Log Export API
The Log Export API provides download links for specified log files within a given time range. It enables users to retrieve consolidated logs from the Secure Email Threat Defense (ETD) system. A common use case for this API is integrating ETD data with Security Information and Event Management (SIEM) applications like Splunk.
Blocked Connection Logs
Blocked Connection Logs allows users to get detailed information on blocked connections, including the reason for blocking, timestamp, sender, and recipient details. This comprehensive data helps users understand why a connection was blocked and when it occurred, enabling them to take the necessary security actions effectively.
Note:
- Licensing: Blocked Connection Logs works only in Inline Mode and is available only with an ETD Advantage License.
- To export blocked Connection Logs, set the
logTypesparameter in your request body to["connection"].
Audit logs
Audit logs allow the user to get ETD audit logs for a given timerange. The logs capture admin activities and security policy configurations for compliance tracking.
Note To export audit logs, set the
logTypesparameter in your request body to["audit"].
Sample Logs
{"category":"user","timestamp":"2025-06-16 06:54:55","action":"get_securex_ribbon_access_token","status":"success","comments":null,"user":{"ip":"151.186.181.86","userAgent":"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36","id":"0b74ee5b-e462-4ddc-8cbe-8c584137e399"},"metadata":null}
{"category":"tenant","timestamp":"2025-07-16 10:38:24","action":"create_public_api_client","status":"success","comments":null,"user":{"ip":"173.38.117.73","userAgent":"python-requests/2.32.0","id":"716b2b58-2d8f-4cb3-80c5-85f4d48a07bf"},"metadata":{"clientId":"d7bb7495-f486-48f3-9276-c74ea39e7236"}}
{"category":"email","timestamp":"2025-07-16 05:27:16","action":"reclassify","status":"success","comments":"","user":{"ip":"173.38.117.91","userAgent":"python-requests/2.32.4","id":"5f94fb97-742b-446a-90f8-d0c49a958e5b"},"metadata":{"request":{"headers":{"host":"integration-o365-action-api.projectraptor.io"}},"verdict":"neutral","action":"","description":"Changing verdict to neutral","emailId":"4bc87252-8721-43b7-97b1-1ca0ea53f173"}}
Message Event logs
Message Event logs allow the user to obtain consolidated ETD message event logs for a given time range, enabling customers to correlate ETD data with other security sources and facilitating SIEM integration.
Event Types
Message events are categorized into two types:
- Create – Applied automatically to new messages, whether they are normal or convicted via ETD.
- Update – Applied to messages when any reclassification or remediation is performed via the ETD UI, API, or through Retrospective Verdicts.
Note If the email is neutral, the message event log will have an event type of create and will not include verdict or action objects. For convicted emails, both verdict and action objects will be present in the message event log with a create event type. If further actions such as reclassification or remediation are taken on the email, either the verdict object, the action object, or both will be included in the message event log with an update event type.
Sample Logs
- Normal Email
An email delivered to a user's inbox without any threat verdict.
{"message": {"eventType": "create", "id": "0540d1c3-8a9e-487c-800b-1391798e95fd", "envelopeTo": ["aanderson@raptoretdautoe2e.onmicrosoft.com"], "internetMessageId": "OtOdKmDRpLSwjPkGUaznVGnxW", "mailboxes": ["aanderson@raptoretdautoe2e.onmicrosoft.com", "dgoodwin@raptoretdautoe2e.onmicrosoft.com"], "fromAddresses": "dgoodwin@raptoretdautoe2e.onmicrosoft.com", "clientIp": "20.190.152.152", "serverIp": "2603:1096:a01:58::7", "subject": "http://www.castaneda.biz/main", "timestamp": "2025-07-16T05:59:42Z", "direction": "internal", "secureEmailGateway": {"gatewayType": "ciscoDefault", "headerName": "X-IronPort-RemoteIP"}, "toAddresses": ["aanderson@raptoretdautoe2e.onmicrosoft.com"], "urls": [{"url": "http://www.castaneda.biz/main"}, {"url": "http://www.castaneda.biz/main.eml"}]}, "tenantId": "07fa4225-ed36-48b0-b165-3468fa6605ef", "logType": "message", "logDate": "2025-07-16", "logHour": "06"}
- Convicted Email
An email identified as malicious (e.g., phishing, malware) based on threat intelligence and scanning. A protective action, such as moving the email to quarantine, junk, or trash, or deleting it, is automatically performed by the system.
