Cisco Secure Access Add-On for Splunk
The Cisco Secure Access Add-On for Splunk is a web application that enables the integration of the Cisco Umbrella and Cisco Secure Access event data with the Splunk data platform.
This guide describes how to install and configure the Cisco Secure Access Add-On for Splunk in your instance of Splunk.
The Cisco Secure Access Add-On for Splunk is available at,
https://splunkbase.splunk.com/app/7569
What's New
The latest version of the Cisco Secure Access Add-On for Splunk is 1.0.48.
Updates to the Cisco Secure Access Add-On for Splunk
- Updated the display name of the add-on to
Cisco Secure Access Add-on for Splunk. - Updated the aliases for the fields in the DNS event type.
About the Umbrella Add-On for Splunk
For information about the Cisco Cloud Security Umbrella Add-On for Splunk, see Cisco Cloud Security Umbrella Add-On for Splunk Integration Guide.
About Event Log Headers
Important: When you export the organization's logs from the AWS S3 bucket, enable log headers. The add-on uses the log headers to extract the event data in the logs.
About S3 Bucket API Key Rotation
The add-on supports the rotation of the API key credentials for the Cisco-managed AWS S3 bucket configured in the add-on. The add-on will rotate the API key for the Cisco-managed S3 bucket before the API key expires. The administrator has the option to rotate the API key manually for the Cisco-managed S3 bucket in the add-on.
Installation of the Add-On in Distributed Deployments
You can install the add-on in a distributed deployment of Splunk Enterprise, or any deployment where you use forwarders to retrieve your data. Depending on your environment and preferences, and the requirements of the add-on, you can install the add-on in multiple environments.
We recommend that you only install the add-on using the Splunk heavy forwarder and Splunk indexes.
| Splunk Platform Component | Notes |
|---|---|
| Heavy Forwarder | Recommended. |
| Indexer | Supported if no heavy forwarders are enabled. |
About Configuring the Data Inputs
In the add-on, configure data inputs for the Umbrella or Secure Access event types. Splunk manages the Umbrella or Secure Access event data and displays the events on the Cloud Security dashboards in the Cisco Secure Access App for Splunk.
Umbrella data inputs
Configure any of the available Umbrella event types: dns, firewall, proxy, audit, or dlp.
- DNS logs
- Firewall logs
- Proxy logs for the Secure Web Gateway (SWG)
- Audit logs
- Data Loss Prevention (DLP) logs
Samples of the Umbrella log endpoints in a Cisco-managed bucket
| Event Type | Example |
|---|---|
| dns | 2506xxx_2db1xxxx1ddf7cxxx18652xxxxfdab7xxxxd60xx/dnslogs/ |
| proxy | 2506xxx_2db1xxxx1ddf7cxxx18652xxxxfdab7xxxxd60xx/proxylogs/ |
| firewall | 2506xxx_2db1xxxx1ddf7cxxx18652xxxxfdab7xxxxd60xx/firewalllogs/ |
| audit | 2506xxx_2db1xxxx1ddf7cxxx18652xxxxfdab7xxxxd60xx/auditlogs/ |
| dlp | 2506xxx_2db1xxxx1ddf7cxxx18652xxxxfdab7xxxxd60xx/dlplogs/ |
Secure Access data inputs
You must configure all available Secure Access event types: dns, firewall, proxy, audit, dlp, ravpn, ztna, and ips.
