Enable Multi-Factor Authentication (MFA) for an Organization on IoT OD
Notes:
- Before you begin, you must be logged in to IoT OD and have an existing Organization. See Log in to the IoT Dashboard.
- Multi-factor authentication (MFA) is activated on a "per Organization" basis by the Tenant Admin role. After MFA activation in the Organization, all local users go through the MFA for authentication.
- The MFA feature is applicable for locally configured users on OD. If an Organization has Single Sign On (SSO) activated in the Organization, please use MFA on the side of security assertion markup language (SAML) Identity Provider (IdP).
Using MFA without SSO
MFA access to IoT OD is granted for locally configured users (meaning your Organization's Tenant Admin adds users to your organization and grants roles/permissions to those users). After authentication through MFA, the user can use any features and services on IoT OD according to the permissions associated with the user's role. For example, if an Organization has MFA activated and a local user with an SEA User role would like to use the SEA/Remote Sessions page to access a connected client with third-party software, then the user would access IoT OD via MFA first. After that, they can initiate SEA remote sessions configured for that particular user.
The following conditions apply:
- When a user accesses the IoT OD Organization (account), then the IoT OD Organization requires using MFA for every configured user with a minimum of two factors:
- First factor: username/password
- Second factor: one-time password (OTP) via email
- When the Tenant Admin accesses the IoT OD Organization, then the Tenant Admin can activate (or deactivate) MFA for the Organization and all the locally configured users have to go through MFA.
Notes:
- Activation of the MFA feature should be available for internal local users of Organizations and external invitees (e.g., external contractors who are allowed access to their systems via SEA in the Organization).
- This procedure is only for a Tenant Admin role with privilege. All other users will not see this screen.
To enable MFA for an existing Organization:
- Click the "people icon" in the far right of the header. Click Access Control. The Access Control page opens.
- Click the Organizations tab.
- Select the Organization that requires MFA access. The detail page for that organization opens.
- Click Edit Organization. The edit organization page opens.
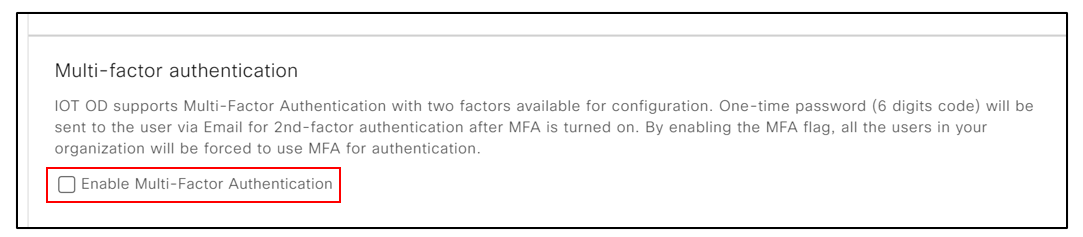
- Select the Enable Multi-Factor Authentication check box from the Features list.
- Click Save.
To enable MFA for a new Organization:
- Click Add Organization. The detailed organization page opens.
- Fill in all the details and select the Enable Multi-Factor Authentication checkbox.
- Click Save.
IMPORTANT: After enabling MFA for an organization, you must log out from the organization and log back in to start using MFA.
Using Single Sign On (SSO)
If you have single sign-on authentication and authorization to access IoT OD enabled, then all users should be configured on an external identity provider (IdP). Cisco does not control the external IdP access. All authentication services are delivered to users on the IdP. If the IdP supports multi-factor authentication (MFA), the MFA can be applied to the IdP.
Depending on SSO/SAML configuration, users can experience one of the two main flow types:
- IdP initiated flow: The user should go to authentication against IdP first (including MFA on the IdP side if configured). After successful authentication, IdP allows the user to access the application (IoT OD).
- Service Provider (SP) initiated flow: The user is accessing the application first (IoT OD) and IoT OD redirects the user to an IdP for proper authentication.