Cisco ISE
Note: The documentation set for this product strives to use bias-free language. For purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product.The External RESTful Services (ERS) APIs are based on HTTPS protocol and REST methodology and uses port 9060. ERS is designed to allow external clients to perform CRUD (Create, Read, Update, Delete) operations on Cisco ISE resources. ERS is based on the HTTP protocol and REST methodology. The External RESTful Services APIs support basic authentication. The authentication credentials are encrypted and are part of the request header. The Cisco ISE administrator must assign special privileges to a user to perform operations using the External RESTful Services APIs.
To perform operations using the External RESTful Services APIs (except for the Guest API), the users must be assigned to one of the following Admin Groups and must be authenticated against the credentials stored in the Cisco ISE internal database (internal admin users):
- External RESTful Services Admin: Full access to all ERS APIs (GET, POST, DELETE, PUT). This user can Create, Read, Update, and Delete ERS API requests.
- External RESTful Services Operator: Read Only access (GET request only).
If you do not have the required permissions and still try to perform operations using the External RESTful Services APIs, an error response is received.
Note: The ERS is limited to Active Directory operations only for Cisco ISE-PIC nodes.
Note: The ERS APIs support TLS 1.1 and TLS 1.2. ERS APIs do not support TLS 1.0 regardless of enabling TLS 1.0 in the