Multi-factor authentication (MFA) for enhanced security in Cisco IoT Operations Dashboard
Cisco IoT Operations Dashboard enhances security by supporting MFA enforcement for users who log in through Cisco identity platform. MFA adds an extra layer of security to your IoT deployments.
How MFA works
When MFA is enabled, users must authenticate themselves using at least two factors. This typically involves entering their credentials and verifying their identity using a one-time password (OTP) generated by an authenticator app.
How MFA is enforced
MFA is enabled at the organization level within IoT OD. Once MFA is activated for an organization, all users within that organization must use it for authentication. After successful authentication through MFA, users can continue to use any features and services on IoT OD based on their assigned roles and permissions.
MFA workflow
- Admins enable MFA. Administrators log in to the Cisco IoT Operations Dashboard and enable MFA at the organization and or sub-organization levels.
- Users set up MFA in Cisco identity platform: Users log in to id.cisco.com, choose their preferred verification app, and set up MFA.
- Install the authenticator app: Users install the authenticator app on their mobile device.
- Log in to the Cisco IoT Operations Dashboard: Users try to log in to the IoT Operations Dashboard by entering their credentials.
- MFA verification: After successful credential verification, an OTP is displayed on the chosen verification app on the user's mobile device.
- Enter OTP and access dashboard: Users enter the received OTP on the login screen to complete the multi-factor authentication and gain access to the Cisco IoT Operations Dashboard.
Notes:
- By default, MFA is enforced on all your organizations (tenants). You can disable MFA from one or more organizations if needed.
- MFA is enforced only for users who authenticate using Cisco IdP. If you use your own identity provider (IdP) for authentication, MFA isn't enforced.
Enable or disable multi-factor authentication
Follow these steps to enable or disable MFA on IoT OD.
Log in to the Cisco IoT Operations Dashboard as a tenant admin or system admin.
Click the "people icon" in the far right of the header. Click Access Control. The Access Control page opens.
Select the Organizations tab.
a. Select the organization that requires MFA access. The detail page for that organization opens.
b. Click Edit Organization. The edit organization page opens.
c. Select or clear the Enable Multi-Factor Authentication check box from the Features list.
d. Click Save.
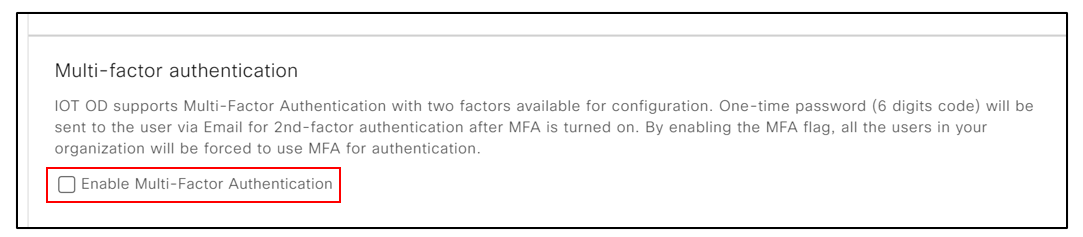
IMPORTANT: After enabling MFA for your organization, users must log out from IoT OD and then log back in to use MFA.
Set up MFA in Cisco identity platform
Follow these steps to set up MFA in Cisco identity provider.
Log in to id.cisco.com.
Go to the Security tab.