- DNS logs
- Firewall logs
- Proxy logs for the Secure Web Gateway (SWG)
- Audit logs
- Data Loss Prevention (DLP) logs
- Remote Access Virtual Private Network (RAVPN) logs
- Zero Trust Network Access (ZTNA) logs
- Zero Trust Network Access (ZTNA) Flow logs
- Intrusion Prevention System (IPS) logs
Samples of the Secure Access log endpoints in a Cisco-managed bucket
| Event Type | Example |
|---|---|
| dns | 2506xxx_2db1xxxx1ddf7cxxx18652xxxxfdab7xxxxd60xx/dnslogs/ |
| proxy | 2506xxx_2db1xxxx1ddf7cxxx18652xxxxfdab7xxxxd60xx/proxylogs/ |
| firewall | 2506xxx_2db1xxxx1ddf7cxxx18652xxxxfdab7xxxxd60xx/firewalllogs/ |
| audit | 2506xxx_2db1xxxx1ddf7cxxx18652xxxxfdab7xxxxd60xx/auditlogs/ |
| dlp | 2506xxx_2db1xxxx1ddf7cxxx18652xxxxfdab7xxxxd60xx/dlplogs/ |
| ravpn | 2506xxx_2db1xxxx1ddf7cxxx18652xxxxfdab7xxxxd60xx/ravpnlogs/ |
| ztna | 2506xxx_2db1xxxx1ddf7cxxx18652xxxxfdab7xxxxd60xx/ztnalogs/ |
| ztna flow logs | 2506xxx_2db1xxxx1ddf7cxxx18652xxxxfdab7xxxxd60xx/ztnaflowlogs/ |
| ips | 2506xxx_2db1xxxx1ddf7cxxx18652xxxxfdab7xxxxd60xx/intrusionlogs/ |
Get Started: Install and Configure the Cisco Secure Access Add-On for Splunk
- Review the prerequisites for installing and configuring the add-on. For more information, see Prerequisites.
- Download and install the Cisco Secure Access Add-On for Splunk in your instance of Splunk. For more information, see Download and Install the Add-On.
- For the add-on, accept the Terms and Conditions. For more information, see Accept the Terms and Conditions.
- Add the information for your AWS Accounts in the add-on. For more information, see Add Your AWS Accounts.
- Confirm the configuration of the Umbrella or Secure Access data inputs. For more information, see About Configuring the Data Inputs and Create New Inputs for Umbrella or Secure Access.
- View your configured events on the dashboards in the Cisco Secure Access App for Splunk. For more information, see View Cloud Security Dashboards.
Walkthrough: Cisco Secure Access Add-On for Splunk
Prerequisites
- An instance of Splunk Enterprise or Splunk Cloud that supports Splunk platform versions 9.4.x or 9.3.x.
- A subscription for Cisco Umbrella or Cisco Secure Access.
- An AWS account associated with the configured AWS S3 bucket.
- The credentials and bucket information for your own or a Cisco managed AWS S3 bucket.
- AWS S3 Access key credentials (AWS Access key ID and secret).
- AWS S3 region.
- AWS S3 bucket name.
- AWS S3 directory prefix.
- For your instance of Splunk, administrative privileges and an environment with Python 3.9.
Note: You can not use the Cisco Secure Access Add-On for Splunk with the Splunk Free license.
Download and Install the Add-On
- Navigate to Splunkbase at
https://splunkbase.splunk.com/. - Search for Cisco Secure Access Add-on for Splunk.
- Download the latest Cisco Secure Access Add-On for Splunk software package (
TA-cisco-cloud-security-addon-1.0.48.tar.gz). - Install the Cisco Secure Access Add-On software package on your instance of Splunk.
Accept the Terms and Conditions
In your instance of Splunk, locate the Splunk navigation bar, click Apps, and then select Cisco Secure Access Add-on for Splunk.
