.
- You can now select gateways from multiple pages to perform bulk actions.
Updated March 12, 2019
What's new in this release
A new "Reset Config" option is available to reboot the gateway, erase the current network configuration, and reconfigure the gateway based on the currently assigned template.
- Select Gateway > Gateways.
- Select a gateway.
- Click Diagnostics.
- Click __Refresh > Reset Config __.
See Diagnostic operations for more information.
Release 2.0.3
What's new in this release
Last updated December 20, 2018
If a gateway is claimed without an address, no default address will be entered and the field will be blank until an address is configured or the gateway's GPS is enabled.
Updated November 13, 2018
- Advanced Template
- Networking configuration
- AP can be managed using a Cisco Wireless LAN Controller
- LTE Throughput can be tested to identify cellular issues
- Dual LTE gateways can enable both SIMs
- LAN Ports can be enable or disabled individually
- APNs can be modified after the gateway is claimed
- New WiFi authentication and SSID options
- WiFi Authentication options for PSK and 802.1x
- SSIDs can be entered for each gateway after being claimed
- Updated menus for SSID Generation options
- Recovery Time
- Geo Fence
- Audit logs
- Firmware upgrade
- Alerts can now be sent by text message.
- Two Factor Authentication
- Customizable columns for gateway view
Advanced Template
Advanced templates allow you to apply additional Cisco IOS configurations to one or more gateways, and allows customization using variables provided in the template.
Advanced templates are reviewed and approved by Cisco for your organization.
For example, advanced templates allow a user to select variables definitions when claiming a gateway, permit incoming connections to IOx App port 9443 from WAN interface, or permit incoming network access from WGB network.
Note: Advanced template settings are only applied after the standard template settings are successfully configured on the gateway.
See Advanced templates for more information.
Networking configuration
APs can be managed using a Cisco Wireless LAN Controller
An Access Point (AP) Mode allows you to manage the WiFi AP and management configurations on IR829 gateways using a Cisco Wireless LAN Controller.
Notes:
- This feature is only supported on the IR829 gateways.
- The WiFi and WGB settings are not available when this "Unified Mode" is selected.
- Changes to the AP Mode or WLC IP addresses will trigger an AP reboot. This can cause wireless traffic downtime.
See AP Mode for more information.
LTE throughput can be tested to identify cellular issues
A new diagnostics option is available to test the throughput of a cellular connection, and can help discover where the connectivity is bad, such as signal strength or uplink bandwidth issues.
Go to Diagnostics > Test network > Test Throughput and enter an iPerf Server address to retrieve cellular throughput information.
You can host your own iPerf server (recommended) or use a public iPerf server.
See Diagnostic operations for more information.
Dual LTE gateways can enable both SIMs
Dual LTE IR829 gateway models can use both SIM slots for cellular traffic.
When enabled, both SIMs in a Dual LTE gateway are used at the same time. The following modes are supported:
- Default Load Balancing:
Cellular traffic is automatically balanced between the SIMs.
For example, see CEF per destination load balancing. - Custom Load Balancing:
Specify the subnet for traffic that will go out of SIM 1, as shown in the following illustration
For example, if you have a video server you can send all video traffic out of SIM1. All other traffic will go out of SIM 0.
See Dual LTE for more information.
Dual LTE Custom Load Balancing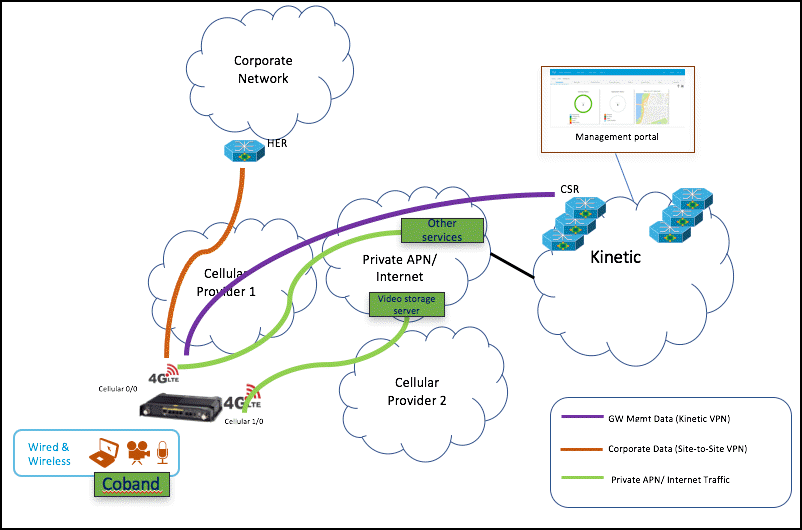
LAN Ports can be enabled or disabled individually
IR829 gateway models support multiple LAN ports, which can be enabled or disabled individually.
See LAN ports for more information.
APNs can be modified after the gateway is claimed
You can now change the APN settings after the gateway is claimed.
Note: Changing this setting can cause cellular traffic downtime.
See WAN Interface for more information.
New WiFi authentication and SSID options
Gateway WiFi configuration is enhanced to provide the following authentication and configuration options:
- Authentication options now include PSK (WPA-pre-shared key mode) and a WPA-802.1X mode that uses a RADIUS authentication server.
- Manual SSID configuration now includes a Custom option that allows you to enter an SSID in the gateways' network configuration settings after the devices are claimed (go to Gateways -> “Networking” Tab -> Advanced Configurations -> WiFi).
- The SSID Generation options are updated for clarity and to provide additional options.
See WiFi settings for more information.
Recovery Time
A new Recovery Time option allows you to select the amount of time that powered Gateways will wait after losing Kinetec connectivity before being automatically reset.
When Kinetic connectivity is restored, the gateway will be reconfigured to the factory settings.
See Recovery Time for more information.
Geo Fence
A GPS fence allows you to track when a gateway enters or leaves a geographic location. For example, a gateway installed in a truck can send an alert when the truck is within a mile of the shipping dock, or leaves that same area.
Geo fences are also displayed on the Dashboard map.
See Create a geo fence for more information.
Audit logs
Audit logs allow you to view the actions initiated by users, or that are system generated. For example, you can see which users modified a template, or when the system generated data for a device.
See Audit logs for more information.
Firmware upgrade
You can now use the Cisco Kinetic Cloud Application to upgrade gateway firmware.
Firmware upgrades available online and can be triggered manually, or scheduled for a future time. You can upgrade specific gateways, groups of gateways, or all gateways.
Notes
- The upgrade process takes up to 2 1/2 hours. The firmware image is first downloaded to the device and then installed. Note: Gateways will be reloaded and be offline during the upgrade process and unavailable for data delivery.
- Factory resetting a gateway restores the gateway to it's original firmware version.
See Upgrade gateway firmware for more information and to upgrade the gateway to the latest version.
Alerts can now be sent by text message
Alerts can now be sent by text message as well as email. Alerts can alse be sent for geo fence events, such as when a gateway enters or leaves a geo fence area.
See Alerts for more information.
Two Factor Authentication
Users can now enable 2-factor authentication, which allows them to generate a one-time login code that must be entered in addition to their password.
See Two Factor Authentication for more information.
Customizable columns for gateway view
Admin users can now hide or display columns in the gateway list view. All users in the organization will see the selected columns by default.
- Go to Gateway > Gateways.
- In the top right of the device list, click
 .
. - Select the columns you want to appear.
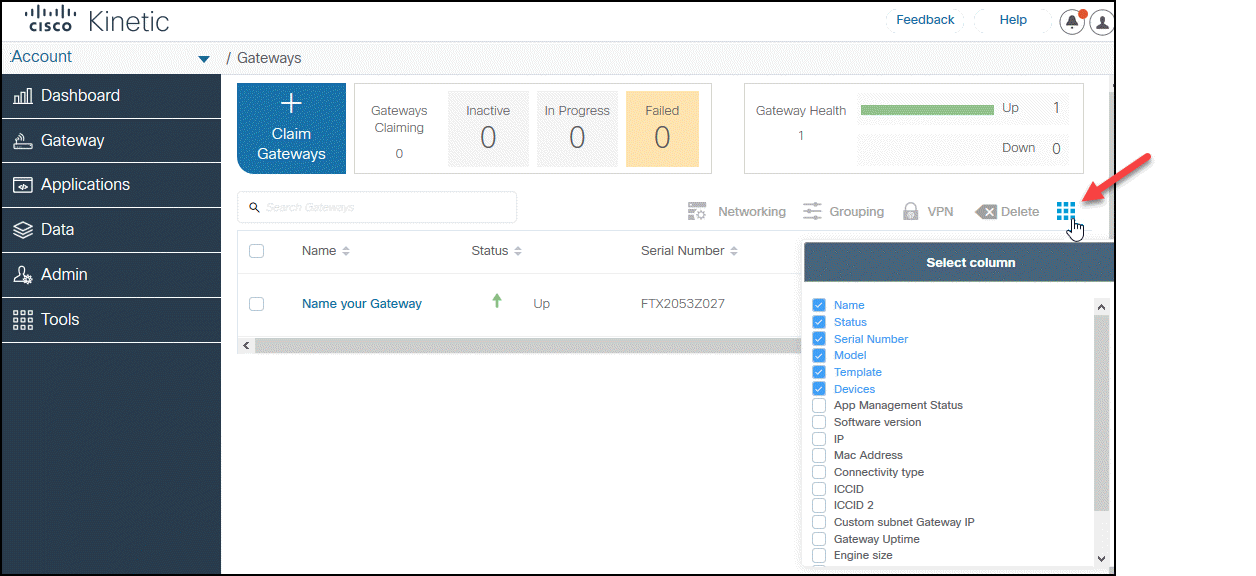
Release 2.0.2
Updated October 23, 2018
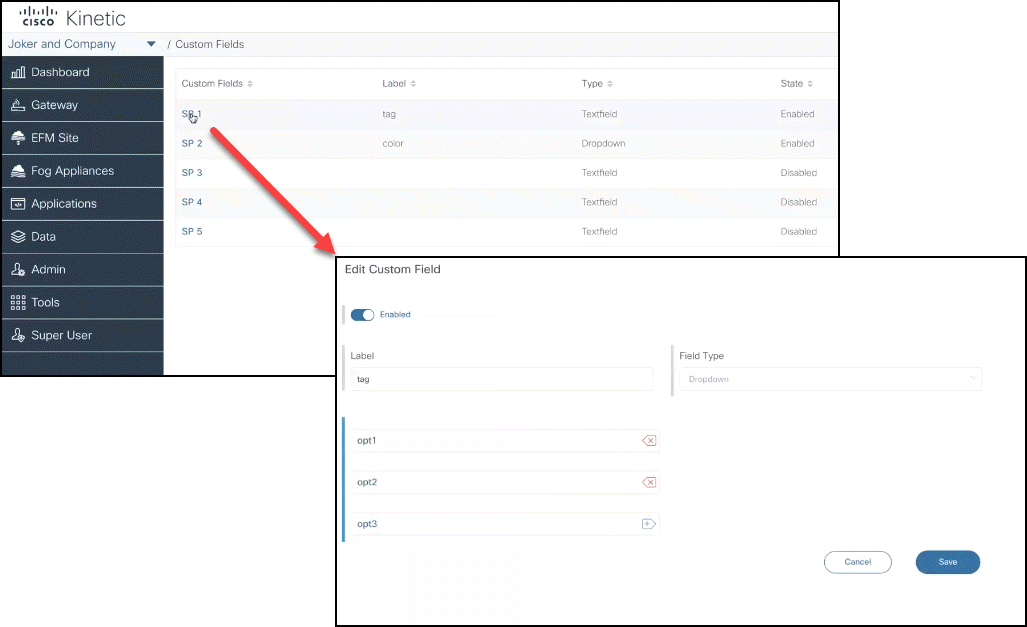
The UI was enhanced for the Gateway Custom Fields and Data Policy features.
