Installing the pxGrid SDK
Download the SDK file and untar the file. You should see the following folders:

The ../samples/cert folder will contain the sample certificates for running the pxGrid scripts.
The ../samples/bin folder will contain the sample pxGrid Java scripts. The cgcl folder will contain the pxGrid C libraries.
- ANCAction_query.sh
- alpha.jks
- alpha_root.jks
- capability_query.sh
- common.sh
- core_subscribe.sh
- endpointprofile_query.sh
- endpointprofile_subscribe.sh
- eps_quarantine.sh
- eps_unquarantine.sh
- generic_action_client.properties
- generic_client.sh
- generic_publisher.properties
- generic_subscriber.properties
- identity_group_download.sh
- identity_group_query.sh
- identity_group_subscribe.sh
- multigroupclient.sh
- propose_capability.sh
- securitygroup_query.sh
- securitygroup_subscribe.sh
- session_download.sh
- session_query_by_ip.sh
- session_sub_download.sh
- session_subscribe.sh
- sxp_download.sh
- sxp_subscribe.sh
In order to run these scripts, the Oracle Java Development Kit is required.
Using Self-signed Certificates for pxGrid Client Testing
Self-signed certificates are an alternative to Sample certificates.
Self-signed certificates were used for testing the pxGrid client with ISE pxGrid. The following procedure is used for self-signed certificates with pxGrid script testing:
- Generate a private key, for example alpha.key, for the pxGrid client.
Generate a private key
openssl genrsa -out alpha.key 4096
Generating RSA private key, 4096 bit long modulus
..................++
.............................++
e is 65537 (0x10001)
- Generate the self-signed CSR (alpha.csr) request and provide a challenge password.
Generate the self-signed CSR request
openssl req -new -key alpha.key -out alpha.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:
State or Province Name (full name) [Some-State]:
Locality Name (eg, city) []:
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:cisco123
An optional company name []:LAB
Note: Keeping the same password throughout this document is easier to maintain and cuts down on errors.
- Generate self-signed cert public-key pair certificate (for example alpha.cer).
Generate self-signed cert public-key pair certificate
openssl req -x509 -days 365 -key alpha.key -in alpha.csr -out alpha.cer
- A PKCS12 file (for example, alpha.p12) will be created from the private key.
PKCS12 file created from the private key
openssl pkcs12 -export -out alpha.p12 -inkey alpha.key -in alpha.cer
Enter Export Password: cisco123
Verifying - Enter Export Password: cisco123
- The alpha.p12 will be imported into the identity keystore (for example, alpha.jks). The keystore filename can be a random filename with a .jks extension. This will serve as the keystoreFilename and associated keystorePassword in the pxGrid scripts.
alpha.p12 will be imported into the identity keystore
keytool -importkeystore -srckeystore alpha.p12 -destkeystore alpha.jks -srcstoretype PKCS12
Enter destination keystore password: cisco123
Re-enter new password: cisco123
Enter source keystore password: cisco123
Entry for alias 1 successfully imported.
Import command completed: 1 entries successfully imported, 0 entries failed or cancelled
- Export only the public ISE Identity certificate into the pxGrid client, note that this will be in .pem format. You can rename the file with .pem extension to make it easier to read, in this example the file was renamed to isemnt.pem.
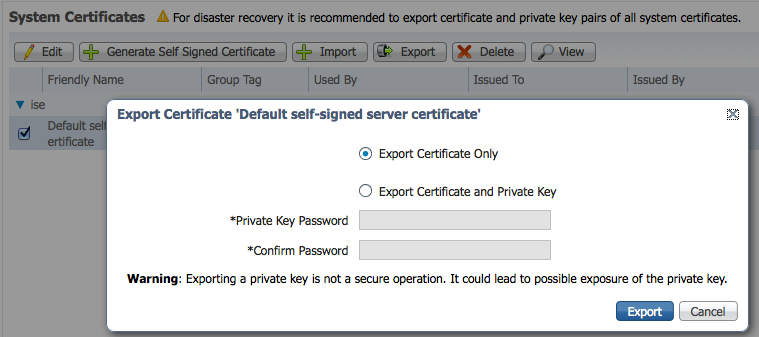
- Convert the .pem file to .der format.
Convert the .pem file to .der format
openssl x509 -outform der -in isemnt.pem -out isemnt.der
- Add the ISE identity cert to the identity keystore. This will be used for securing bulk session downloads from the ISE MNT node when running the pxGrid session download scripts.