{"message": {"eventType": "create", "id": "18e4177a-5124-4bb2-934d-12eff40e99bc", "returnPath": "automationuser1@etdcesautomation.com", "clientIp": "2a01:111:f403:c408::1", "envelopeTo": ["sacjha@raptoretdautoe2e.onmicrosoft.com"], "fromAddresses": "automationuser1@etdcesautomation.com", "toAddresses": ["sacjha@raptoretdautoe2e.onmicrosoft.com"], "direction": "incoming", "secureEmailGateway": {"gatewayType": "ciscoDefault", "headerName": "X-IronPort-RemoteIP"}, "mailboxes": ["sacjha@raptoretdautoe2e.onmicrosoft.com"], "serverIp": "2603:1096:a04::207", "timestamp": "2025-07-21T06:35:55Z", "internetMessageId": "<PN3P287MB0337E3B075A9B9D5368442C5955DA@PN3P287MB0337.INDP287.PROD.OUTLOOK.COM>", "subject": "http://talos.tl1.tc5.ct4-5.ed.verdictsim.com/ TC_id_0365_9642 2025-07-21 06:35:46", "action": {"action": "move", "timestamp": "2025-07-21T06:36:01.079567128Z", "remediatedBy": "automatic", "publicApiClientId": "", "folder": "trash"}, "verdict": {"category": "spam", "detections": [{"technique": "Low content reputation", "type": "", "description": ""}, {"technique": "Malicious URL", "type": "url", "description": "http://talos.tl1.tc5.ct4-5.ed.verdictsim.com/"}, {"technique": "Frequent sender for recipient's domain", "type": "email_sender", "description": "automationuser1@etdcesautomation.com"}, {"technique": "Frequent sender for recipient", "type": "email_sender", "description": "automationuser1@etdcesautomation.com"}, {"technique": "Frequent sender", "type": "email_sender", "description": "automationuser1@etdcesautomation.com"}], "isAutoRemediated": true, "verdict": "spam", "timestamp": "2025-07-21T06:36:00.344258147Z", "reclassifiedBy": "automatic"}, "urls": [{"url": "http://talos.tl1.tc5.ct4-5.ed.verdictsim.com/"}]}, "tenantId": "07fa4225-ed36-48b0-b165-3468fa6605ef", "logType": "message", "logDate": "2025-07-21", "logHour": "06"}
- Reclassified Email
An email whose initial threat verdict was changed after further analysis via the ETD UI, API, or through Retrospective Verdicts.
{"message": {"eventType": "update", "id": "74572252-1c58-458e-b189-118a769c945d", "verdict": {"verdict": "phishing", "reclassifiedBy": "user", "timestamp": "2025-07-21T12:36:28.412718327Z", "user": "201faae8-19fb-4c33-b414-dfb09132e747"}, "internetMessageId": "<173950879335.1381575.7836783979393758791@example.com>"}, "tenantId": "07fa4225-ed36-48b0-b165-3468fa6605ef", "logType": "message", "logDate": "2025-07-21", "logHour": "12"}
- Remediated Email
An email that an administrator has manually acted upon to mitigate a threat. Actions include moving the email to quarantine, junk, or trash.