Security Settings window of the Cisco ISE GUI (Administration > System > Settings > Security Settings). Enabling TLS 1.0 in the Security Settings window is related to the EAP protocol only and does not impact ERS APIs.
In this section you will learn how to easily enable ERS and to start building your own applications.
Enable ERS (port 9060)
ERS uses on HTTPS port 9060 which is by default closed. Clients trying to access this port without enabling ERS first, will face a timeout from the server. Therefore, the first requirement is to enable ERS from the Cisco ISE admin UI. Go to Administration > Settings > ERS Settings and enable the Enable ERS for Read/Write radio button as shown in the screenshot below.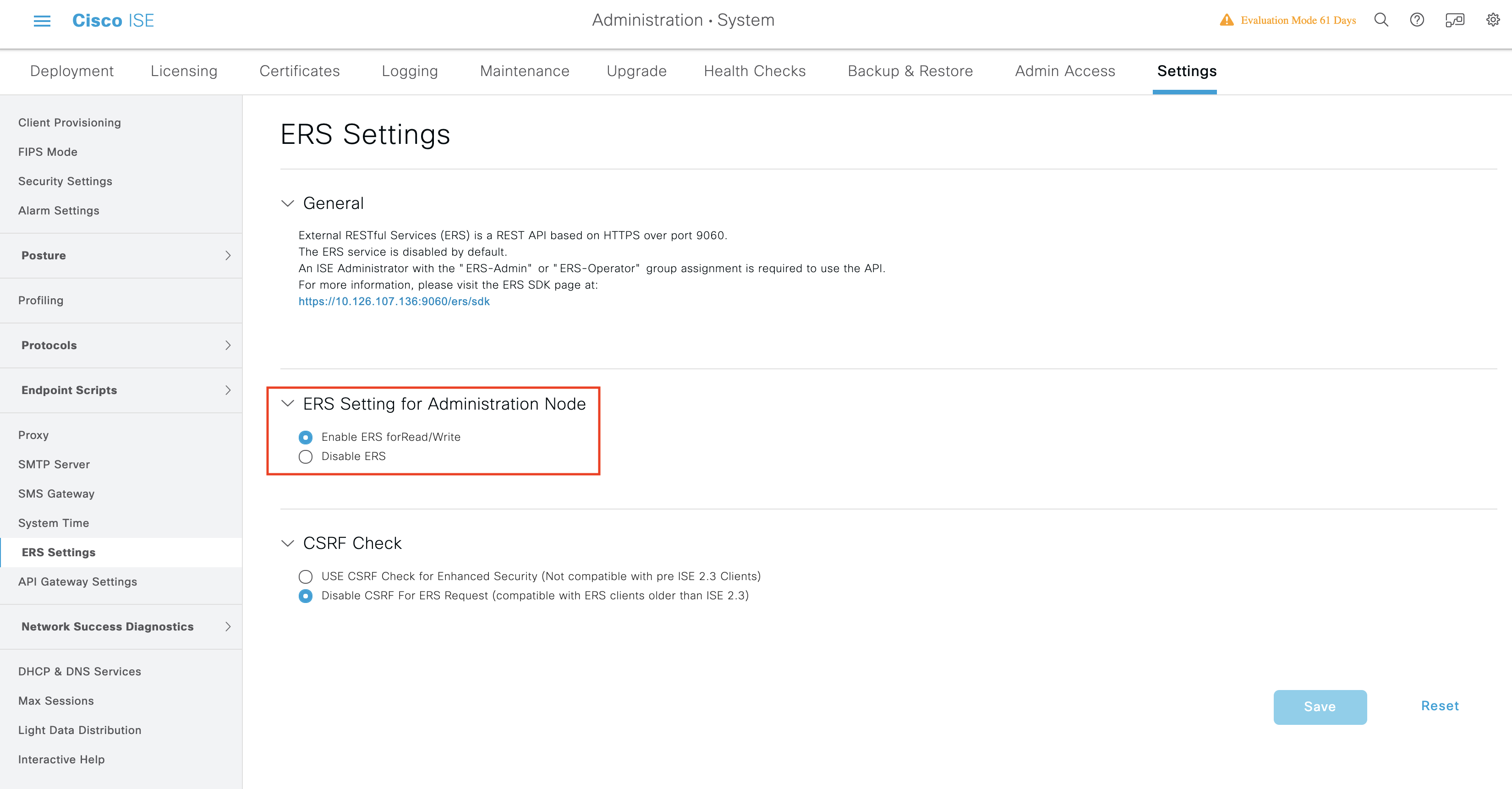
Creating ERS Admin
