Cisco Open NX-OS supports Linux containers (LXC) natively on the platform. This allows customers and third-party application developers the ability to add custom functionality directly to the switch, and host their applications on the device in a secure, isolated environment:
The benefits of utilizing containers include:
- Isolated and secure application execution environments
- Resource and process isolation. Resources can be controlled, limiting the amount of CPU, memory, storage, and network bandwidth allocated to the container environment.
- Independent software release cycles
- Customers and third-party developers can create their own open-source based custom applications, independent of the traditional NX-OS software release cycle.
- Decreased time to market for custom-built features.
- Network Operation Optimization
- Custom applications running within the container environment can reduce the need to use separate software solutions or interfaces. An example of this is a packet capture tool running locally on the device directly within the container, or applications that can monitor and control the switch.
Open NX-OS Container Architecture
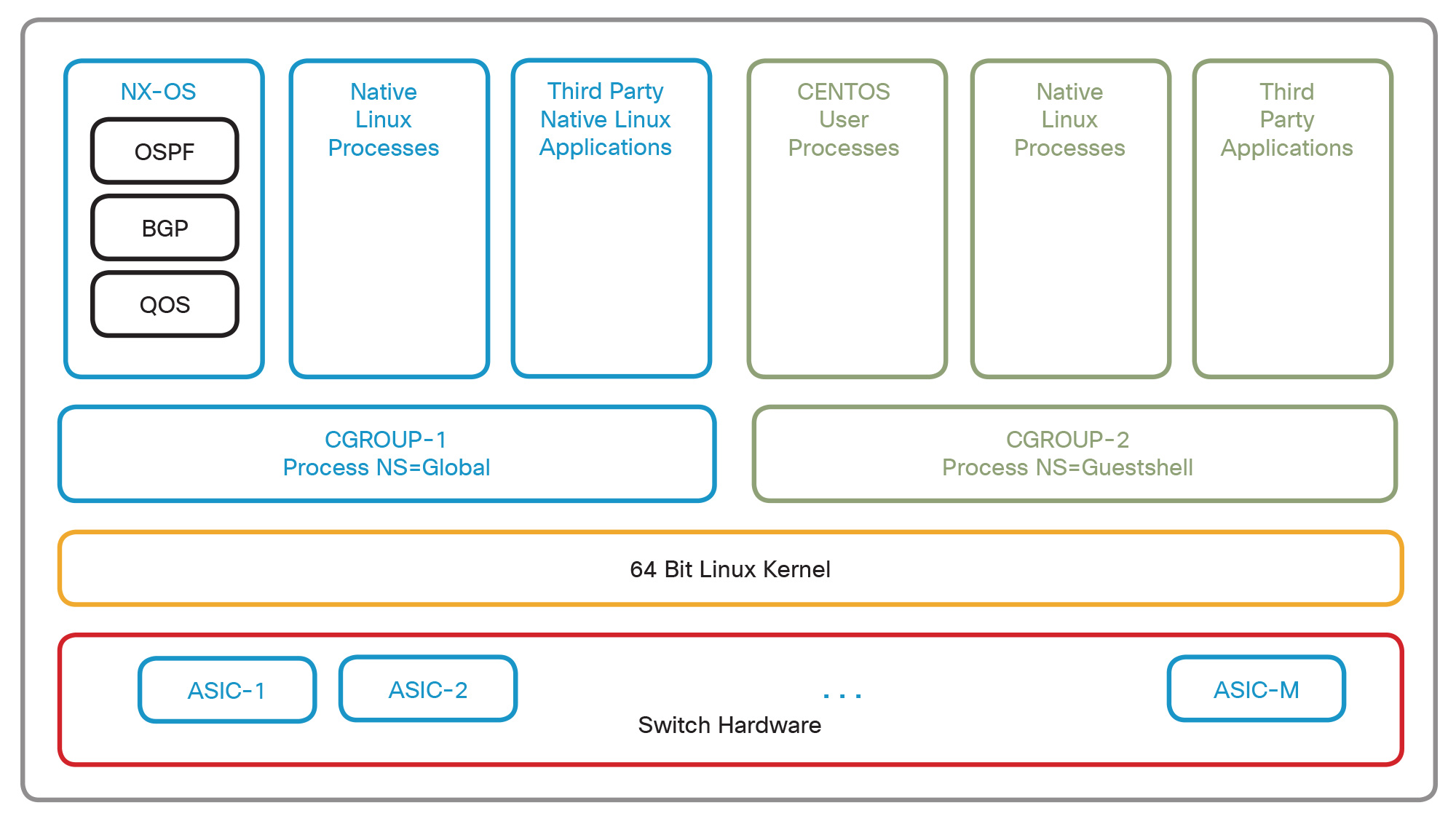
The Linux kernel provides built-in resource controls (cgroups) which allow for the isolation and limiting of process, memory and filesystem resources. The isolation provided is transparent, so there is no process-scheduling overhead.
The processes within a container are given their own namespace which does not overlap with native NX-OS processes or any other containers that may be present on the system. This ensures that NX-OS processes are protected from the containerized guest processes. This separation is provided directly within the kernel.
It's worth mentioning that there are significant differences between containers and full hypervisor environments. Since they are implemented directly by the host kernel, only Linux containers can be supported. Even if the Linux distributions used within containers differ, they will still use the underlying host's kernel and libraries. Hypervisor-based virtual machines differ from containers in that each VM operates as an independent entity: there is no reliance on an up-stream kernel.
Differences in Container and Hypervisor-based Architectures
