ASAv
Overview
The ASAv is Cisco's Adaptive Security Virtual Appliance. It is the same VM image that Cisco licenses as a virtual firewall in production environments. The ASAv image runs in demo mode in CML without any additional licensing.
For more details about ASAv, refer to the following resources:
Limitations
- The ASAv is performance limited when forwarding traffic. Achieved throughput is ~180Kbits/s when passing traffic through one ASAv device.
- In unlicensed state firewall connections are limited to 100. Once licensed with any entitlement, the connections go to the platform limit.
Features Tested with CML
Each CML release is tested with the bundled version of ASAv. The tests validate the following features:
| Test Name | Result |
|---|---|
| ping | Pass |
| Routing | Pass |
| PAT | Pass |
| Static NAT | Pass |
| Access Control | Pass |
| Stateful Inspection | Pass |
The lab used for the tests is ASAv Feature Tests, which is one of the sample labs included with CML on the Tools > Sample Labs page.
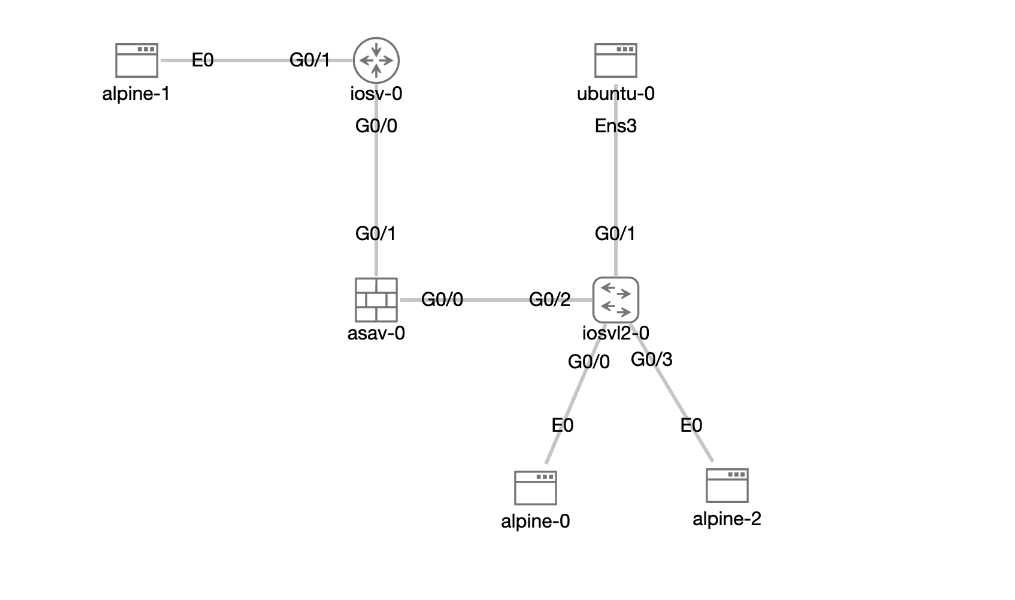
Ping
- Sending ICMP Echo packets to the neighbor IP
- Neighbor devices (inside and outside) are reachable
ciscoasa# ping 192.168.1.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.5, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/10 ms
Routing
- Default static route added
ciscoasa# show route
S* 0.0.0.0 0.0.0.0 [1/0] via 203.0.113.1, outside
C 192.168.1.0 255.255.255.0 is directly connected, inside
L 192.168.1.1 255.255.255.255 is directly connected, inside
C 203.0.113.0 255.255.255.0 is directly connected, outside
L 203.0.113.2 255.255.255.255 is directly connected, outside
- Traffic for unknown destination is successfully routed to next router
- Verification: Remote host (209.165.202.3) is reachable from ASA
ciscoasa# ping 209.165.202.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 209.165.202.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/10 ms
Static NAT
- Static NAT configured to make branch-server accessible from outside
ciscoasa# show xlate
1 in use, 1 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from inside:192.168.1.6 to outside:203.0.113.3
flags s idle 0:03:43 timeout 0:00:00
- Branch-server (192.168.1.6) is accessible from outside network on the public IP address 203.0.113.3
- Verification: After allowing HTTP traffic to branch-server, the server is accessible on the public address of 203.0.113.3
alpine-1:~$ nc -zv 203.0.113.3 80
203.0.113.3 (203.0.113.3:80) open
PAT
- IP addresses of internal hosts (except branch-server) are translated to a single address of 203.0.113.2
- Show
xlateoutput shows the translations after sending ICMP traffic from two internal hosts to external router
ciscoasa# show xlate
3 in use, 3 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from inside:192.168.1.6 to outside:203.0.113.3
flags s idle 0:06:19 timeout 0:00:00
ICMP PAT from inside:192.168.1.5/1 to outside:203.0.113.2/1 flags ri idle 0:00:18 timeout 0:00:30
ICMP PAT from inside:192.168.1.7/1 to outside:203.0.113.2/58305 flags ri idle 0:00:06 timeout 0:00:30
- Verification: Ping from internal host to external router. Debug ICMP on external router shows packets coming from translated address.
Access Control Policy
- Only HTTP traffic allowed from outside to internal server
- All other traffic from outside dropped
- Verification: External device tries to connect to internal server. Only connection to port 80 (HTTP) is successful.
HTTP (Port 80)
- Internal server listens on port 80
cisco@ubuntu:~$ sudo nc -l 80
- External client can access internal server on port 80
alpine-1:~$ nc -zv 203.0.113.3 80
203.0.113.3 (203.0.113.3:80) open
Other ports (e.g., 81)
- Internal server listens on port 81
cisco@ubuntu:~$ sudo nc -l 81
- External client cannot reach server on port 81 because ASA is dropping packets
- Client does not receive any response (ASA is just dropping packets) and the operation times out
alpine-1:~$ nc -zv 203.0.113.3 81
nc: 203.0.113.3 (203.0.113.3:81): Operation timed out
Stateful Inspection
- ICMP inspection enabled on ASA
- Returning ICMP Echo Reply messages allowed in
cisco@ubuntu-0:~$ ping 209.165.202.3
PING 209.165.202.3 (209.165.202.3) 56(84) bytes of data.
64 bytes from 209.165.202.3: icmp_seq=1 ttl=63 time=4.22 ms
64 bytes from 209.165.202.3: icmp_seq=2 ttl=63 time=3.82 ms
64 bytes from 209.165.202.3: icmp_seq=3 ttl=63 time=4.39 ms
64 bytes from 209.165.202.3: icmp_seq=4 ttl=63 time=4.53 ms
- ICMP requests initiated from outside are still not allowed in
PING 203.0.113.3 (203.0.113.3): 56 data bytes
^C
--- 203.0.113.3 ping statistics ---
7 packets transmitted, 0 packets received, 100% packet loss
alpine-1:~$