The second requirement is to create a Cisco ISE Administrator with the admin group as ERS-admin as shown in the following screenshot: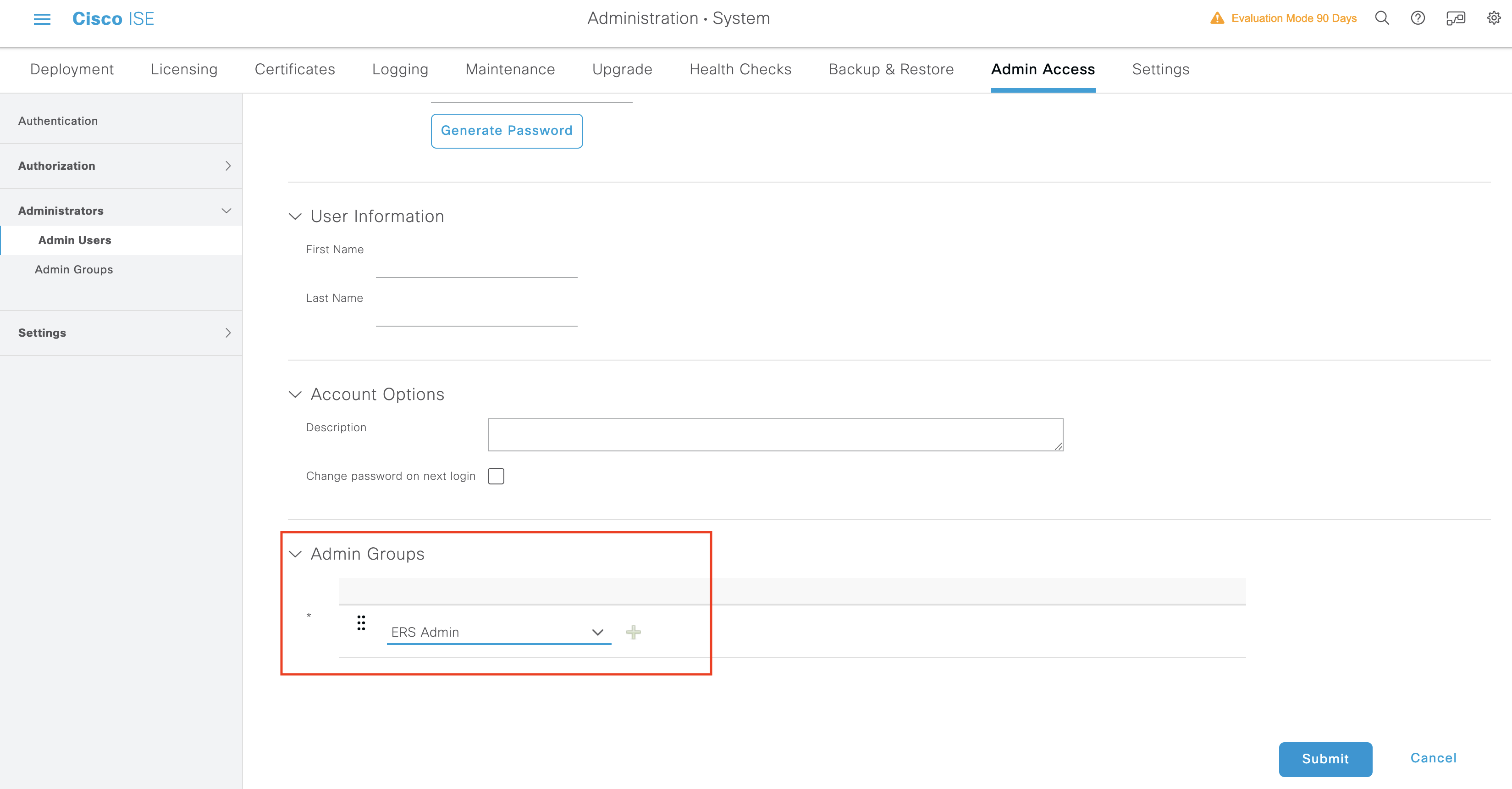
Setting up ERS for Sponsor Access
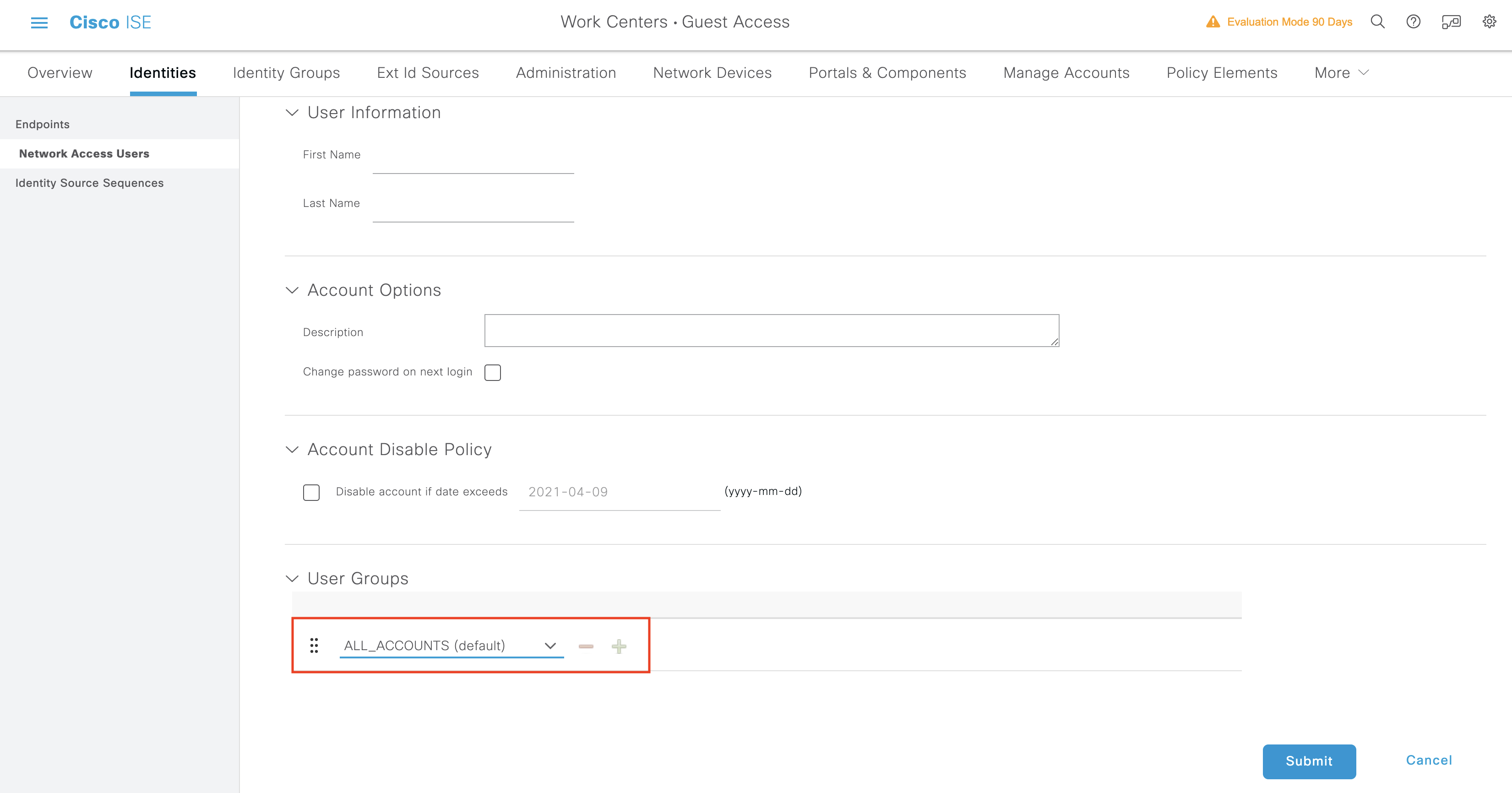
To access Sponsor API to perform operation on GuestUsers, it is required to enable ERS as shown above but instead of using ISE Admin, it is required to create an internal user who belongs to the ALL_ACCOUNTS(default) group, and edit the ALL_ACCOUNTS(default) sponsor group setting to enable the REST API for Sponsor. Those steps are shown in the screenshots below:Creating internal user belonging to the ALL_ACCOUNTS(default) group
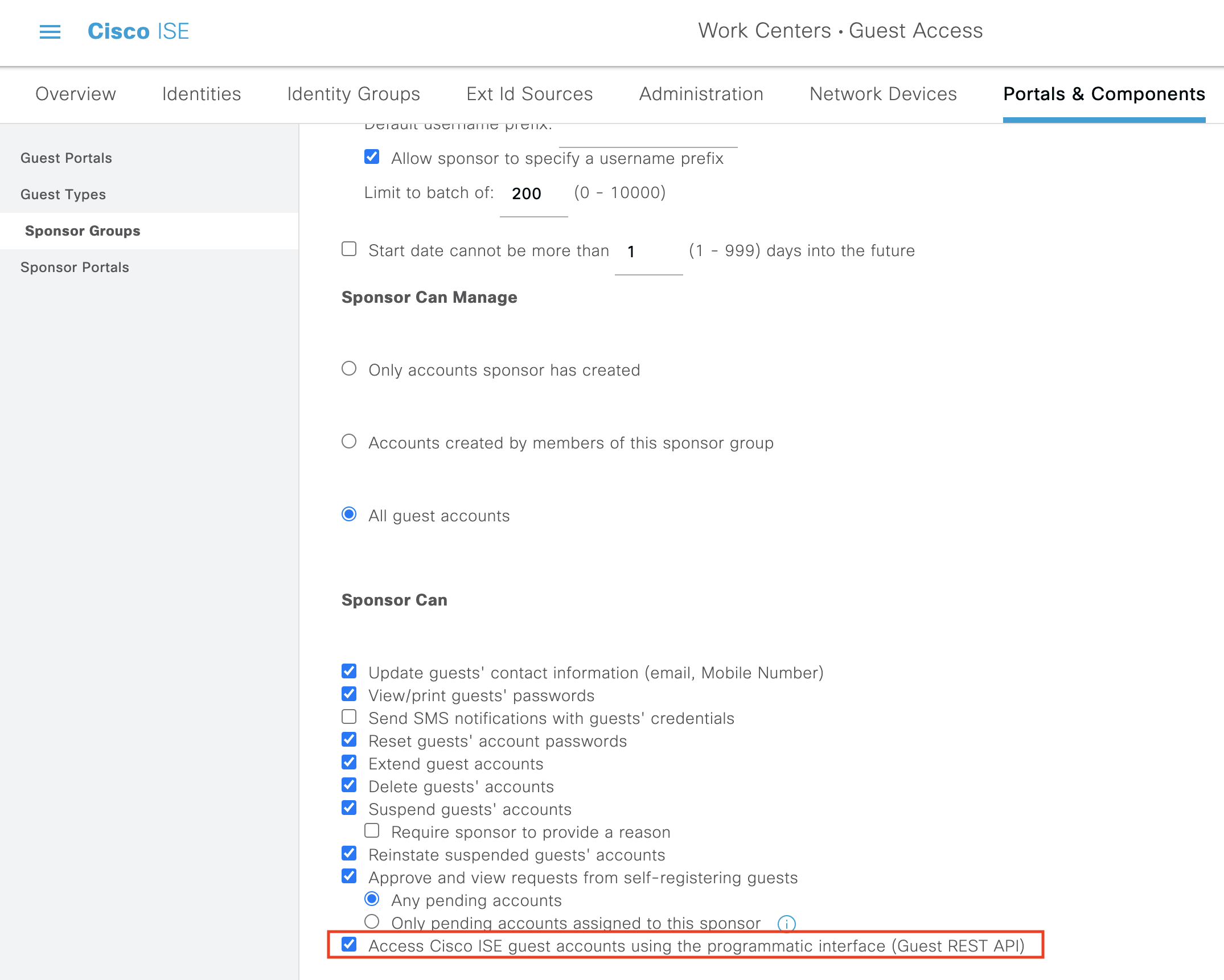
Edit the ALL_ACCOUNTS(default) sponsor group
Allow access for guest users through the REST API