Data Policy UI
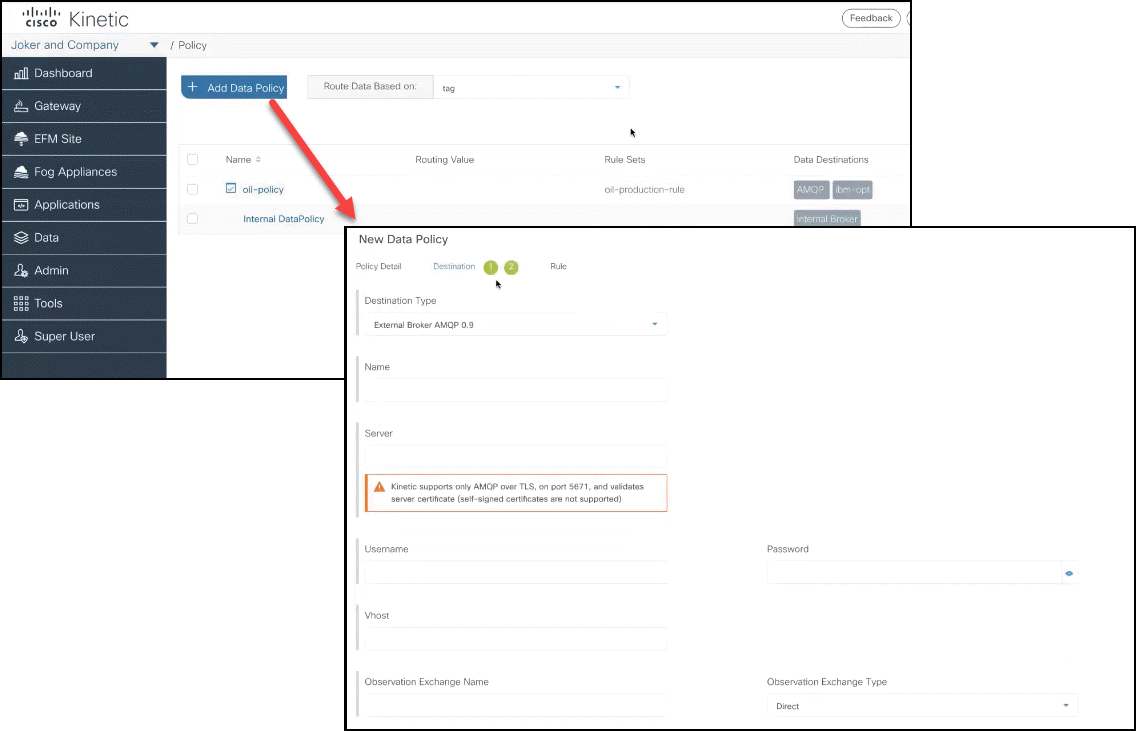
Custom Field UI
Updated September 6, 2018.
What's new in this release
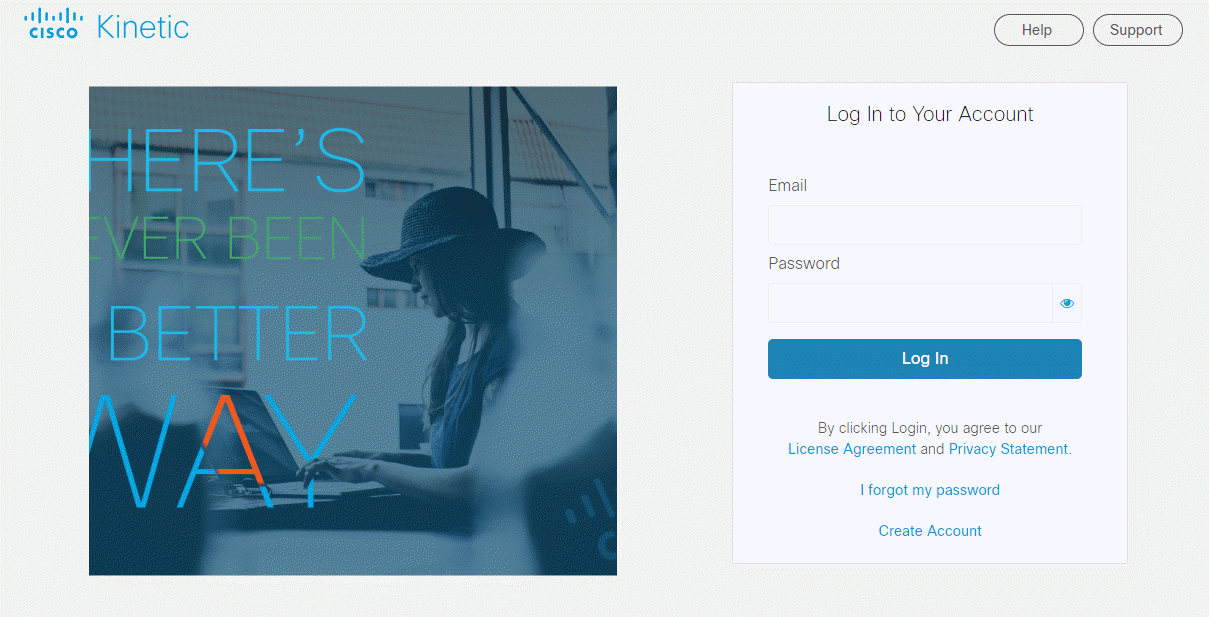
Login screen enhancements
An improved login screen provides quick access to Help and Support pages, and allows you to recover your password if necessary.
UI improvements
The Cisco Kinetic Cloud Application user interface includes a new color scheme and other enhancements for better accessibility.

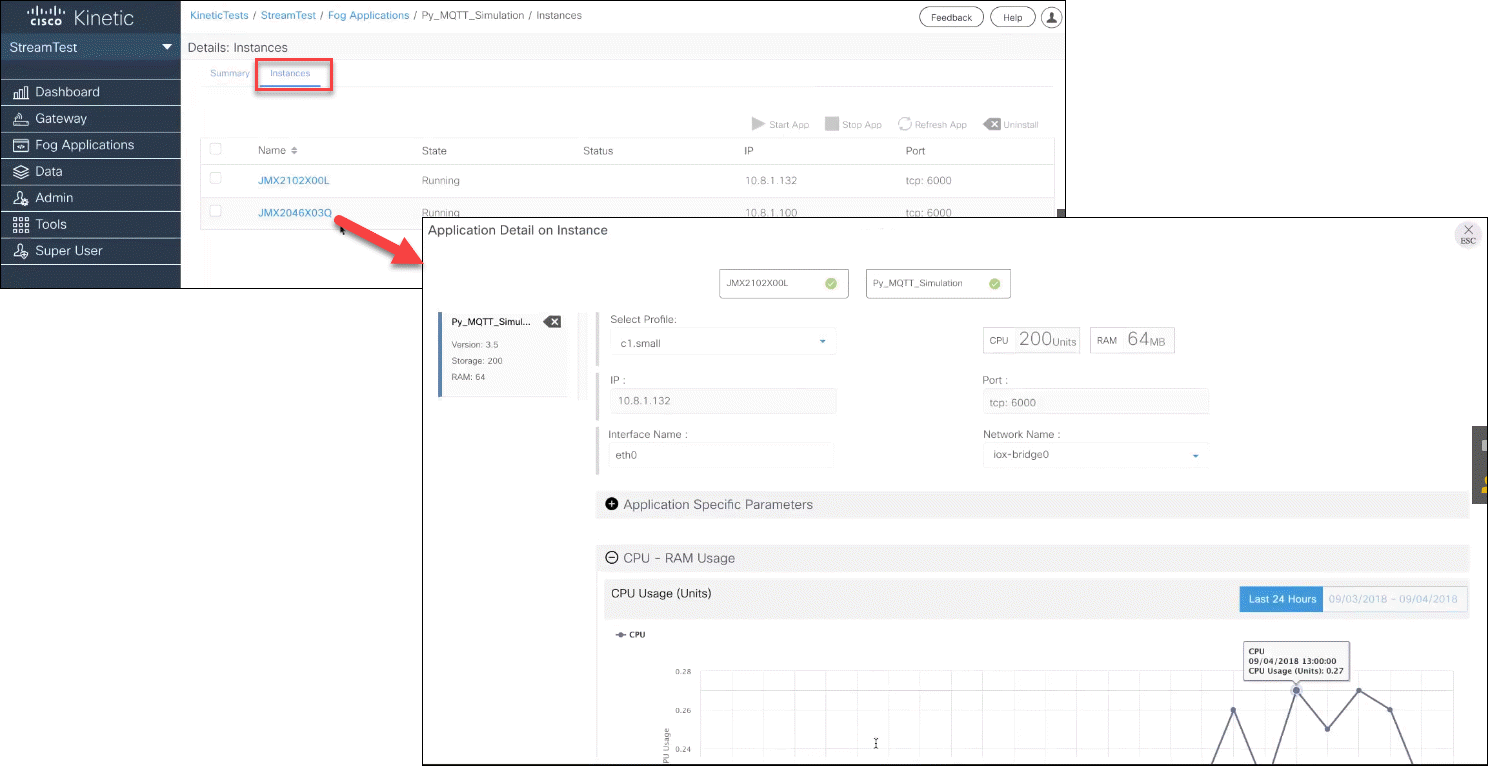
Fog application enhancements
Fog applications has been enhanced to include:
- An improved user interface that clearly presents information about the fog apps installed in your organization.
- A Summary tab that provides information about each installed fog app.
- An improved Instances tab that includes information about each gateway where the app is running. This now includes CPU and memory (RAM) usage for each instance.
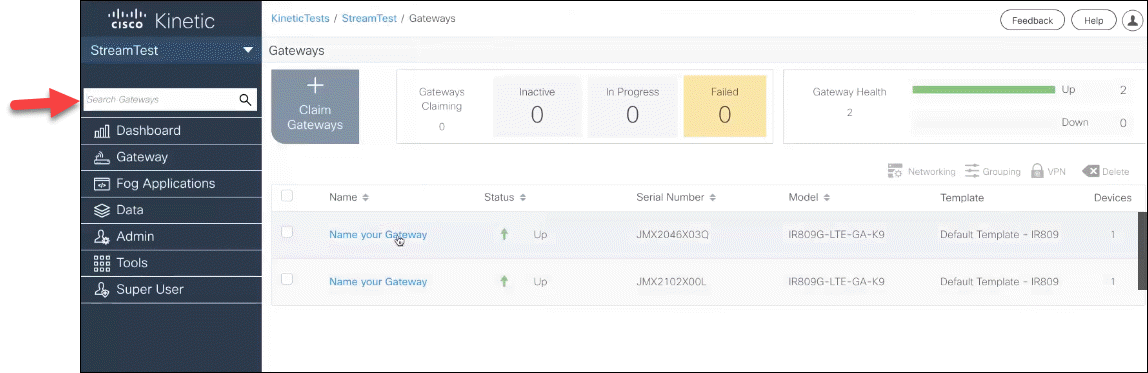
Additional gateway search results
Gateway searches now return results for additional fields, such as software version, iOS version, MAC address, IP address and other gateway fields, in addition to the device serial number, model, and other fields included in previous releases.
Release 2.0.1
Updated June 21, 2018.
What's new in this release
- Improved Help and Feedback menu
- Change your email and password
- Improved organization management menu
- GPS tracking up to 30 days
- Cellular usage tracking up to 30 days
- Firmware upgrade requests
- Site-to-Site VPN backup router
- Test broker connections
- Debug mode for IBM IoT destinations
- Event Log for IBM IoT destinations
- Telemetry data from the device SDK
- Open issues
- Fixed issues
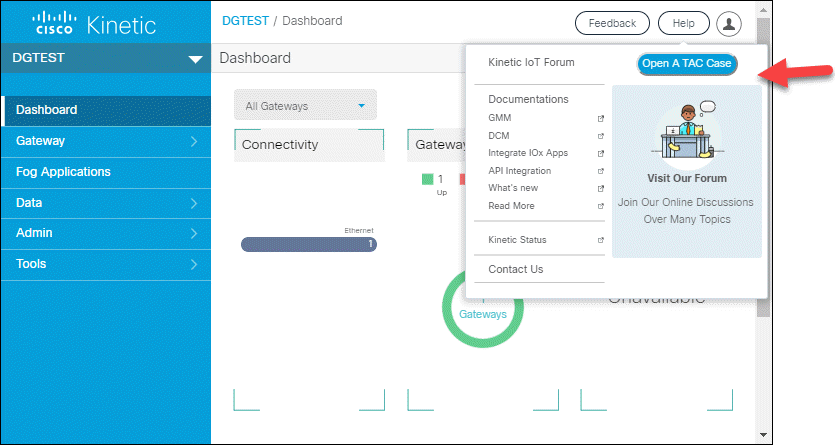
Improved Help and Feedback menu
The new Help menu in the top right provides quick access to help and support resources. For example, click help to access information and learning tools for the Kinetic modules, check the Kinetic cloud status or open a support case.
Click Feedback to let us know about your Kinetic experience and provide input for future enhancements.