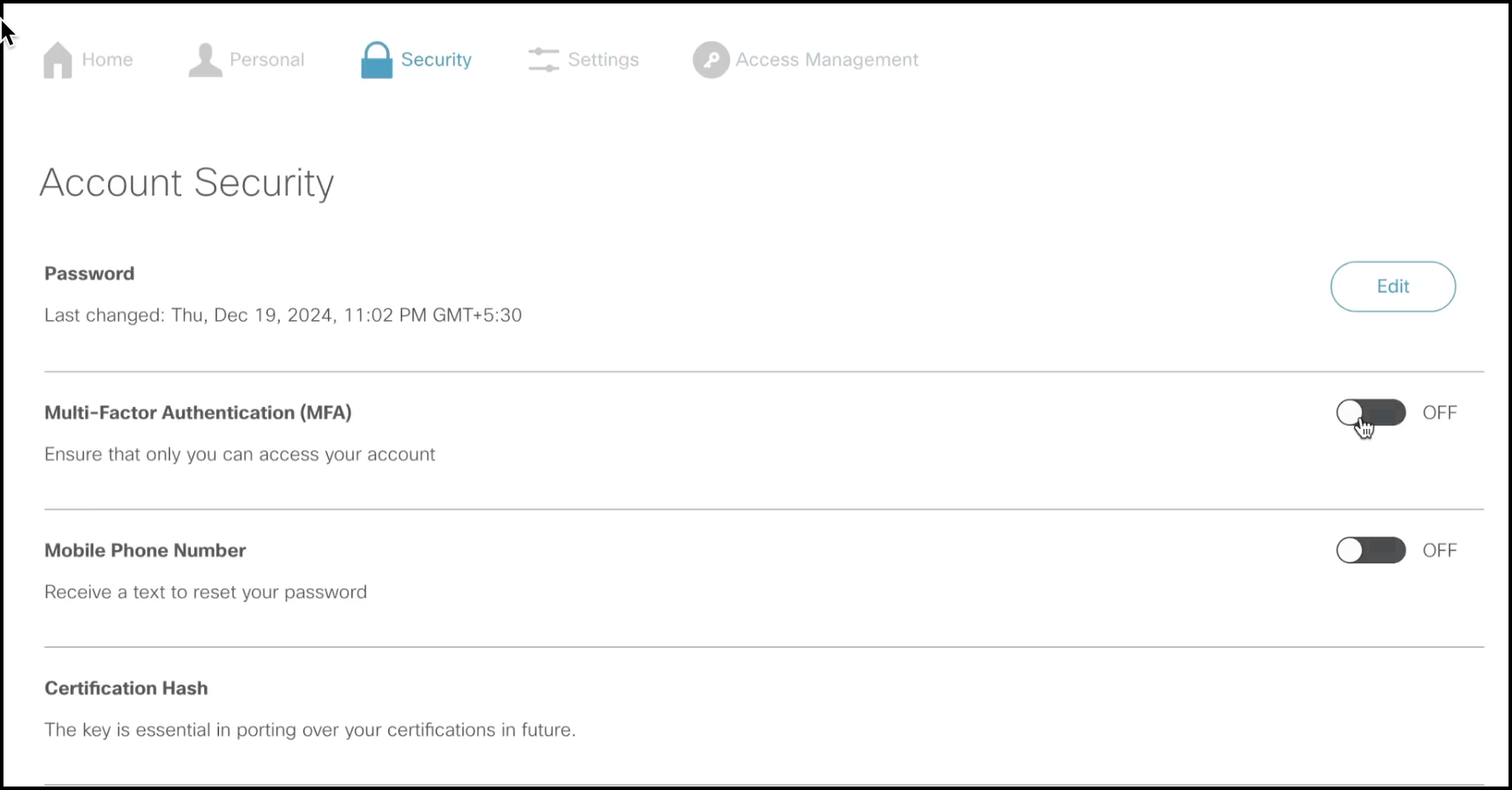
Under Account Security, enable the Multi-Factor Authentication(MFA) toggle button. A window opens, prompting you to enter your password.
Enter your password and click Verify.
The Enroll in Multi-Factor Authentication window appears, allowing you to select your authenticator app. Available options include Cisco Duo and Google Authenticator.
Select your preferred authenticator app, and click Next.
A window displaying a QR Code opens.
Open the authenticator app on your mobile device and scan the QR Code.
The authenticator app generates a 6-digit code on your phone.
Enter the code in the window and click Submit.
A confirmation window appears, indicating successful enrollment.
Multi-factor authentication scenarios
Using your own identity provider (IdP)
If your IoT OD organization uses an external identity provider (like Active Directory) for authentication, enabling MFA doesn't affect how your users log in to Cisco IoT Operations Dashboard.
Mixed IdP environments
If one organization uses a non-Cisco IdP and another uses Cisco IdP, only users in the organization that uses Cisco IdP are subject to MFA enforcement.
Switching from a non-MFA to MFA organization
Users must log out and re-authenticate with the new IdP after switching organizations.
Switching organizations within the same IdP
Users can seamlessly switch between organizations that use the same IdP without requiring a new login.
Switching IdPs
Users are prompted to log out and re-authenticate with the new IdP.