{"message": {"eventType": "update", "id": "49f405a3-910c-4e0b-ae23-1df81cb386bf", "action": {"action": "move", "folder": "trash", "remediatedBy": "manual", "publicApiClientId": "", "timestamp": "2025-07-21T12:36:50.76424181Z", "user": "201faae8-19fb-4c33-b414-dfb09132e747"}, "internetMessageId": "<171888171705.414181.15363077649421787144@example.com>"}, "tenantId": "07fa4225-ed36-48b0-b165-3468fa6605ef", "logType": "message", "logDate": "2025-07-21", "logHour": "12"}
JSON Response Details
The log files contain a series of JSON objects. Depending on the log type, the file will include a combination of Email, Verdict, and Action objects.
Note:
- To retrieve message event logs, set the
logTypesparameter in your request to["message"].- To retrieve multiple log types in a single call, provide them as an array. For example:
logTypes:["audit","message"].
Email Object
| Field | Description |
|---|---|
id |
A unique identifier for the email, assigned by ETD. |
timestamp |
The timestamp when the email was received by the system. |
clientIp |
The IP address of the client that sent the email. |
fromAddresses |
Sender email addresses from the From header. |
toAddresses |
Recipient email addresses from the To header. |
mailboxes |
Mailboxes to which the email was delivered. |
subject |
The subject line of the email. |
internetMessageId |
The unique Message ID of the email |
envelopeFrom |
The sender address from the envelope |
direction |
The direction of the email flow (e.g., incoming, outgoing). |
tenantId |
The unique identifier for your tenant. |
secureEmailGateway |
The name of the active Secure Email Gateway that processed the email. |
envelopeTo |
The recipient address from the envelope. |
serverIp |
The IP address of the receiving server. |
xOriginatingIP |
The IP address from the X-Originating-IP header. |
returnPath |
The email address specified in the Return-Path header. |
ccAddresses |
Recipient email addresses from the CC header. |
replyTo |
The email address specified in the Reply-To header. |
Verdict Object
| Field | Description |
|---|---|
timestamp |
The timestamp when this verdict was applied. |
internetMessageId |
The ID of the email this verdict applies to. |
verdict |
The specific verdict applied to the message. |
reclassifiedBy |
The method used for reclassification (Automatic, API, or Manual). |
user |
The ID of the user who performed a manual reclassification. |
publicApiClientId |
The Client ID of the public API client used during remediation. |
category |
A high-level category for the verdict applied to the message. |
rules |
Custom rules applied to emails. |
businessRisk |
The Business Risk of the latest verdict. |
technique |
The list specific detection techniques that contributed to the verdict. |
type |
The type of detection |
description |
A description of the detection or verdict. |
Action Object
| Field | Description |
|---|---|
timestamp |
The timestamp when the action was performed. |
internetMessageId |
The Unique ID of the email acted upon. |
tenantId |
Unique Tenant Identifier. |
action |
The action performed on the email. |
folder |
The folder to which the email was moved (e.g., trash, junk) |
user |
The ID of the user who performed a manual remediation. |
remediatedBy |
The method used to perform the remediation (API, Manual, or Automatic).) |
publicApiClientId |
The Client ID of the public API client used during remediation. |
Response Limitations
- The API response will contain a maximum of 200 download URLs.
- Each URL is limited to a maximum of 2048 characters.
- If a response exceeds these limits, additional entries will be truncated.
Steps to Enable the Logs
- Complete the authentication by following the steps mentioned on the Authenication page.
- Once you created your API credentials, navigate to the ETD UI and go to Administration > Business.
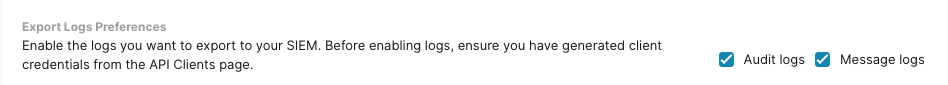
- In the Export Log Preferences section, select the checkboxes for the logs you wish to enable.