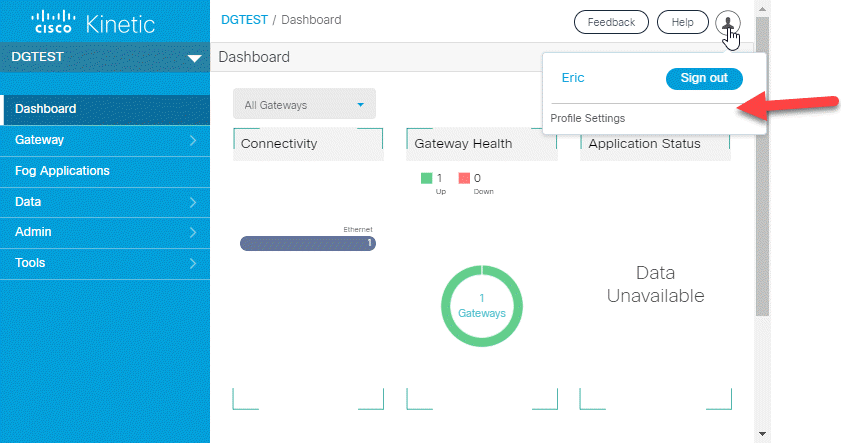
Change your email and password
A new profile icon in the top right allows you to change your password or update your email address.
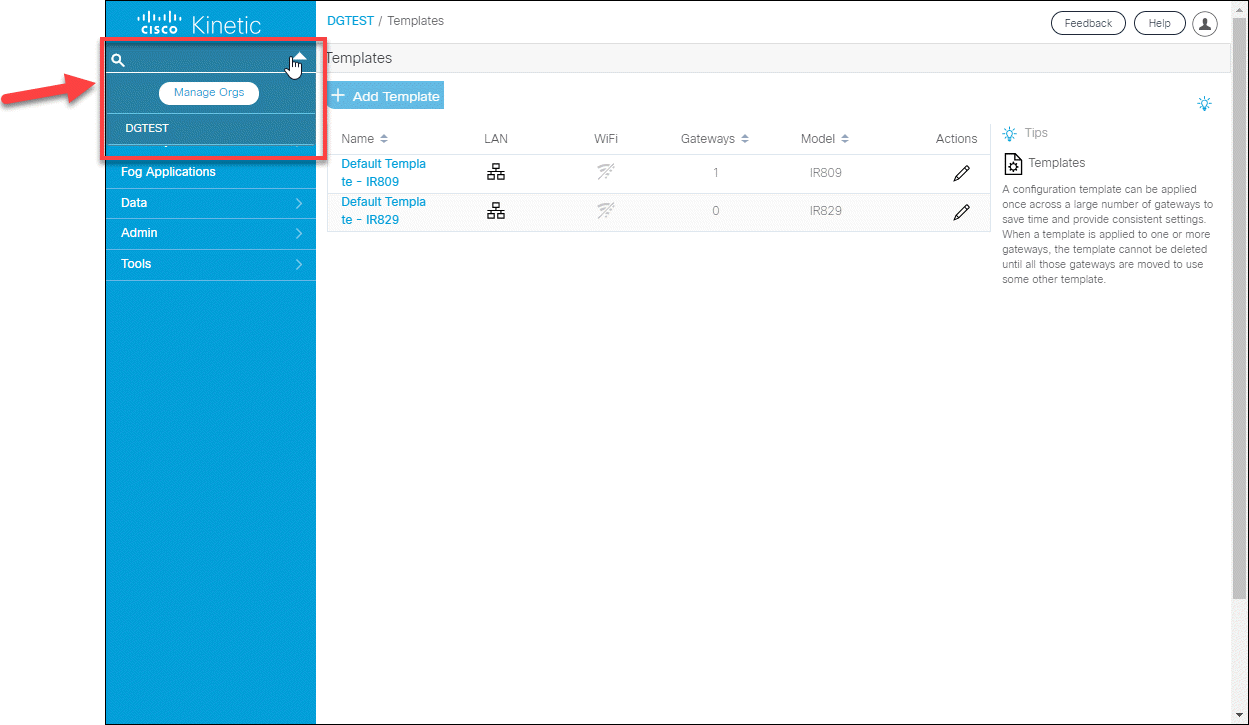
Improved organization management menu
Select and manage your organizations and accounts by expanding the menu at the current organization name.
GPS tracking up to 30 days
GPS tracking history is now available for up to 30 days.
To view the location of a gateway over the past 24 hours, click the GPS history option in the dashboard. GPS data is visualized in 1 hour trips.
Note: GPS must be enabled in the template associated with the gateway.
- Click the Dashboard tab to view a summary of gateway and application status.
- Select a gateway on the map.
- Click GPS history.
- In the Track for menu, select an hour to display.
- Select 24 hours, 15 days or 30 days of data.
- Select a date and time.
- Use the slider under the map to view the gateway location on the map for a specific time.
Notes
- GPS data is not displayed if the gateway does not have GPS enabled, or is stationary for the selected hour.
- Signal strength (RSSI) information is also displayed for the gateway, if available.
Cellular usage tracking up to 30 days
For cellular-enabled gateways, you can now view up to 30 days of data usage and signal strength history.
- Select Gateway > Gateways.
- Select a gateway name.
- Click Monitor.
- If the gateway uses a cellular connection, up to 30 days of data usage and signal strength can be displayed as graphs.
- Select 24 hours, 15 days or 30 days of data.
- Select a date and time.
Tip: Data usage and signal strength information is also displayed in the Dashboard.
Firmware upgrade requests
Gateway firmware upgrades are available as a managed service, which means you can request an upgrade for your devices, and a Cisco representative will contact you to arrange it.
Go to Tools > Firmware Upgrade to check if a firmware upgrade is available. If a message is displayed that a firmware upgrade is not available, then your gateways are running the latest version supported by Kinetic.
If a new firmware version is available, select the gateways to be updated and enter a description, such as the time and day you'd like to upgrade.
Click Send and a Cisco representative will contact you to coordinate and perform the upgrade.
Note: Gateways will be reloaded and be offline during the upgrade process.
Site-to-Site VPN backup router
Site-to site VPN connections can now use a second backup router, if necessary. If the first router is offline and the second one is used, the second router will continue to be used even when the first one comes back online. If the second server goes offline, then the first server will be used again.
See Site-to-site VPN for more information.
Test broker connections
You can now click Test Broker Connections to test that your data destination is successfully connecting to Cisco Kinetic.
The test option is available on:
- Internal Broker
- External broker AMQP 0.9
- IBM IoT
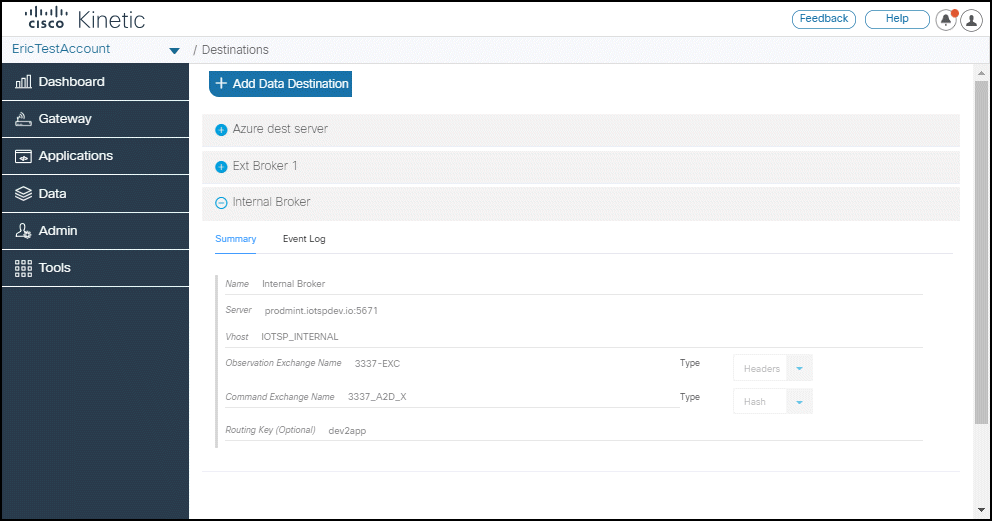
Note: This option is not supported for Microsoft Azure destinations.
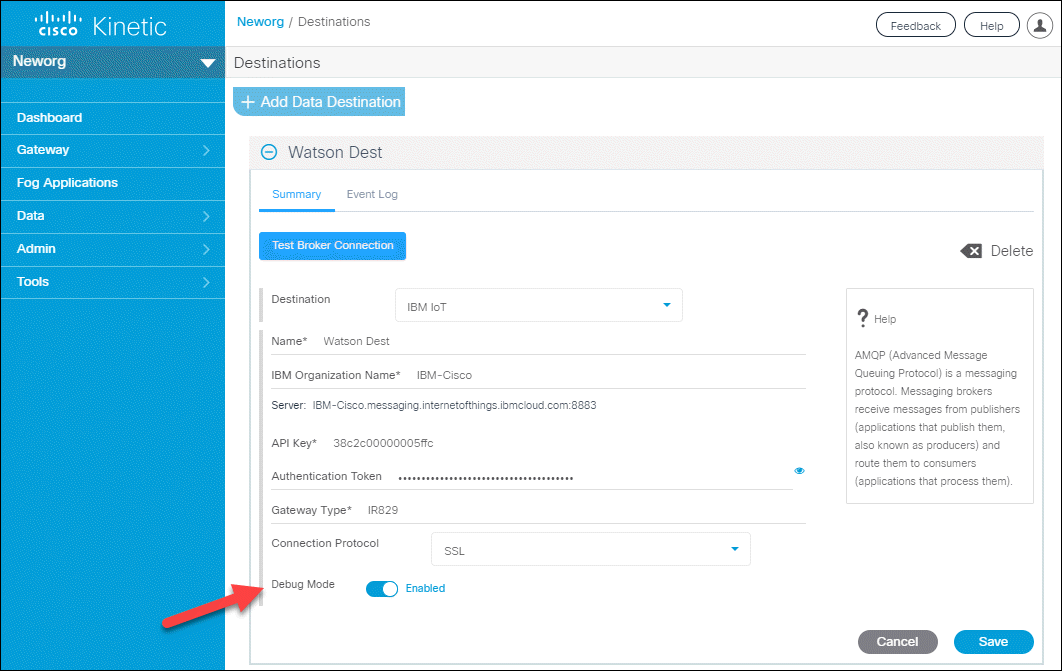
Debug mode for IBM IoT destinations
An optional debug mode can be used to include additional information along with the device data sent to IBM IoT destinations.
The debug mode includes the following timestamps:
- “dcm_received_at” — the timestamp, UTC, in milliseconds indicating when DCM received the data message.
- “dcm_sent_at” — the timestamp indicating when DCM published the message (to be sent to the destination).
To enable debug mode, select the Debug option when creating or editing an IBM IoT destination:
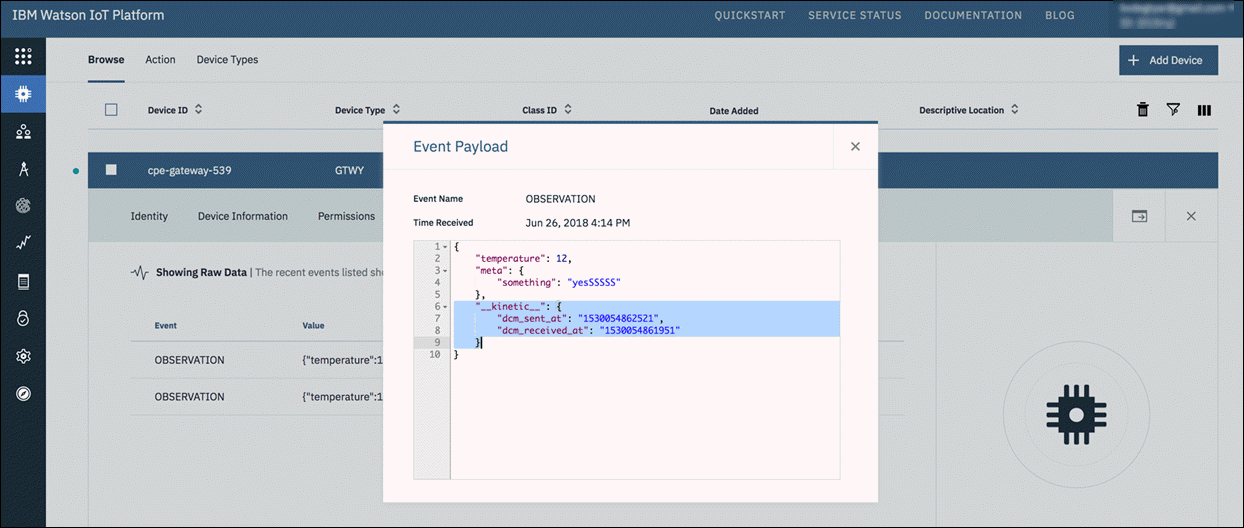
For example, when Debug mode is enabled, go to the IBM destination that is receiving Kinetic data, select Recent Events and then select an observation to view the event payload. The payload will include the debug timestamps:
Event Log for IBM IoT destinations
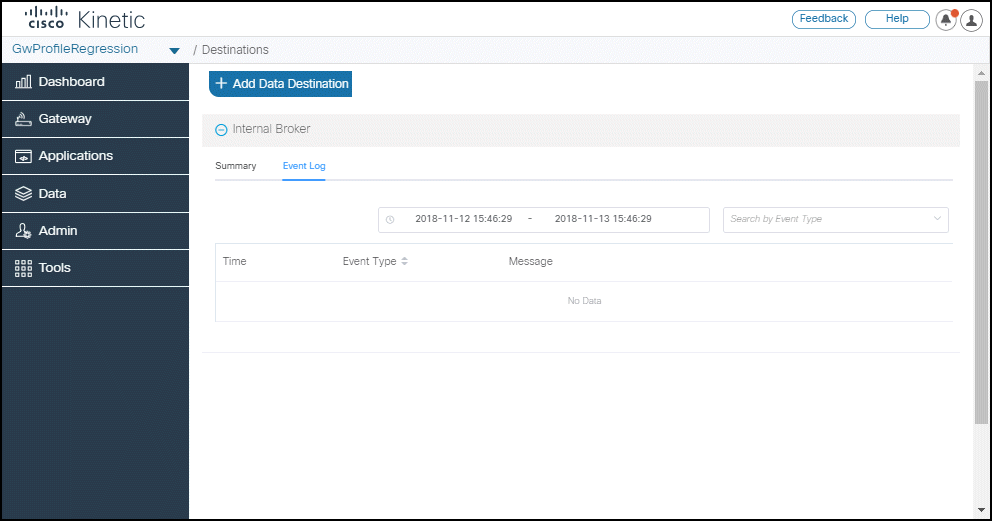
An event log is now available that shows the communication and data transfer events for IBM IoT data destinations.