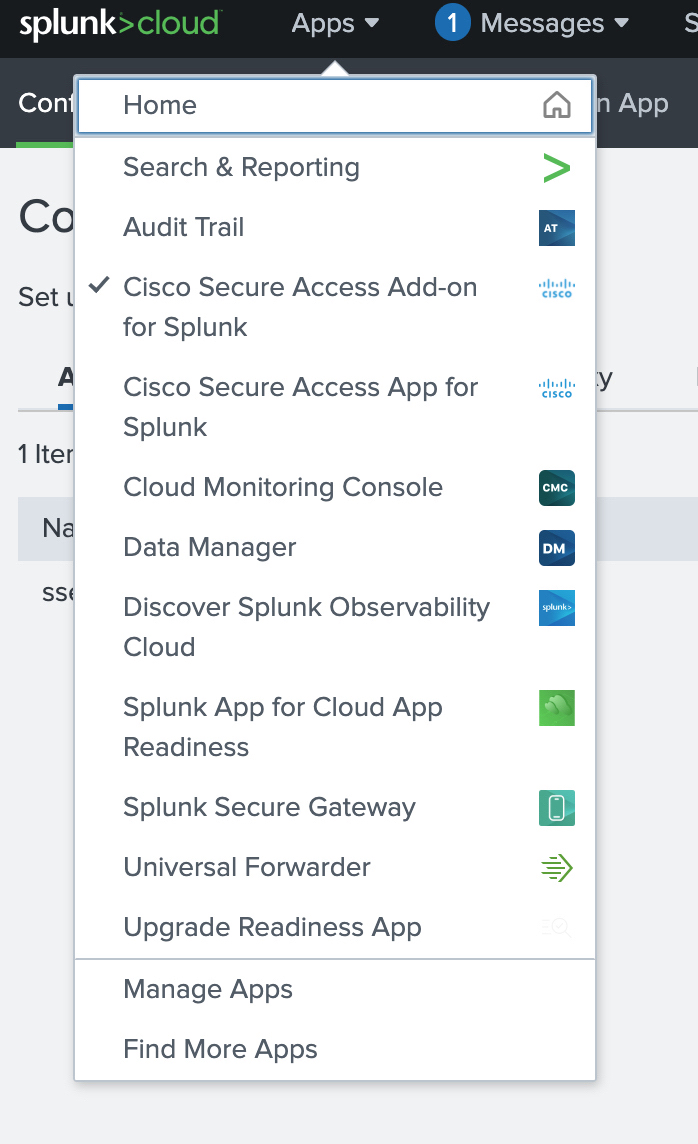
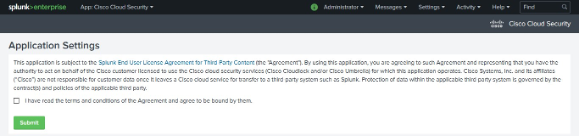
Navigate to Application Settings.
Click I have read the terms and conditions of the Agreement and agree to be bound by them.
Click Submit.
Add Your AWS Accounts
Add your AWS account information in the add-on.
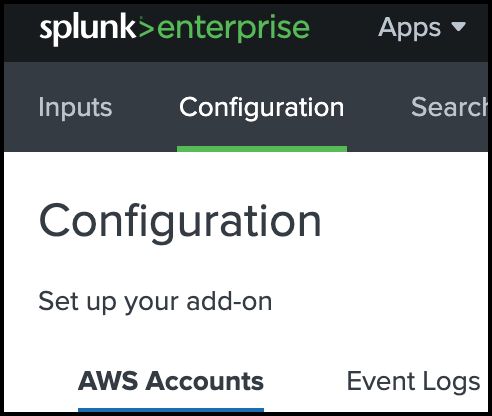
Navigate to Application Settings.
Navigate to Configuration, and then click AWS Accounts.
Configure the setttings for an AWS account in the add-on.
- For Name, enter a unique name of an AWS account where you have your own or a Cisco-managed S3 bucket.
- For AWS Access Key Id, enter your AWS Access key ID.
- For AWS Secret Access Key, enter your AWS Secret Access key.
- For AWS Region, enter your AWS S3 region, for example:
us-west-1.