Endpoint
Americas API endpoint:
https://api.us.etd.cisco.com/v1/logs/downloadLinks
Europe API endpoint:
https://api.de.etd.cisco.com/v1/logs/downloadLinks
Australia API endpoint:
https://api.au.etd.cisco.com/v1/logs/downloadLinks
India API endpoint:
https://api.in.etd.cisco.com/v1/logs/downloadLinks
UAE API endpoint:
https://api.ae.etd.cisco.com/v1/logs/downloadLinks
Request/Response Samples
Blocked Connection Log API
Sample Blocked Connection Log API Request Using CURL:
curl --location --request POST 'https://api.in.etd.cisco.com/v1/logs/downloadLinks' \
--header 'x-api-key: apikeyTest' \
--header 'Authorization: Bearer <Bearer Token>' \
--header 'Content-Type: application/json' \
--data-raw '{"timeRange": ["2026-02-27T12","2026-02-27T14"], "logTypes":["connection"]
}'
Sample Response:
{
"data": {
"connection": [
"https://integration-logs-export-bucket.s3.amazonaws.com/tenant_id%3D94105fc6-320e-4210-91e1-86bef57fef27/log_date%3D2026-02-27/hour%3D12/log_type%3Dconnection/0001_part_00.1772195932.jsonl?x-etd-environment=integration&x-etd-client-id=65f9cd07-2501-48df-a54d-cfb4069c1e6d&x-etd-pre-sign-aws-request-id=b00d4106-2af8-4772-a928-19b3de1f6516&X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=ASIA6J4PVEVXDN42GK6P%2F20260302%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20260302T171906Z&X-Amz-Expires=3600&X-Amz-SignedHeaders=host&X-Amz-Security-Token=IQoJb3JpZ2luX2VjEMH%2F%2F%2F%2F%2F%2F%2F%2F%2F%2FwEaCXVzLWVhc3QtMSJHMEUCIAUoy4mklcsCyHtVIxb9EwWurs5WR8JlnI37BJ4tE5RJAiEA5BBIAgX1XTY9kDba49DgFK3oWCuHfuEQUmNihKPLSZIqngMIiv%2F%2F%2F%2F%2F%2F%2F%2F%2F%2FARADGgw5ODMzMTE5MTg0NDYiDB3BjWMSD171O75wCiryAthyGL%2BxcU6RApU%2BvmEbgR%2BJ7xAgDhKG42xsnWoUo3aMdXw3GQT1eGDvXdpyi9VgXuPAPr07YR2AzrTV0PFKHeWEQhfsM%2FkRslp3ZScKKvciGrW%2B8%2BD8xyU%2BFqoyvL%2FMSJFzkYngZJ0%2FsbLDUzpqCSXAsO1XYh5Jn8qmGNEBG0DsUBEvT3xV1j8DZSuyvsVTO6IN0Lj%2BfP6kCur%2Fr%2FqTVWHMyCG2HKbZs9%2Bz1OTpVnAN2bUtke3JtTzjSSuGri6ZPZSAcsm6T3Rb2pcTR0C264vu9VCWvW4mtWijdffZlBojdex4Af0XvlvXg5EV39N5hcZa608jIPmvoS8t%2BNw%2FVYx%2FwcJ6nHNUzQvD023FOmX8QVi4clJhxgmoxNxhd4%2BoUJRAzObsUdorH62%2BSiXoFh0eibzSoDlpQES4oYd0k8Nax%2B2a12NsKpIZEJgXtcL5ZMBQnNPtx%2FoTUFFoSEYEqiDoSVcGb5KRHjtsv1dCCj5hCvww1vOWzQY6nQEuKPhc6GvA35EjtIP1ggPqgyqXNIvoZBVRMs8yLX1hb1SM8tQHnuJDv5%2FDZi%2F6VfXR5ZqEi7oBsowj0098a3o9T%2BHNLzx5CuUf%2B5XqIpMvUtSdgX0GboHzXYqPefXZSnhd2mefBae8zkKCgpTD6nb5XJR%2BoU1wiNOCHUaqsn8RQ45a2HOtg0hQKdShpypoecJm4Pm1o46kqRWpzCDZ&X-Amz-Signature=878da4f1057d721ef3975770cf9c85004f51401ceb95fbbbaded1525a0efcd29"
]
}
}
Note:
- Blocked Connection log export starts 15 minutes after the feature is enabled in the UI.