- Go to Data > Destinations.
- Select or create an IBM IoT destination.
- Click the Event Log tab.
Telemetry data from the device SDK
The Kinetic SDK supports adding telemetry data to data messages.
To Turn on telemetry data, set the application configuration parameter "include_meta_data_with_msg" to "true".
For example, when using "CustomSSLMqttClient" in the SDK, set "include_meta_data_with_msg" to "true" in package_config.ini under the application section to obtain telemetry data.
If the regular "MQTTClientEdge" part of SDK is used instead of "CustomSSLMqttClient", use the helper class to obtain the payload and topic to publish. For example:
com.cisco.iot.swp.device.sdk.common.utils.HelperMethods.getPublishTopic(String topic, boolean useTelemetry, boolean isBatch)
com.cisco.iot.swp.device.sdk.common.utils.HelperMethods.getPublishPayload(String payload, boolean useTelemetry, String topicToPublish, String label, String deviceId, int QOS, boolean isBatch)See the sample usage for more information.
Usage information
- When the "include_meta_data_with_msg" flag is set to true, the actual message payload is sent with the telemetry data to the destination.
- For AMQP 0.9, the data can be expected in the following manner:
('Headers : ', {'dp_received_ts': u'1530143798459', 'sent_to_destination': u'1530143798632', 'route_version': u'v1', '__kinetic__app_sent_at': u'1530143798092', 'route': u'/v1/321:285961/json/dev2app/alertTemp', '__kinetic__dcm_received_at': u'1530143798229', 'gatewayId': u'321', 'message_direction': u'dev2app', 'tag': u'alertTemp', 'deviceId': u'285961', 'content_type': u'json', 'assetName': u'assetpi', 'accountId': u'853', 'device_id': u'285961'})- For IBM destinations, telemetry is added into the payload under the key "kinetic":
{
"actual data" : "not touched"
"__kinetic__": {
"dcm_sent_at": "1530144426872",
"dcm_received_at": "1530144426530",
"app_sent_at": "1530144426286"
}
}Open Issues
| Jira # | Description | Workaround |
|---|---|---|
| 21108 | Initial WGB and Wifi configuration may fail and eventually recover. | None. It will auto-recover |
| 21505 | DHCP / BOOTP Issues with PLC | Raise a support request or email ciscokinetic.io-support@cisco.com for assistance related to this issue |
Fixed Issues
Issues resolved in this release:
| Jira # | Description |
|---|---|
| IOTSP-24343 | Remote Access to new gateways not working for certain existing users |
| IOTSP-24634 | Gateway unclaim and down alerts to be made gateway specific |
| IOTSP-25396 | Getting the max alert email without max number of alerts being generated within a day |
Release 1.5.3
Updated May 17, 2018.
What's new in this release
May 17, 2018 updates
The Dashboard map can now be expanded to fill the entire window.
Users can zoom in and out of the Dashboard map using their keyboard and mouse.
- Cmd + scroll on a Mac
- Ctrl + scroll on a Windows PC
May 03, 2018 updates
Gateway Diagnostics
Admin users can perform the following diagnostic operations on their organization's claimed gateways.
- Connectivity with Kinetic—Click Gateway or App Infra to verify that the gateway and apps can communicate with Cisco Kinetic.
- Test network—Use ping and trace route commands to verify connectivity from the gateway to a different IP address. See below for more information.
- Show Commands—Run a set of pre-defined show commands in the gateway that display information about the device.
- Debug Commands—Retrieve the syslogs, clear the syslogs, enable/disable additional debugging on the gateways.
- Refresh—Reboot the gateway, reboot the access point (AP) for IR 829 gateways, and refresh the app management state (this forces Kinetic to resync with the IOx apps running the gateway.
See Diagnostic operations for more information.
Alerts
Alerts can be configured for different topics and for a specific gateway to notify Kinetic users about user actions and unexpected gateway and application events.
In this release, alerts are logged in the system and can also be delivered by email. Emails are sent as soon as the alerts occur, or after a specified delay.
Note: To avoid excessive alert emails, carefully select alert topics and gateways. The current release will generate a maximum of 50 alert emails within a 24 hour period to avoid spamming users with too many messages.
Alerts can be generated when:
- Network Alerts—A network error or configuration occurs.
- Reboot Alerts—A gateway is rebooted.
- Gateway Health—The gateway state changes, a template is changed, a gateway is claimed or deleted, and other gateway events.
- App Management—An app is added, installed stopped, started, etc.
- Cellular Activity—A SIM card is removed from a dual LTE gateway.
See Create alerts for more information.
Reports
Admin users can configure reports for specific gateways that capture system data and metrics. Reports can be generated one-time (non-recurrence) or periodically (recurrence).
For example, the Cellular Usage report provides information about the gateways' signal strength and cellular usage. The Inventory report includes detailed information about the gateway device attributes.
In this release:
- Reports are generated in the csv format.
- Reports can be generated for the gateway inventory and cellular usage.
- The gateway inventory report, provides a snapshot of the gateways and it’s attributes at the time of the report was generated.
- The cellular usage report provides the cellular usage and signal strength information for 24 hours prior to the report generation time.
See View reports for more information. for more information.
GPS History
To view the location of a gateway over the past 24 hours, click the GPS history option in the dashboard. GPS data is visualized in 1 hour trips.
GPS must be enabled in the template associated with the gateway.
- Click the Dashboard tab to view a summary of gateway and application status.
- Select a gateway on the map.
- Click GPS history.
- In the Track for menu, select an hour to display.
- Data is available from the past 24 hours.
- Use the slider under the map to view the gateway location on the map for a specific time.
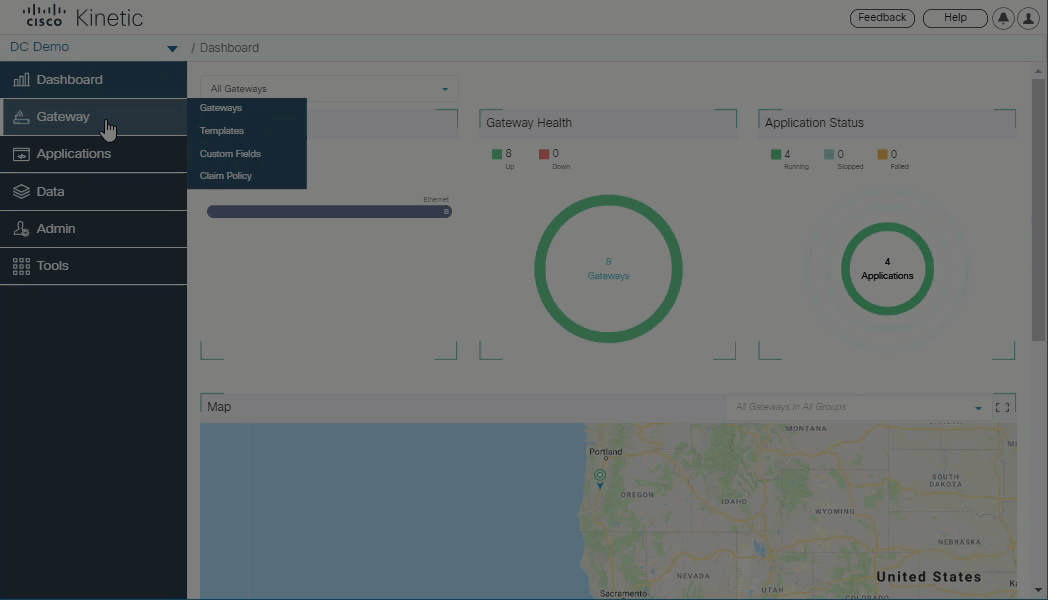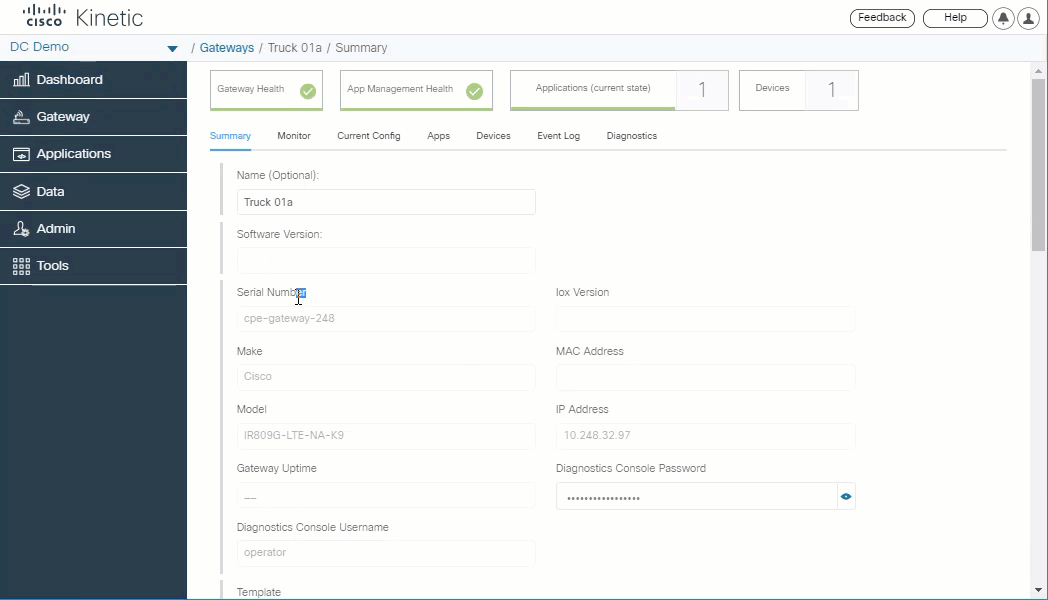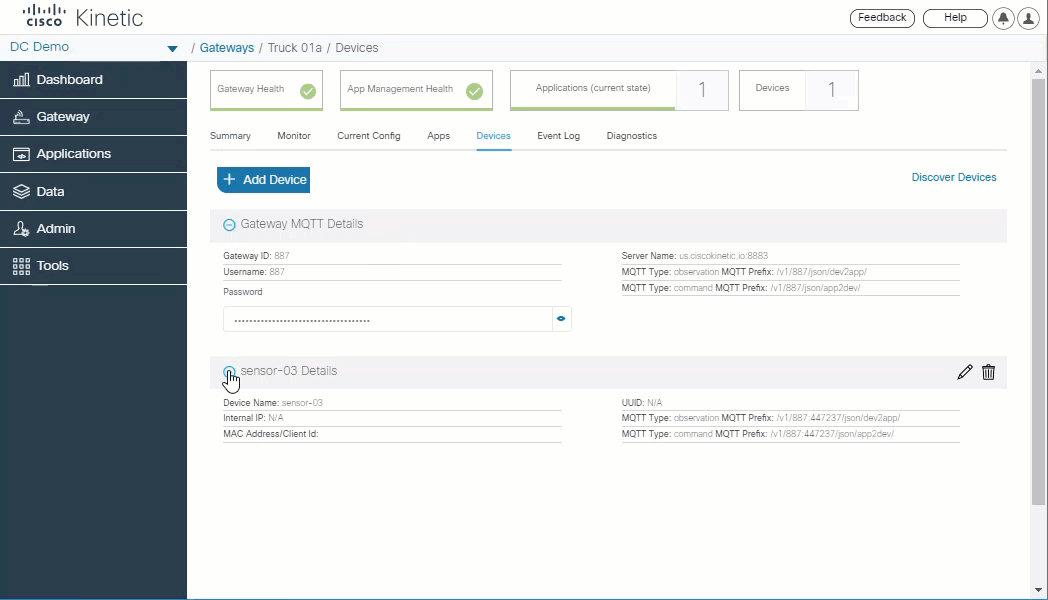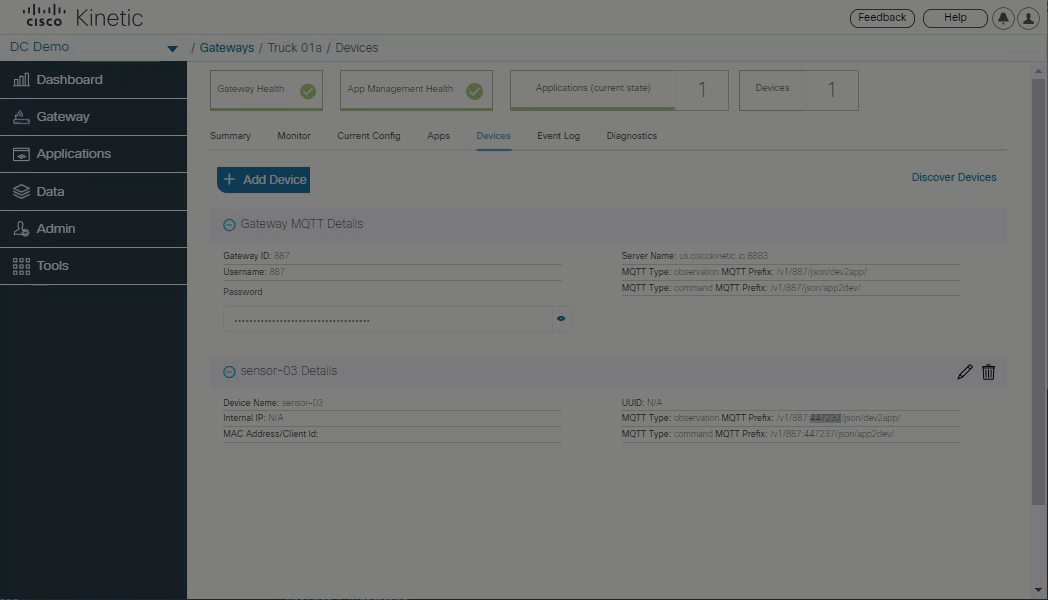
Notes
- GPS data is not displayed if the gateway does not have GPS enabled, or is stationary for the selected hour.