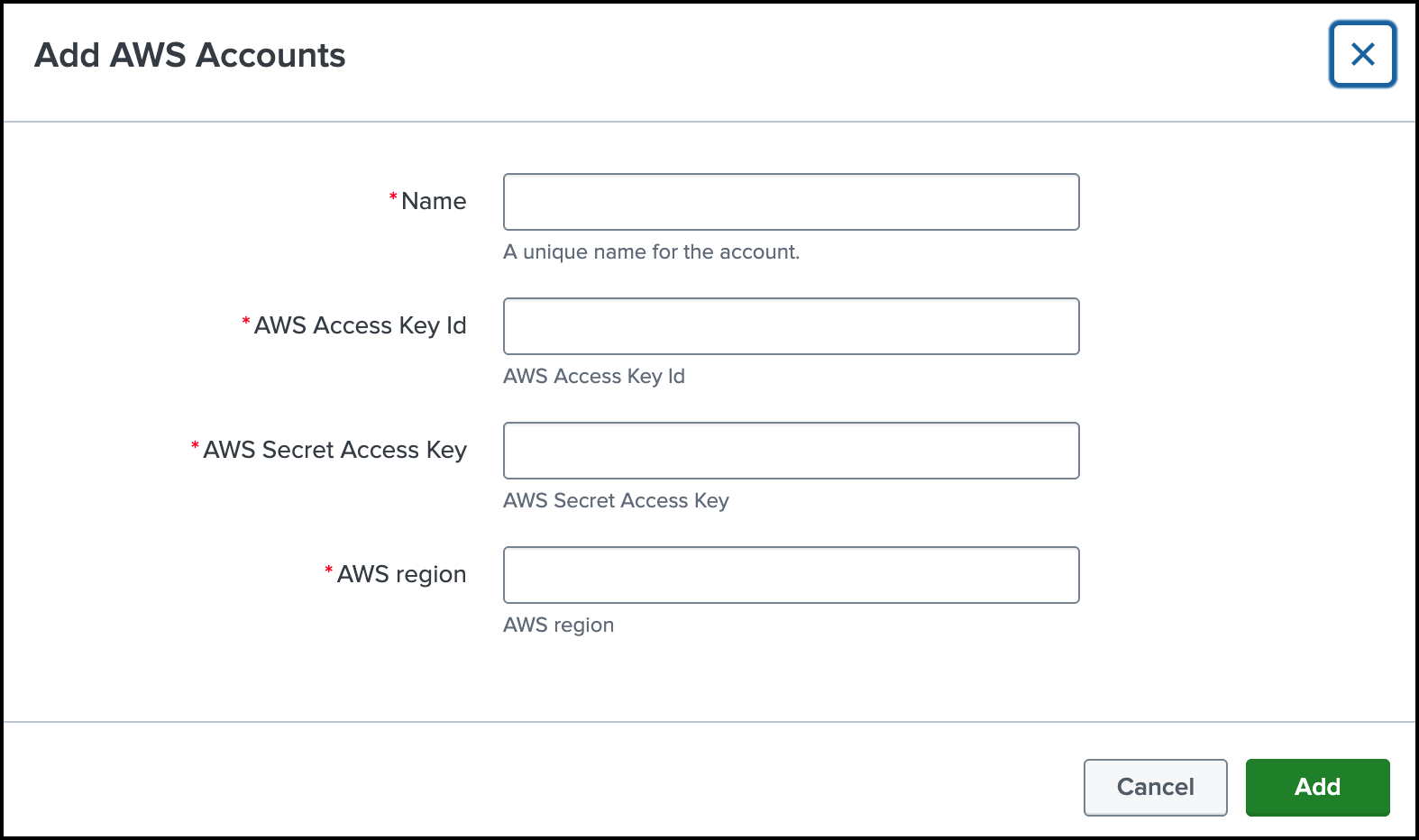
Click Add.
To add more AWS accounts in the add-on, repeat Steps 3–4.
Create New Inputs for Umbrella or Secure Access
Add Umbrella or Secure Access event types to integrate the event data from your own or a Cisco-managed S3 bucket with Splunk. Each line in a log file is processed and written to Splunk as a single event. For information about event types, see About Configuring the Data Inputs.