- The maximum time range allowed for each API request is 3 hours.
- Links are valid for 1 hour and the log retention period is 30 days.
Audit Log API
Sample Audit Log API Request Using CURL:
curl --location --request POST 'https://api.in.etd.cisco.com/v1/logs/downloadLinks' \
--header 'x-api-key: apikeyTest' \
--header 'Authorization: Bearer <Bearer Token>' \
--header 'Content-Type: application/json' \
--data-raw '{"timeRange": ["2024-09-09T10","2024-09-09T12"], "logTypes":["audit"]
}'
Sample Response:
{
"data": {
"audit": [
"https://integration-logs-export-bucket.s3.amazonaws.com/tenant_id%3Dcb747c88-e177-4355-86c0-eec9d0e35cf7/log_date%3D2024-09-09/hour%3D11/log_type%3Daudit/0000_part_00.1725881165.json?x-etd-environment=integration&x-etd-client-id=768c11ae-edd7-40d5-86e1-b00218930c0c&x-etd-pre-sign-aws-request-id=&X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=ASIA6J4PVEVXFVH4JGVQ%2F20240909%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20240909T134616Z&X-Amz-Expires=3600&X-Amz-SignedHeaders=host&X-Amz-Security-Token=IQoJb3JpZ2luX2VjEDYaCXVzLWVhc3QtMSJGMEQCIF5GViTLiRXAuj37WoeL6Ls8J7btmGgcEo3Q623mE7ZrAiB8gslG2uvEhmO2VJEOO8ZKIQyTbm4zRXmpqknzNBqQhiqVAwheEAMaDDk4MzMxMTkxODQ0NiIM%2FH8nY27rcutHqt9DKvICz2Mn%2F8ns1hmcT0iJ2yuMHIIH4EUnwU42joDwd5i%2Frdx27WXdPj5JRonujAFdMz7uIhZP3pdaTCDYcsYIPrf3%2B2bSywRNyIE4uiWpAbQcVnBOYUtpBusW5WpNxQy%2BPwh8ApZtsjdnMWARDdBN1fI%2FhzzFSm329yAZ%2FzED2vCBdfZ%2FZG19TFe0JRGV8kOB1Wc30xcCEqWtZYEtfIxEwn1YpcQp1JfZoxsB1q9yi18Y%2F4jXURgVUyvsAniG0nezclJTR1ruH9LN6nBBG49rsGX38sL76ocYeHn0NFb0L2eusfl5jfIP5Ou4AYyV%2BRXItVEWmDgYKIakt%2B9Bpf167bh%2BhYDDOQLvJArDfsf2Q9iaHaawGFL076cMCwTczLXUWRMzAf4UEyltmSgcSCXitAZCz0jEjuzMbDUrqbm%2B2xocrpdVUAHy02CeKvHHr6IMgDg8QhqD0OsQqTByG3iBQcCL6kmXX2b%2BesyTHVUt7O7O6rNUzDDl5Pu2BjqeAehcExwQQmlgDEiixYn0PS41FNPEJsSmim4xIpWLj8d7A1PwcLU8napR5pMpPuzs2V71OCFQfFzq9varpkBaqNL5kdWEBRqLHA8TW1WYOhcdMtdV0f3G0GeR300EK0zkvfVi66IS5kmDsxRKzmGKKRG9C1iDPfS%2BLSM5%2FBVazMQWP8NIeC0frr6Vl1KDdbXAMWmodDbTL8fFzfMdLAJD&X-Amz-Signature=dd351f793f44856e9caff7341cf568a9d1e69c6aef2ab3d10ec17ff947bed11c",