- Signal strength (RSSI) information is also displayed for the gateway, if available.
GPS troubleshooting
If the GPS history does not show data:
- Verify that GPS is enabled on the gateway at Details > Current config.
- If GPS is not enabled, verify that the template associated with the gateway has GPS enabled.
- Change the gateway template to one that has GPS enabled, if necessary.
- Verify that the correct GPS antennas are attached to the gateway.
See View gateway location history for more information.
Gateway diagnostics menu
A new gateway Embedded Menu Manager (EMM) menu is available to run predefined IOS commands for troubleshooting and device status. This menu is accessed using an SSH connection between the gateway and a computer.
Notes
- This feature is available only on gateways ordered or provisioned with the Kinetic release 1.5.3 or later. See Provision a gateway to update a gateway to the latest release.
- Kinetic gateways also support direct access to the console IOS CLI.
Procedure
Connect to the gateway using a USB cable or a VPN connection:
- Option 1: Connect a USB cable from your computer to the gateway console port.
- Option 2: Use a VPN connection between your computer and the gateway. See Remote management for instructions.
Launch an SSH client on your computer.
In the SSH client, enter the gateway IP address.
Enter the default username: operator.
Enter the password:
If the gateway is not claimed in the Kinetic admin console: operator.
If the gateway is claimed, go to Gateway > Gateways, select a gateway and click the Summary tab. Enter the password displayed for the Diagnostics Console.
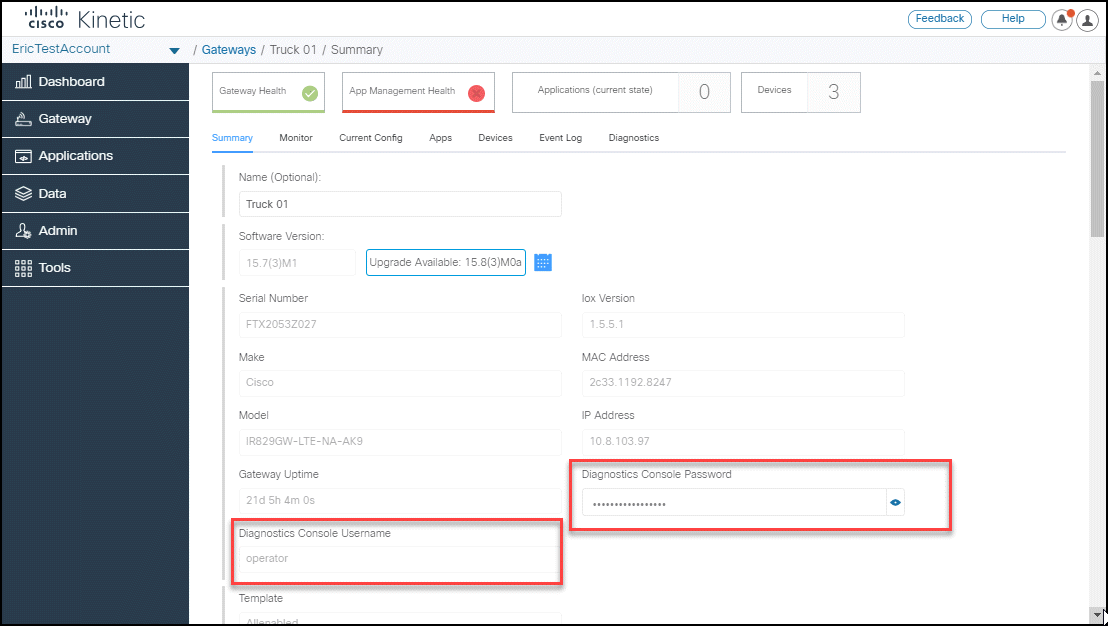
Connect to the device.
Enter a number for one of the predefined Cisco IOS commands, and press Enter.
Follow the onscreen prompts for additional options, if necessary.
See Gateway diagnostics menu (EMM) for more information.
Applications management enhancements
- The Applications screens were updated for improved usability and to provide additional app information.
- Increased the maximum size of the fog application that can be uploaded to Cisco Kinetic from 280 MB to 512 MB.
Open Issues
| Jira # | Description | Workaround |
|---|---|---|
| 21108 | Initial WGB and Wifi configuration may fail and eventually recover. | None. It will auto-recover |
| 21505 | DHCP / BOOTP Issues with PLC | Raise a support request or email ciscokinetic.io-support@cisco.com for assistance related to this issue |
Fixed Issues
Issues resolved in this release:
| Jira # | Description |
|---|---|
| 21168 | The VPN configuration may fail if the name-server table is full. |
| 21626 | The Fog Application page may not display the applications. |
| 18214 | Status for Site To Site Tunnel may show "Down" incorrectly even when the tunnel is up. |
Release 1.5.2
Last updated March 22, 2018.
What's new in this release
This release includes the following new features and enhancements.
March 22, 2018 updates
- Increased the maximum memory that can be allocated while installing a fog application on a gateway from 512 MB to 768 MB.
- Increased the maximum size of the fog application that can be uploaded to Cisco Kinetic from 95 MB to 280 MB.
- Fixed an issue that occurred when updating a gateway with any address from Germany.
February 23, 2018 updates
- A cellular usage bandwidth chart was added to the dashboard.
- Templates can now be edited even if they are already associated with gateways. Changes to an existing template are applied to any associated gateways.
February 6, 2018 updates
Support for custom subnets
A custom subnet can now be used to configure unique subnets across multiple gateways and advertise routes directly using IKEV2.
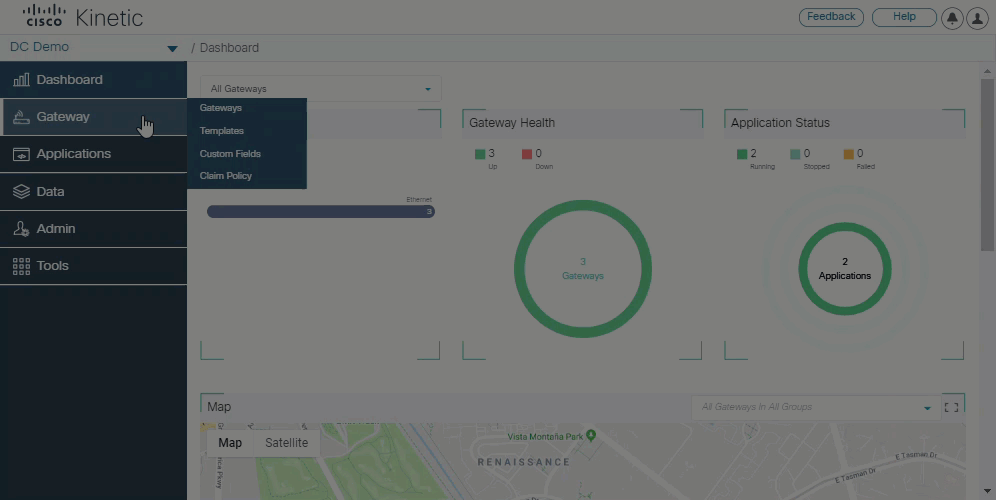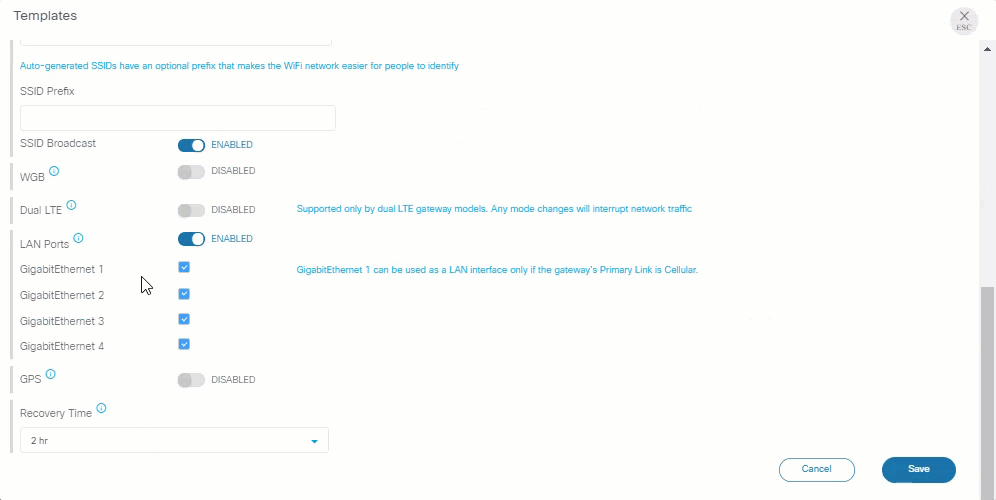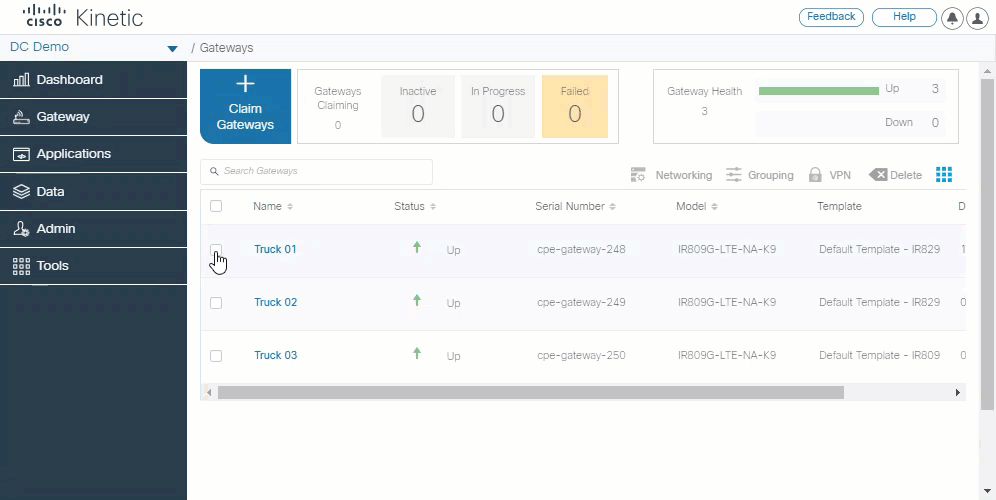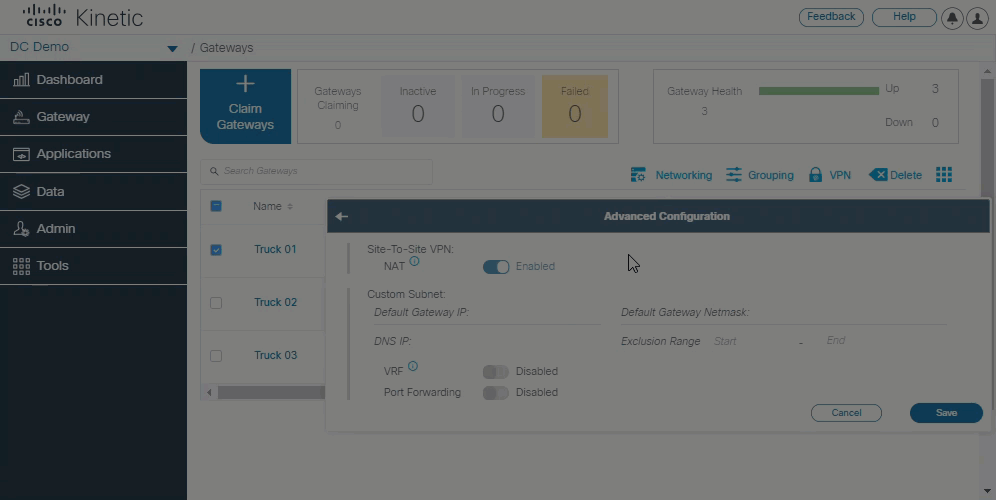
New Networking menu
A new Networking menu allows you to change a gateway's template or configure a Private Subnet. The Private Subnet settings are available only if the device template is configured with the Advanced option (see above).