You can set up all event data by selecting Yes for the Create inputs for all event types option. Otherwise, select No and then enter the event types in the add-on.
After you add the first event type, you can clone it. Then, update the required settings for each cloned event type. For more information, see Clone an Event Type.
We recommend that you provide a unique name for each input.
Important: If you upgrade the add-on, you must reenter the AWS Secret Access Key. Do not edit the Default Start Date for an existing input.
Navigate to Application Settings.
Navigate to Configuration, and then click Event Logs.
Enter the values for Name, AWS Account to use, Bucket Name, Directory Prefix, Interval, Index, and Default Start Date.
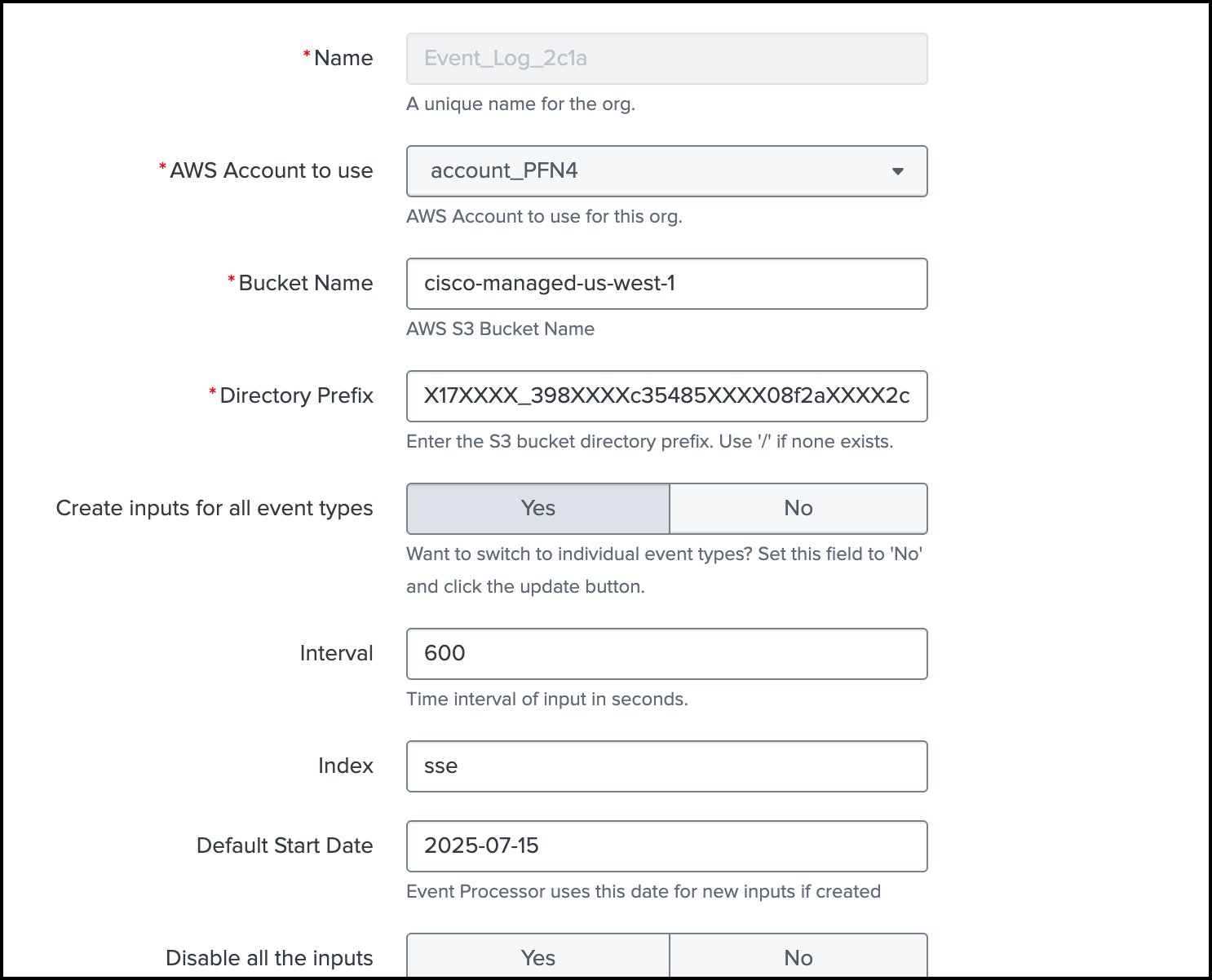
- Name—Enter a unique name for the integration of the Umbrella or Secure Access events in the add-on.