"https://integration-logs-export-bucket.s3.amazonaws.com/tenant_id%3Dcb747c88-e177-4355-86c0-eec9d0e35cf7/log_date%3D2024-09-09/hour%3D11/log_type%3Daudit/0000_part_00.1725882962.json?x-etd-environment=integration&x-etd-client-id=768c11ae-edd7-40d5-86e1-b00218930c0c&x-etd-pre-sign-aws-request-id=&X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=ASIA6J4PVEVXFVH4JGVQ%2F20240909%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20240909T134616Z&X-Amz-Expires=3600&X-Amz-SignedHeaders=host&X-Amz-Security-Token=IQoJb3JpZ2luX2VjEDYaCXVzLWVhc3QtMSJGMEQCIF5GViTLiRXAuj37WoeL6Ls8J7btmGgcEo3Q623mE7ZrAiB8gslG2uvEhmO2VJEOO8ZKIQyTbm4zRXmpqknzNBqQhiqVAwheEAMaDDk4MzMxMTkxODQ0NiIM%2FH8nY27rcutHqt9DKvICz2Mn%2F8ns1hmcT0iJ2yuMHIIH4EUnwU42joDwd5i%2Frdx27WXdPj5JRonujAFdMz7uIhZP3pdaTCDYcsYIPrf3%2B2bSywRNyIE4uiWpAbQcVnBOYUtpBusW5WpNxQy%2BPwh8ApZtsjdnMWARDdBN1fI%2FhzzFSm329yAZ%2FzED2vCBdfZ%2FZG19TFe0JRGV8kOB1Wc30xcCEqWtZYEtfIxEwn1YpcQp1JfZoxsB1q9yi18Y%2F4jXURgVUyvsAniG0nezclJTR1ruH9LN6nBBG49rsGX38sL76ocYeHn0NFb0L2eusfl5jfIP5Ou4AYyV%2BRXItVEWmDgYKIakt%2B9Bpf167bh%2BhYDDOQLvJArDfsf2Q9iaHaawGFL076cMCwTczLXUWRMzAf4UEyltmSgcSCXitAZCz0jEjuzMbDUrqbm%2B2xocrpdVUAHy02CeKvHHr6IMgDg8QhqD0OsQqTByG3iBQcCL6kmXX2b%2BesyTHVUt7O7O6rNUzDDl5Pu2BjqeAehcExwQQmlgDEiixYn0PS41FNPEJsSmim4xIpWLj8d7A1PwcLU8napR5pMpPuzs2V71OCFQfFzq9varpkBaqNL5kdWEBRqLHA8TW1WYOhcdMtdV0f3G0GeR300EK0zkvfVi66IS5kmDsxRKzmGKKRG9C1iDPfS%2BLSM5%2FBVazMQWP8NIeC0frr6Vl1KDdbXAMWmodDbTL8fFzfMdLAJD&X-Amz-Signature=3a801877ef9e98bd39b9f1b9075b8db2497f5278e392033e56025873a1b42cdc",
"https://integration-logs-export-bucket.s3.amazonaws.com/tenant_id%3Dcb747c88-e177-4355-86c0-eec9d0e35cf7/log_date%3D2024-09-09/hour%3D11/log_type%3Daudit/0000_part_00.1725883852.json?x-etd-environment=integration&x-etd-client-id=768c11ae-edd7-40d5-86e1-b00218930c0c&x-etd-pre-sign-aws-request-id=&X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=ASIA6J4PVEVXFVH4JGVQ%2F20240909%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20240909T134616Z&X-Amz-Expires=3600&X-Amz-SignedHeaders=host&X-Amz-Security-Token=IQoJb3JpZ2luX2VjEDYaCXVzLWVhc3QtMSJGMEQCIF5GViTLiRXAuj37WoeL6Ls8J7btmGgcEo3Q623mE7ZrAiB8gslG2uvEhmO2VJEOO8ZKIQyTbm4zRXmpqknzNBqQhiqVAwheEAMaDDk4MzMxMTkxODQ0NiIM%2FH8nY27rcutHqt9DKvICz2Mn%2F8ns1hmcT0iJ2yuMHIIH4EUnwU42joDwd5i%2Frdx27WXdPj5JRonujAFdMz7uIhZP3pdaTCDYcsYIPrf3%2B2bSywRNyIE4uiWpAbQcVnBOYUtpBusW5WpNxQy%2BPwh8ApZtsjdnMWARDdBN1fI%2FhzzFSm329yAZ%2FzED2vCBdfZ%2FZG19TFe0JRGV8kOB1Wc30xcCEqWtZYEtfIxEwn1YpcQp1JfZoxsB1q9yi18Y%2F4jXURgVUyvsAniG0nezclJTR1ruH9LN6nBBG49rsGX38sL76ocYeHn0NFb