Virtual Route Forwarding (VRF)
The Virtual Route Forwarding feature can be used to create a separate routing instance for destination that overlaps with the Kinetic Infrastructure. Enable this feature if your destination networks for subtended devices overlaps with the 10.0.0.0/16 and 10.7.0.0/16 network.
Gateway diagnostics
The new diagnostics feature provides information about a gateway, including output from a predefined set of show commands and connectivity with the Kinetic cloud.

- Select Gateway > Gateways.
- Select a gateway.
- Click Diagnostics.
- Click a button to run the predefined diagnostics:
- Connectivity with Kinetic—Click Gateway or App Infra to verify that the gateway and apps can communicate with Cisco Kinetic.
- Show Commands—Click Run to run a set of show commands that display information about the device.
- Refresh—Click Refresh App Management refresh the app management state.
Tip: Click Export to download a text file with the diagnostic results.
Improved Dashboard
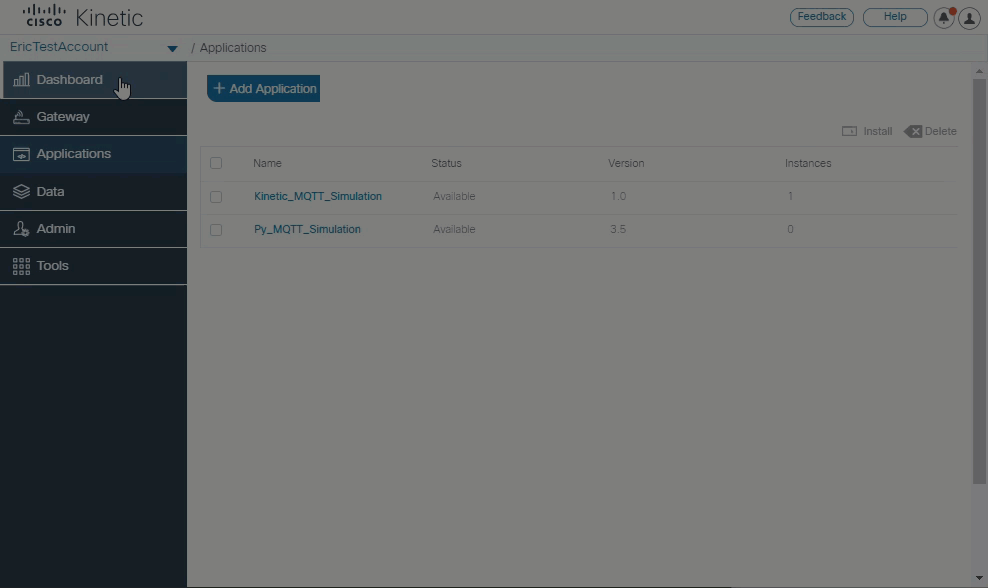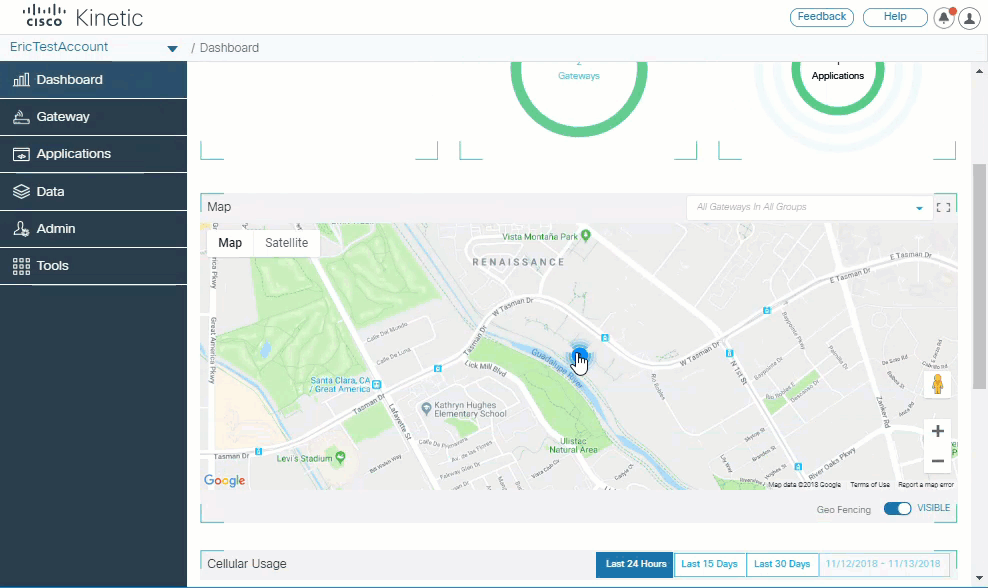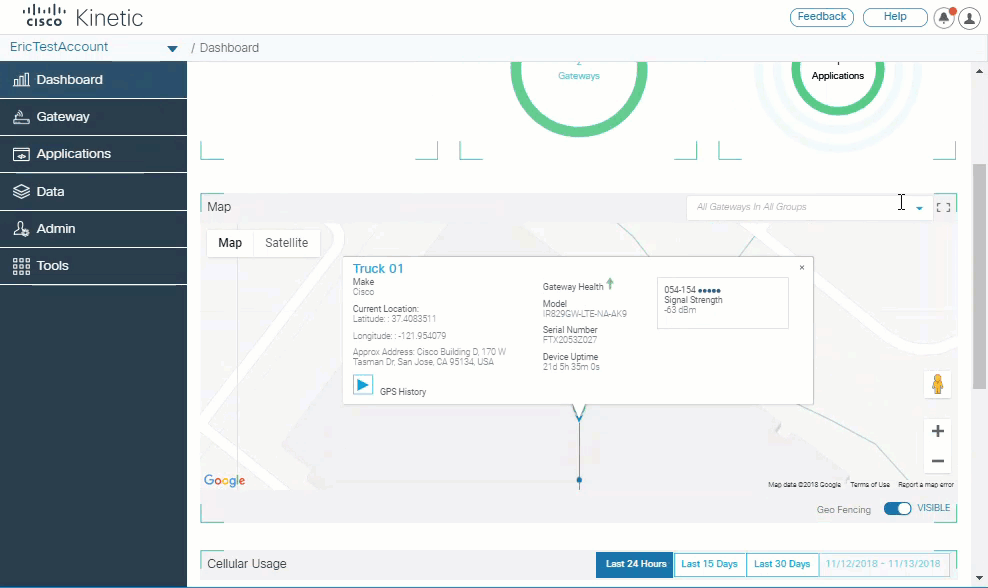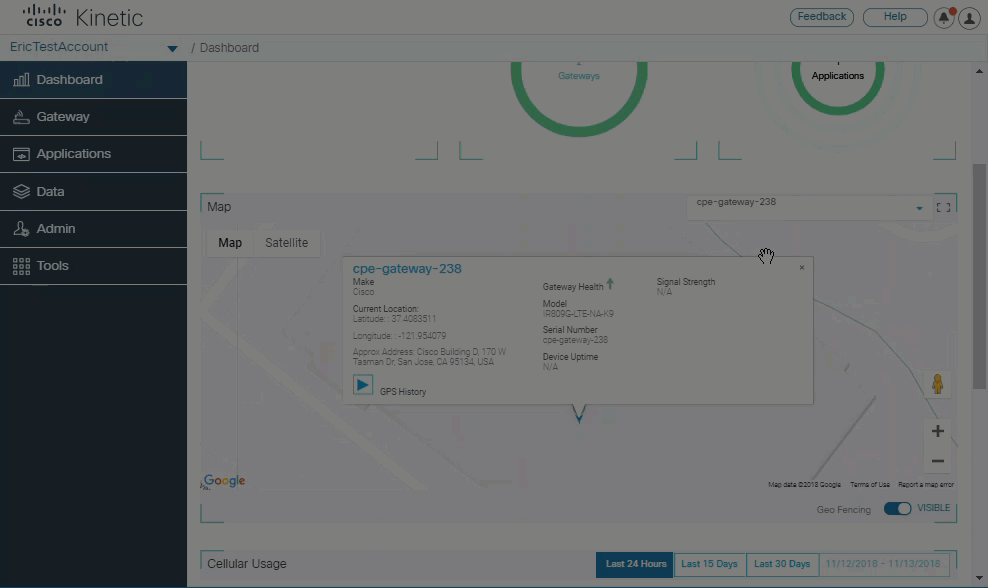
An improved Dashboard displays a summary of device health, and allows you to view the location and details of gateways on a map.
Kinetic Data Control Module (DCM) now supported
The Kinetic Data Control Module (DCM) is no longer in beta. This includes the Fog Applications and Data options in the Kinetic admin console.
Open Issues
| Jira # | Description | Workaround |
|---|---|---|
| 18214 | Status for Site To Site Tunnel may show "Down" incorrectly even when the tunnel is up. | None. Wait 15-30 minutes for the status to be updated. |
| 21108 | Initial WGB and Wifi configuration may fail and eventually recover. | None. It will auto-recover |
| 21505 | DHCP / BOOTP Issues with PLC | Raise a support request or email ciscokinetic.io-support@cisco.com for assistance related to this issue |
Fixed Issues
Issues resolved in this release:
| Jira # | Description |
|---|---|
| 21168 | The VPN configuration may fail if the name-server table is full. |
| 21626 | The Fog Application page may not display the applications. |
Release 1.5.1
Last updated January 2, 2018.
What's new in this release
This release includes the following new features and enhancements.
Support for the Kinetic Gateway Management Modules
The Internet of Things (IoT) allows enterprises to gain unprecedented visibility into the status and performance of their operations. As more sensors and machines get connected to the network, companies seek to get maximum value from their IoT data. IT and OT systems struggle to manage the expanding network while efficiently delivering data to applications. The Cisco Kinetic platform helps companies address these challenges.The platform includes the following cloud-based modules:
- Gateway Management (GMM)—Deploy and manage your Cisco gateways from a remote location and access devices over a secure VPN connection.
- Data Control (DCM)—Transform and filter sensor data, and send the results to the cloud and/or other destinations, according to policies set by the data owner.