- AWS Account to use—Enter the name of the AWS account that you configured in the add-on.
- AWS S3 Bucket Name—Enter your AWS S3 Bucket Name, for example:
cisco-managed-us-west-1. - AWS S3 Directory Prefix—Enter the AWS S3 directory prefix and append it with a forward slash (/), for example: /dnslogs.
- Interval—Provide an interval (in seconds) to fetch the data to the Splunk indexer. We recommend
600seconds. - Index—Choose the index where to store the Umbrella or Secure Access logs. We recommend that you do not choose the
defaultindex. - Default Start Date—Enter a date in the
YYYY-MM-DDformat, for example:2022-02-27. We recommend that you set the Default Start Date to the date when you installed the app. Selecting a date before the date when you installed the app may create a backlog of events that the app must process.- Note: You can enter a Default Start Date with the current day using the
YYYY-MM-DDformat.
- Note: You can enter a Default Start Date with the current day using the

For Create inputs for all event types—Click Yes to create all events types for the AWS Account and S3 bucket, or click No, and then enter each event type in the add-on.
- (Optional) You can clone the first event type that you added. For more information about cloning an event type, see Clone an Event Type.
For Disable all the inputs, choose Yes to disable all configured inputs or click No.
Clone an Event Type
After you add the first event type, you can clone it and configure more data inputs. For each event type, you must configure the required settings.
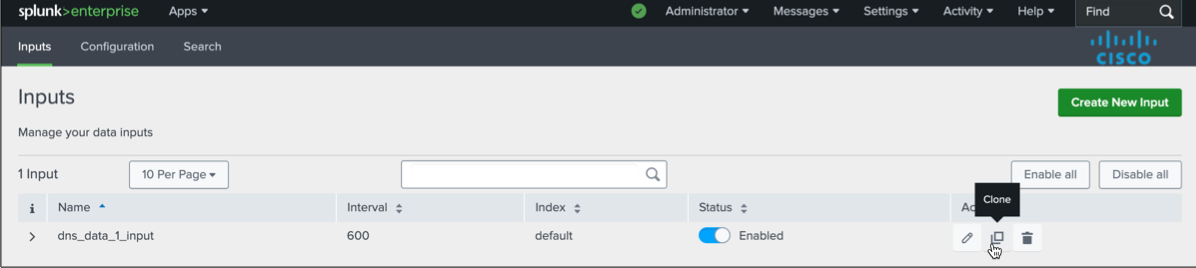
Navigate to Application Settings.
Navigate to Inputs.
Click Clone. The add-on clones many of the fields and attributes from the first event type.
For this input, enter the values for Name, AWS Secret Access Key, AWS S3 Directory Prefix, and Event Type.
- For Name, enter a name for the data input.
- For AWS Secret Access Key, enter your AWS Secret Access key.
- For AWS S3 Directory Prefix, enter the AWS S3 directory prefix and append it with a forward slash, for example: /dnslogs/.
- For Event Type, choose one of the event types: dns, firewall, proxy, audit, dlp, ravpn, ztna, or ips.
Contact Support
- If you have questions about configuring the data inputs for Umbrella in the Cisco Secure Access Add-On, contact Cisco Umbrella Support.
- If you have questions about configuring the data inputs for Secure Access in the Cisco Secure Access Add-On, contact Cisco Support.