Add the ISE identity cert to the identity keystore
keytool -import -alias mnt1 -keystore alpha.jks -file isemnt.der
Enter keystore password: cisco123
Owner: CN=ise.lab6.com
Issuer: CN=ise.lab6.com
Serial number: 548502f500000000ec27e53c1dd64f46
Valid from: Sun Dec 07 17:46:29 PST 2014 until: Mon Dec 07 17:46:29 PST 2015
Certificate fingerprints:
MD5: 04:7D:67:04:EC:D2:F5:BC:DC:79:4D:0A:FF:62:09:FD
SHA1: 5A:7B:02:E4:07:A1:D2:0B:7D:A5:AE:83:27:3B:E7:33:33:30:1E:32
SHA256: C4:21:6C:6F:5B:06:F3:2C:D7:26:35:CB:BE:2B:1B:FF:0E:EE:09:91:F6:B6:54:0C:6F:63:CB:43:1F:77:F2:37
Signature algorithm name: SHA1withRSA
Version: 3
Extensions:
# 1: ObjectId: 2.5.29.19 Criticality=false
BasicConstraints:[
CA:true
PathLen:2147483647
]
# 2: ObjectId: 2.5.29.37 Criticality=false
ExtendedKeyUsages [
serverAuth
clientAuth
]
# 3: ObjectId: 2.5.29.15 Criticality=false
KeyUsage [
DigitalSignature
Key_Encipherment
Key_Agreement
Key_CertSign
]
# 4: ObjectId: 2.16.840.1.113730.1.1 Criticality=false
NetscapeCertType [
SSL server
]
# 5: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: C4 F3 1A 9E 7B 1B 14 4F 51 9E A4 88 33 07 7A AC .......OQ...3.z.
0010: 75 37 36 D4 u76.
]
]
Trust this certificate? [no]: yes
Certificate was added to keystore
- Import the pxGrid client certificate into the identity keystore.
Import the pxGrid client certificate into the identity keystore
keytool -import -alias pxGridclient1 -keystore alpha.jks -file alpha.cer
Enter keystore password:
Certificate already exists in keystore under alias \<1\>
Do you still want to add it? [no]: n
Certificate was not added to keystore
Note: If you receive the following message that the certificate was already added to a pre-existing keystore, you can reply no and still be okay. yes is selected to verify that the certificate was added later on.
- Import the ISE identity cert into the trust keystore (i.e. alpha_root.jks). This will serve as the truststore Filename and truststore Password for the pxGrid scripts.
Import the ISE identity cert into the trust keystore
keytool -import -alias root1 -keystore alpha_root.jks -file isemnt.der
Enter keystore password:
Re-enter new password:
Owner: CN=ise.lab6.com
Issuer: CN=ise.lab6.com
Serial number: 548502f500000000ec27e53c1dd64f46
Valid from: Sun Dec 07 17:46:29 PST 2014 until: Mon Dec 07 17:46:29 PST 2015
Certificate fingerprints:
MD5: 04:7D:67:04:EC:D2:F5:BC:DC:79:4D:0A:FF:62:09:FD
SHA1: 5A:7B:02:E4:07:A1:D2:0B:7D:A5:AE:83:27:3B:E7:33:33:30:1E:32
SHA256: C4:21:6C:6F:5B:06:F3:2C:D7:26:35:CB:BE:2B:1B:FF:0E:EE:09:91:F6:B6:54:0C:6F:63:CB:43:1F:77:F2:37
Signature algorithm name: SHA1withRSA
Version: 3
Extensions:
# 1: ObjectId: 2.5.29.19 Criticality=false
BasicConstraints:[
CA:true
PathLen:2147483647
]
# 2: ObjectId: 2.5.29.37 Criticality=false
ExtendedKeyUsages [
serverAuth
clientAuth
]
# 3: ObjectId: 2.5.29.15 Criticality=false
KeyUsage [
DigitalSignature
Key_Encipherment
Key_Agreement
Key_CertSign
]
# 4: ObjectId: 2.16.840.1.113730.1.1 Criticality=false
NetscapeCertType [
SSL server
]
# 5: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: C4 F3 1A 9E 7B 1B 14 4F 51 9E A4 88 33 07 7A AC .......OQ...3.z.
0010: 75 37 36 D4 u76.
]
]
Trust this certificate? [no]: yes
Certificate was added to keystore
- Upload the pxGrid client public certificate (alpha.cer) into the ISE trusted certificate store.
- Select Administration > Certificate Management > Trusted Certificates > upload the alpha.cer to the ISE pxGrid node.
- Copy the identity keystore (alpha.jks) and trust keystore (alpha_root.jks) into the ../samples/bin/.. folder.
Testing pxGrid Client and ISE pxGrid Node
Run the multigroupclient pxGrid script file to register the pxGrid client to the ISE pxGrid node.
./multigroupclient.sh -a 192.168.1.23 -u SIM01 -k alpha.jks -p cisco123 -t alpha_root.jks -q cisco123