Improved user interface
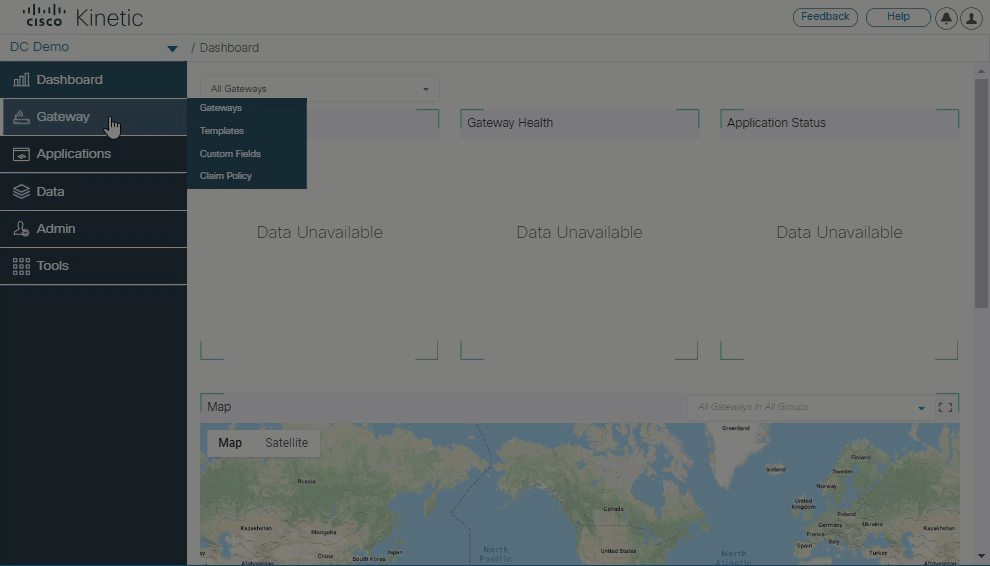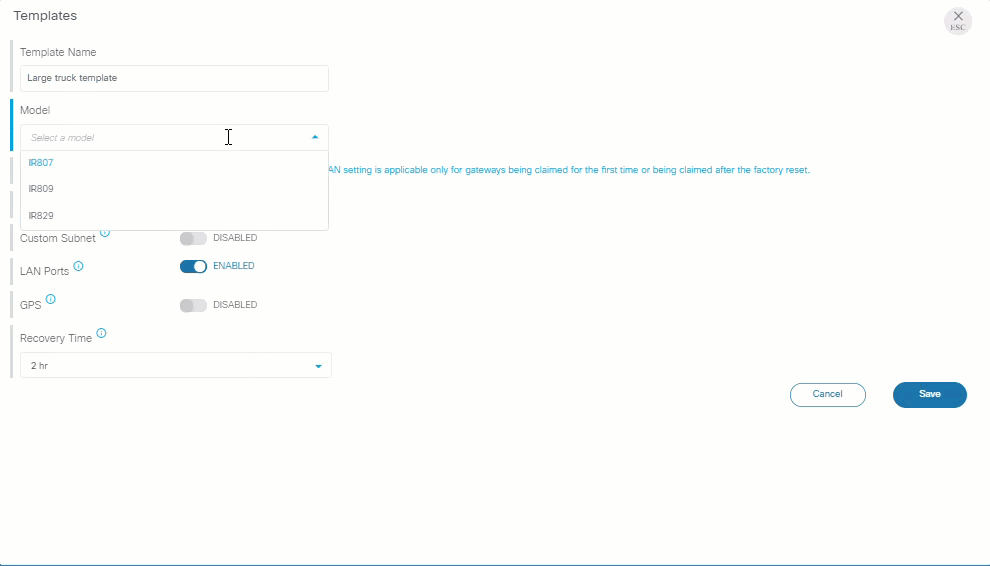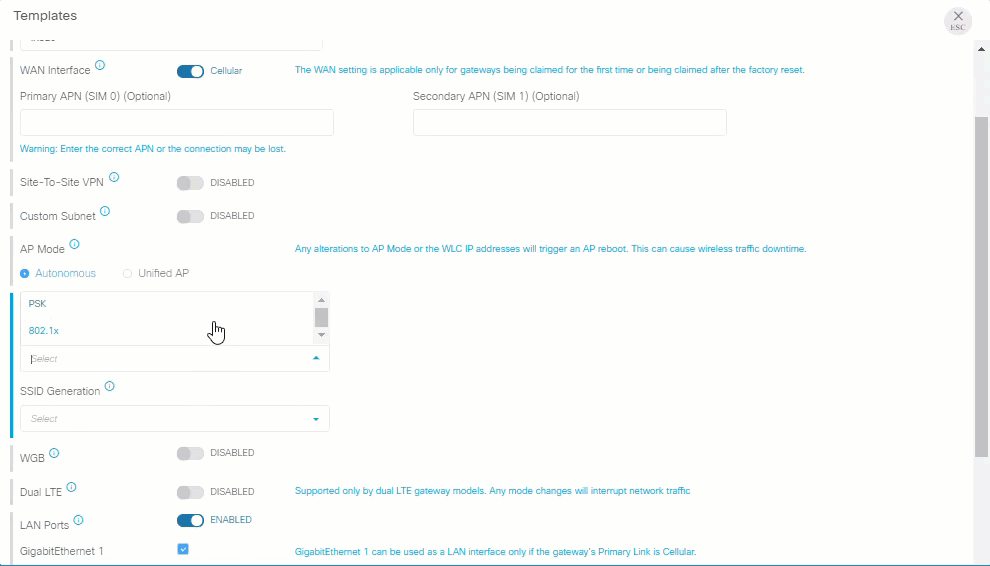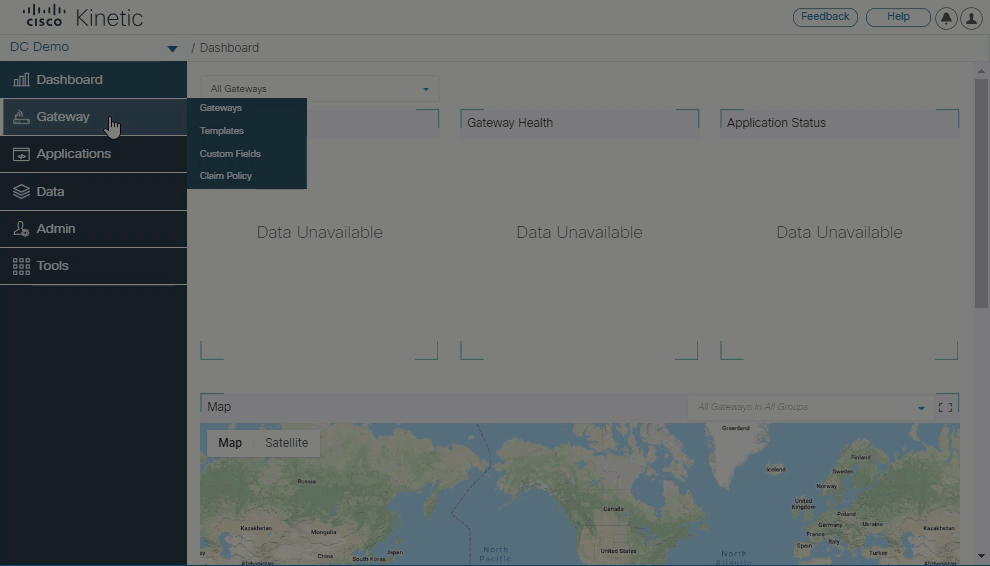
The Kinetic admin console user interface has been redesigned for easy of use and improved workflow. Main menu selections are now on the left. Roll your mouse over a menu to select additional options. Common tasks such as claiming a gateway have been streamlined and improved.

Simplified templates for network settings
Templates (previously "Configurations") define only the gateway's network setup. Devices and apps can be optionally configured. You can create multiple templates and select them when claiming a device, or use the default template.
The default template can also be defined using the new Claim Policy feature.
See Gateway Templates for more information.
Enhanced gateway claim flow
Claiming a gateway is easier than ever using the new claim flow, which leads you through the process on claiming a device for your organization. Select custom field definitions and then select or create a template. Templates include only network settings allowing Kinetic GMM module users to apply only the network configuration template, while Kinetic DCM users can also add fog apps and devices.
See Claim your gateways for more information.

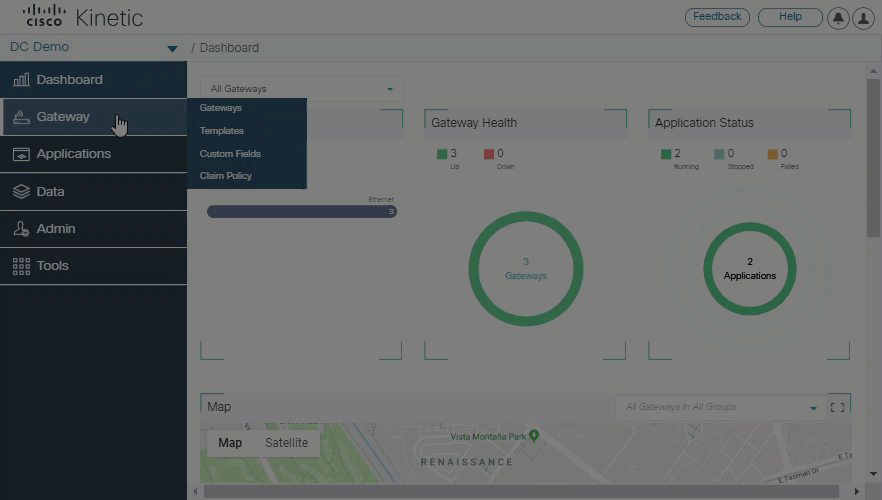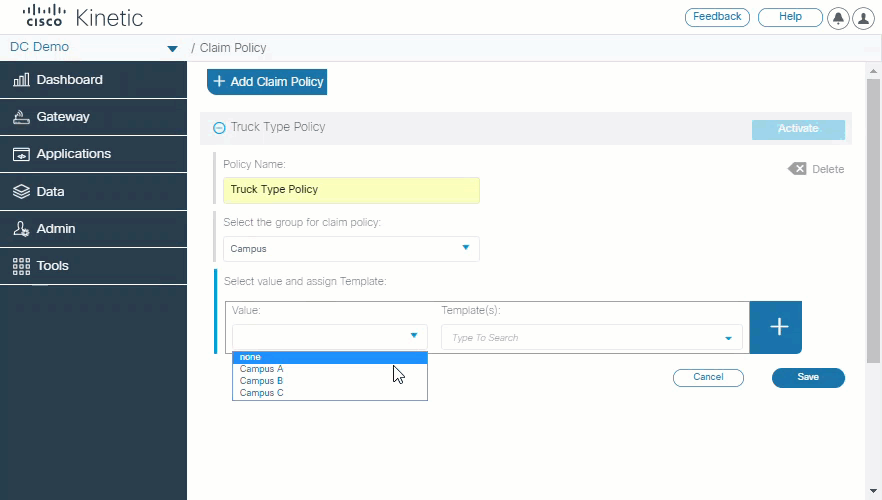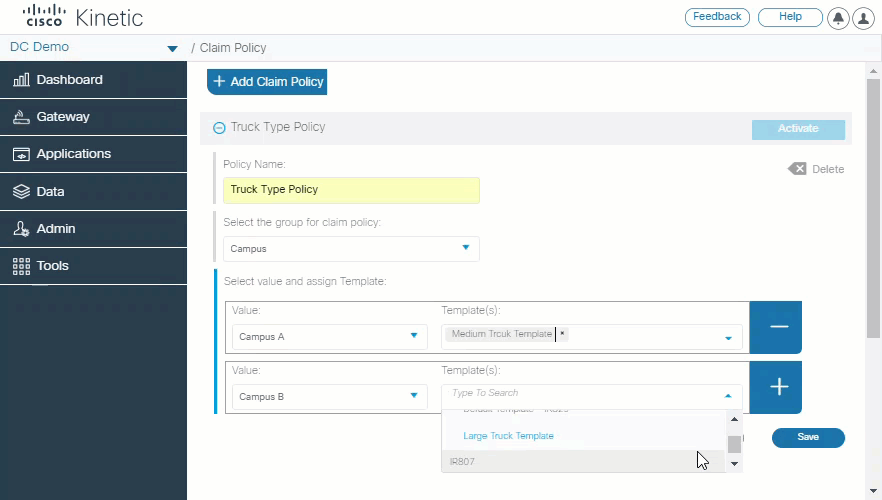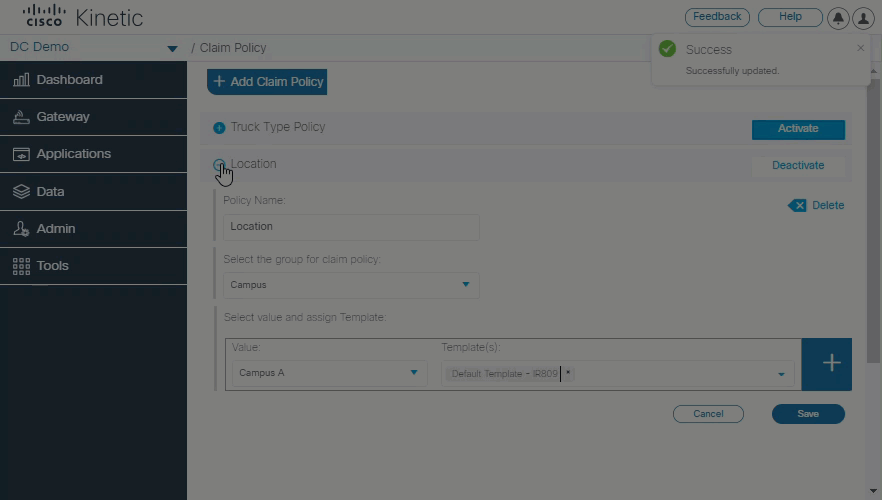
Define the default template
A new Claim Policy allows you to define different default templates based on the custom field definition for a device.