0L2eusfl5jfIP5Ou4AYyV%2BRXItVEWmDgYKIakt%2B9Bpf167bh%2BhYDDOQLvJArDfsf2Q9iaHaawGFL076cMCwTczLXUWRMzAf4UEyltmSgcSCXitAZCz0jEjuzMbDUrqbm%2B2xocrpdVUAHy02CeKvHHr6IMgDg8QhqD0OsQqTByG3iBQcCL6kmXX2b%2BesyTHVUt7O7O6rNUzDDl5Pu2BjqeAehcExwQQmlgDEiixYn0PS41FNPEJsSmim4xIpWLj8d7A1PwcLU8napR5pMpPuzs2V71OCFQfFzq9varpkBaqNL5kdWEBRqLHA8TW1WYOhcdMtdV0f3G0GeR300EK0zkvfVi66IS5kmDsxRKzmGKKRG9C1iDPfS%2BLSM5%2FBVazMQWP8NIeC0frr6Vl1KDdbXAMWmodDbTL8fFzfMdLAJD&X-Amz-Signature=be15a339650d85055ce0d638ec0e16563d93385c1978f1bddea79f54faea9984"
]
}
}
Note:
- Audit log export starts 15 minutes after the feature is enabled in the UI.
- New log files are generated and made available for download every 15 minutes.
- The maximum time range allowed for each API request is 3 hours.
- Links are valid for 1 hour and the log retention period is 30 days.
Message Event Log API
Sample Message Event Log API Request Using CURL:
curl --location --request POST 'https://api.in.etd.cisco.com/v1/logs/downloadLinks' \
--header 'x-api-key: apikeyTest' \
--header 'Authorization: Bearer <Bearer Token>' \
--header 'Content-Type: application/json' \
--data-raw '{"timeRange": ["2024-09-09T10","2024-09-09T12"], "logTypes":["message"]
}'
Sample Response:
{
"data": {
"message": [
"https://integration-logs-export-bucket.s3.amazonaws.com/tenant_id%3D07fa4225-ed36-48b0-b165-3468fa6605ef/log_date%3D2025-07-16/hour%3D03/log_type%3Dmessage/integration-message-export-firehose-91-2025-07-16-03-55-52-1913e88c-288d-38b2-ac8d-88ba8f7bceb8.jsonl?x-etd-environment=integration&x-etd-client-id=3598b2c9-be32-4db5-846f-5e388cbda458&x-etd-pre-sign-aws-request-id=&X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=ASIA6J4PVEVXMIYHBO2A%2F20250716%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20250716T131331Z&X-Amz-Expires=3600&X-Amz-SignedHeaders=host&X-Amz-Security-Token=IQoJb3JpZ2luX2VjEEUaCXVzLWVhc3QtMSJHMEUCIQD0idrnQ6IkJe%2FftoJR1aVzypm81tF5zUhivrR03eFE%2FAIgOeQzMgdPNMR7Yf81kUXPZAw8FpYjA%2FDkgHyWHA2C4%2FoqlQMIXhADGgw5ODMzMTE5MTg0NDYiDIOIcRD%2BYELXqaYbHSryAoe6LeprFCaYFUrf5yZkKUvQ08gUGM1OA3vrsWQ3a3wWeqxJUWwXCZwQo9ClA1ZV8IRvOo2dx0LhpJVb2I2FQoQE%2B5tfBF4a57r1sInIhMEL9WcGo6DBcsUWk7blVSdaQRR4cN%2FdzmJM9bFiVgWbtXhHk44Y6J%2F1mjMrCtRyZOPg7bn%2FgXD%2BnVlI8qpTXHZnxZYpgSfXNOcBWOiHczY9JTkSYU7KRofLV0GNjJXYCMBc3QQCiAGQi7wCZGCZsBWikz9INrAglSPt%2B%2BrY%2F1x3XbNAGL6JYx%2Bt%2BF0dIFatSSQwze%2BPkf4nulibD48rGiUEfQcVhppoZKth5vV%2FFFfIqT5npJXgqvjO30mFhXjURzQ%2FvqNhPRF1MpX3a17Oxdj8IpQPmFkX7eidInlsZCJGXipawN7cdcwk8dmnmzaJOlkbWP9PdJ5LIy021WDl%2FYiGd8dDkz8Tdpq00tnFn0O7cuyq7k95%2F7%2ByJ0wyDec2CWKBdiEw0bPewwY6nQGS6e5p3K90rQxd%2B2VCOs%2FlpfjT%2FmbVYG9JB6CpjqcS%2FdYboIEdVkfkf8ybOYh6VTHh%2FP1fgL34TRPamV4MxOD%2BA4ZkSInT5Q%2FwBNuEZWhjg4k2YdkqXL4xRwbqS5KBYH%2F3RxVrFeznHuZwzJmDFOylDwAOtOjL%2BrodNHBXDYSoZB1Z9DGpX4WmFCOVgVUTJJ3wOAUd%2Blff6p7ASEbc&X-Amz-Signature=d9889362ce7070108e5db51b6fbccc116872b84a3c47905801781f01d84313e8"
]
}
}
Note:
- Message Event log export starts 20 minutes after the feature is enabled in the UI.
- The maximum time range allowed for each API request is 3 hours.
- Links are valid for 1 hour and the log retention period is 30 days.
Error Responses
The API uses standard HTTP status codes to indicate the success or failure of a request.
| Code | Message | Description |
|---|---|---|
400 |
Bad Request |
The provided JWT token is invalid or malformed. Please generate a new token using valid client credentials. |
400 |
Bad Request |
The timestamp range cannot extend into the future beyond the current hour. The response will indicate the exact time limit. |
400 |
Invalid daterange |
The end date in the request is not later than the start date. Ensure the start of the range is chronologically before the end. |
400 |
Invalid daterange |
The specified time range is too far in the past. Timestamps cannot be older than 30 days. |
400 |
Invalid daterange |
The duration between the start and end times exceeds the maximum allowed period of 3 hours. |
400 |
Unable to deserialize request body |
The request body is not valid JSON or does not conform to the expected structure. Check for syntax errors or missing/invalid fields. |
401 |
Token expired, generate new token to proceed |
The provided JWT token has expired. You must generate a new token to continue making requests. |
403 |
Forbidden |
The required x-api-key header is missing from your API request. |
429 |
Limit exceeded |
You have exceeded the API rate limit or your daily usage quota. Please contact our support team to request an increase. |
503 |
Service temporarily unavailable |
Service is temporarily unavailable. Please try again after a few minutes. |