Inspect API Docs
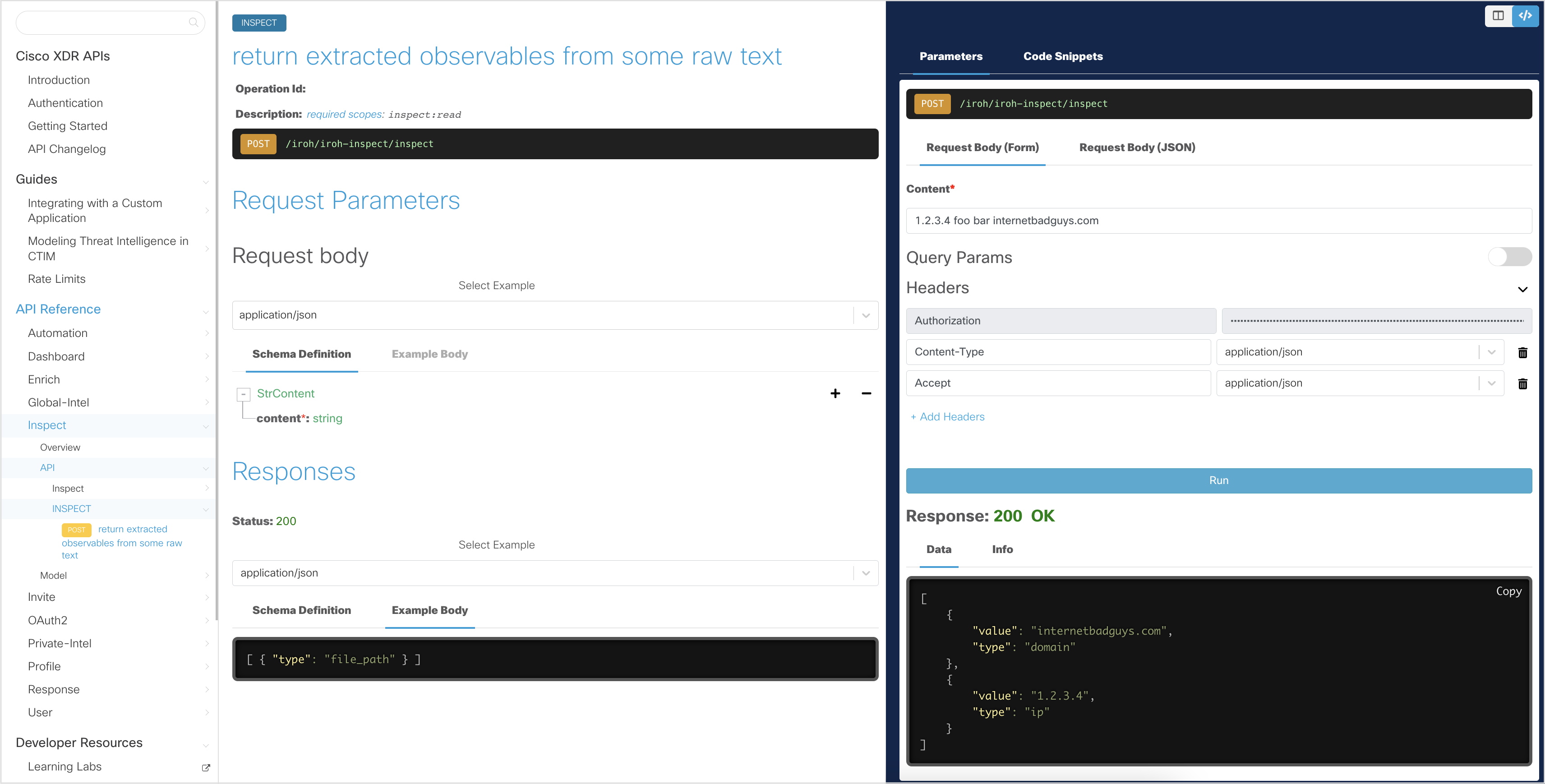
The Inspect API allows developers to find observables in an arbitrary string. This allows you to feed in textual information that may contain threat intelligence. The output of this API is a JSON structure of the observables to be used in subsequent API calls, such as Enrich or Response:
[
{
"type": "domain",
"value": "ilo.brenz.pl"
},
{
"type": "email",
"value": "no-reply@internetbadguys.com"
},
{
"type": "sha256",
"value": "8fda14f91e27afec5c1b1f71d708775c9b6e2af31e8331bbf26751bc0583dc7e"
}
]Use Cases
- Parse a blog post for interesting observables.
- Parse a Tweet for interesting observables.
- Quickly convert a set of observables into a JSON structure.
How to use the API Docs
Use the interactive documentation to explore the Inspect API endpoints. Each request will have a complete description of all the required parameters and it also allows you to instantly try it out in the online console. Code templates are also provided for you to quickly build scripts.
In the interactive explorer, the Client ID and Client Secret has been pre-filled and will allow you to make read-only API requests. These credentials will allow you to get an Access Token, which will be stored for subsequent API requests and regenerated when it expires.
Note: The interactive documentation uses read-only credentials and the try it out feature will only work with
GETand selectedPOSTrequests.To try other
InspectAPI requests, go to https://visibility.amp.cisco.com/iroh/iroh-inspect/index.html
Generate an Access Token
In the interactive API explorer, the Access Token is automatically generated using the pre-filled Client ID and Client Secret so you do not need to generate it yourself.
If you want to understand how the Access Token is generated from the Client ID and Client Secret credentials, take a look at the Authentication page.
For detailed instructions on how to use the interactive API documentation (or your own Python script), see the Getting Started page.
Download the Inspect OpenAPI Specification
Download the Inspect OpenAPI specification (OAS) file here.
Sample Code
Below is an example of how to use the Inspect API, without the Python SDK. Please check the Getting Started for instructions using the SDK.
import json
import requests
# create headers for API request (See the OAuth2 overview page for sample code to generate an access token)
access_token = 'eyJhbGciO....bPito5n5Q' # truncated example, generate JWT token separately
bearer_token = 'Bearer ' + access_token
# inspect the provided observable and determine its type
url = 'https://visibility.amp.cisco.com/iroh/iroh-inspect/inspect'
headers = {
'Authorization': bearer_token,
'Content-Type':'application/json',
'Accept':'application/json'
}
payload = {
'content': '1.2.3.4 foo bar internetbadguys.com'
}
response = requests.post(url, headers=headers, data=json.dumps(payload))
print(response.text)
if response.status_code == 200:
# convert the response to a dict object
response_json = json.loads(response.text)
# iterate through the list of observables
for observable in response_json:
# get the values from a Threat Context (remainder values are accessed in the same way)
value = observable['value']
type = observable['type']Contact: Cisco Security Business Group -- Advanced Threat
License: All Rights Reserved