For example, when claiming gateways, all devices for Cummings trucks will use template "LAN and WiFI" by default, but Detroit trucks will use template "GPS and WiFI".
This can speed up the task of claiming devices since your can claim gateways without having to select a template. You can always select or create a different template, if necessary. If the custom field definitions do not match the active Claim Policy, the the system default template is used.
See Define the default template for instructions.
Grouping gateways
A new Grouping feature allows you define the custom field definitions for multiple gateways. This allows you to group gateways according to their use, location, or any criteria your define. This makes it easier to search for gateways.
See Group your gateways for instructions.

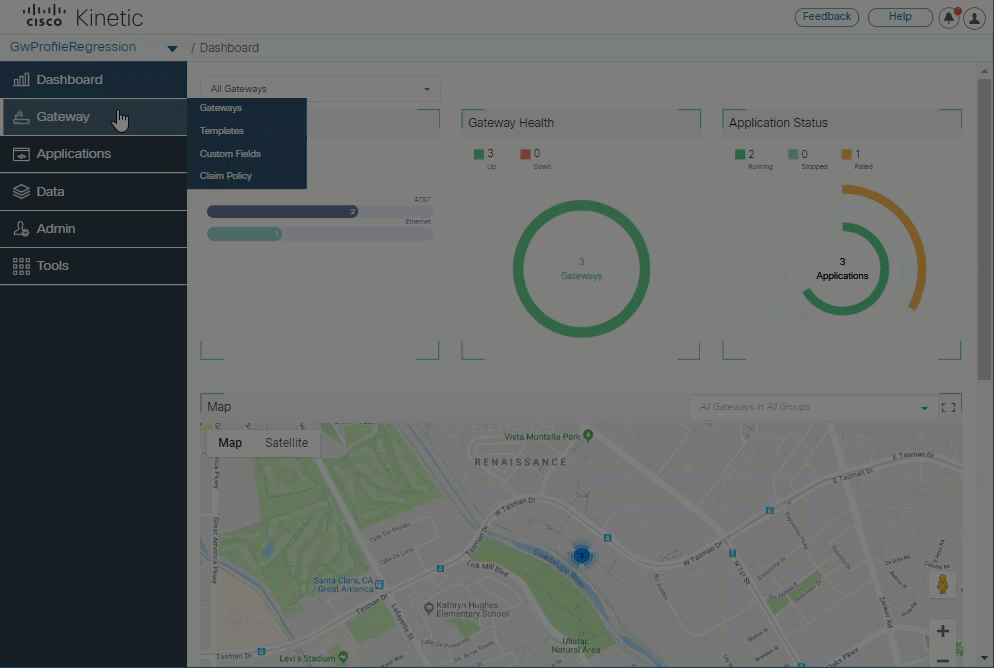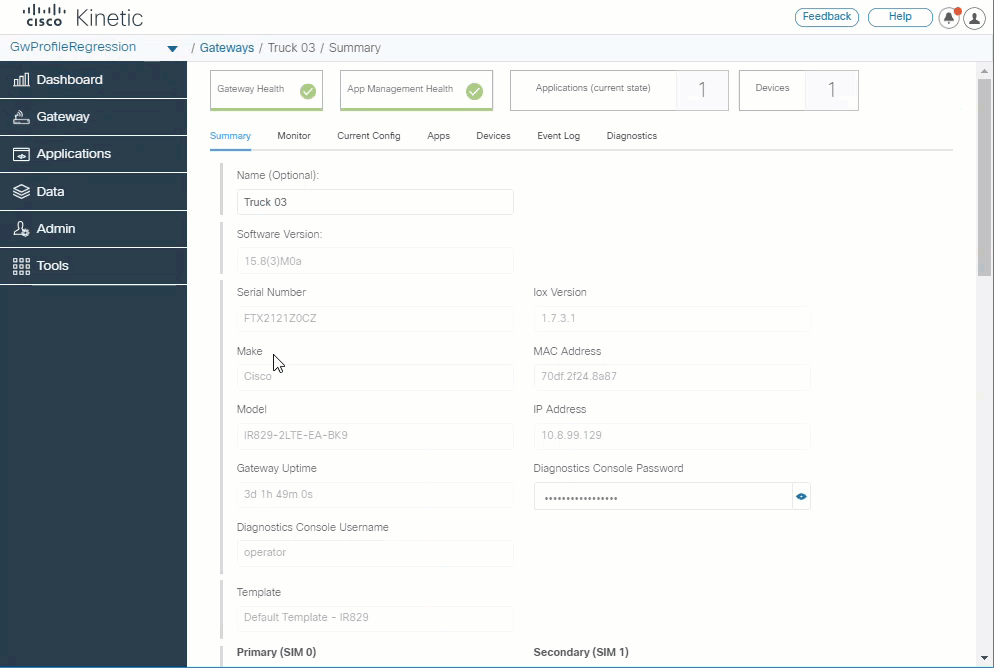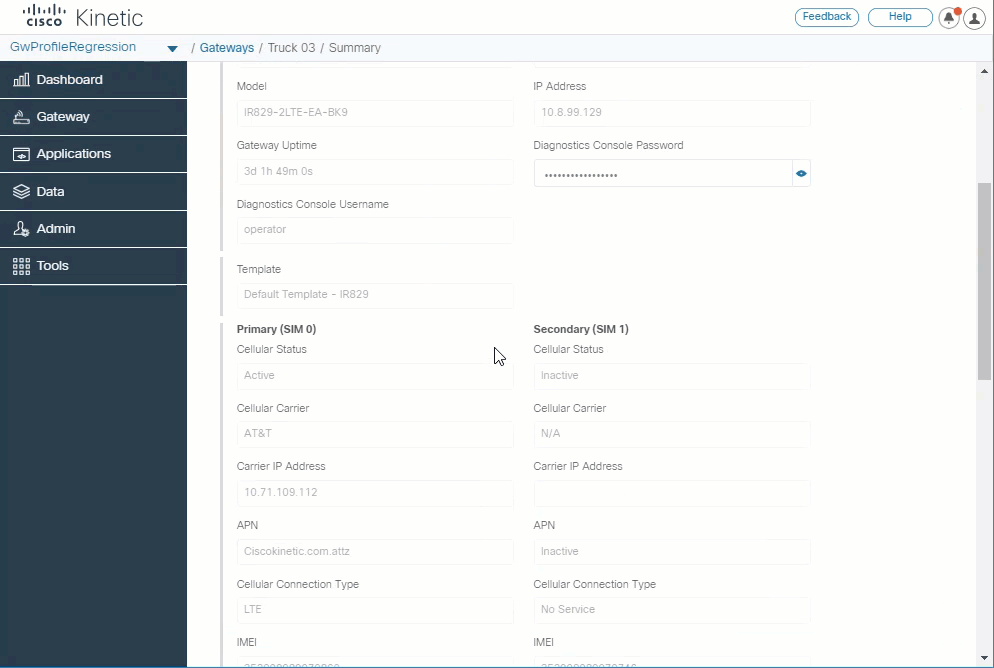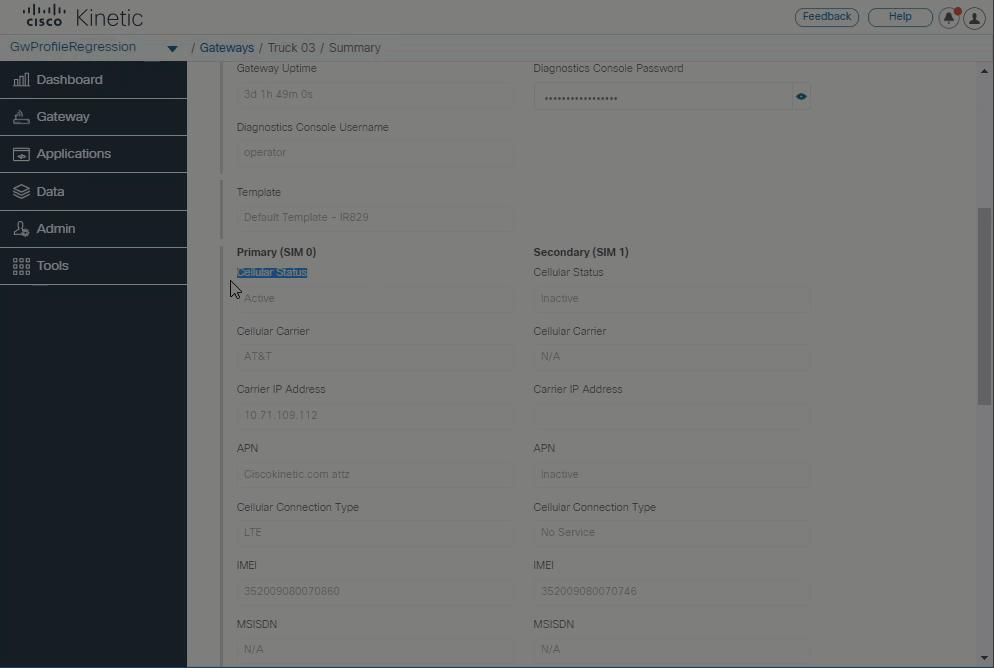
Enhanced gateway details page
Enhanced gateway details page now displays the device cellular carrier, IOS version, status, gateway name, model, tunnel Up/Down status, MAC and IP address, and cellular service details.
Port Forwarding
You can now configure Port Address Translation (PAT) to access subtended devices when using Site-to-Site VPN. Learn more
Other improvements
| Feature | Description |
|---|---|
| Low touch cellular provisioning | Gateways automatically connect to Kinetic using the cellular uplink public APN. It is no longer necessary to initialize the cellular APN using an Ethernet uplink connection. |
| Dual LTE support | A dual LTE IR829 gateway is now supported for increased cellular coverage area. |
| Configuration edit | The gateway configuration can now be changed by changing the device's configuration template. |
| Cellular monitoring | Cellular coverage and data utilization is now tracked. |
| Cellular details | Cellular activity and information for troubleshooting is provided, such as ICCID, MSISDN, and activity logs. |
| GPS tracking Improvements | Location tracking of gateway are now updated every 30 seconds. |
| Advanced search | You can now search for gateways using the gateway name, serial number, IOS version, custom field value, cellular network carrier, or the carrier type (3G, 4G, LTE). |
| IOS/IOX/AP code upgrade in backend | IOS/IOX/AP upgrades can be performed by Cisco Kinetic. |
Supported devices
IR809 gateways
- IR809G-LTE-VZ-AK9
- IR809G-LTE-NA-AK9
IR 829 gateways (Single LTE)
- IR829GW-LTE-VZ-AK9
- IR829GW-LTE-NA-AK9
IR 829 gateways (Dual LTE)
- IR829-2LTE-EA-BK9 (US - ATT & Verizon)
Open Issues
| Jira # | Description | Workaround |
|---|---|---|
| 18214 | Status for Site To Site Tunnel may show "Down" incorrectly even when the tunnel is up. | None. Wait 15-30 minutes for the status to be updated. |
| 21108 | Initial WGB and Wifi configuration may fail and eventually recover. | None. |
| 21168 | The VPN configuration may fail if the name-server table is full. | None. Contact ciscokinetic.io-support@cisco.com for assistance. |
| 21626 | The Fog Application page may not display the applications. | Refresh your browser. |
Fixed Issues
Cloud App - 1.5.1-102 (12/21/2017)
Issues resolved in this release:
| Jira # | Description |
|---|---|
| 21123 | Application Management fails to come up on dual LTE gateways (IR829-2LTE-EA-BK9). |
| 13219 | Fog Application upgrade fails with 409 conflict error. |