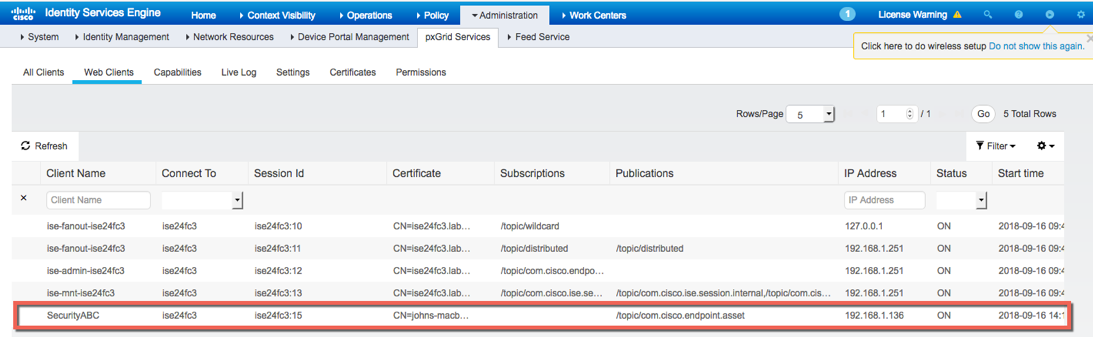
pxGrid Context-In Threat Example
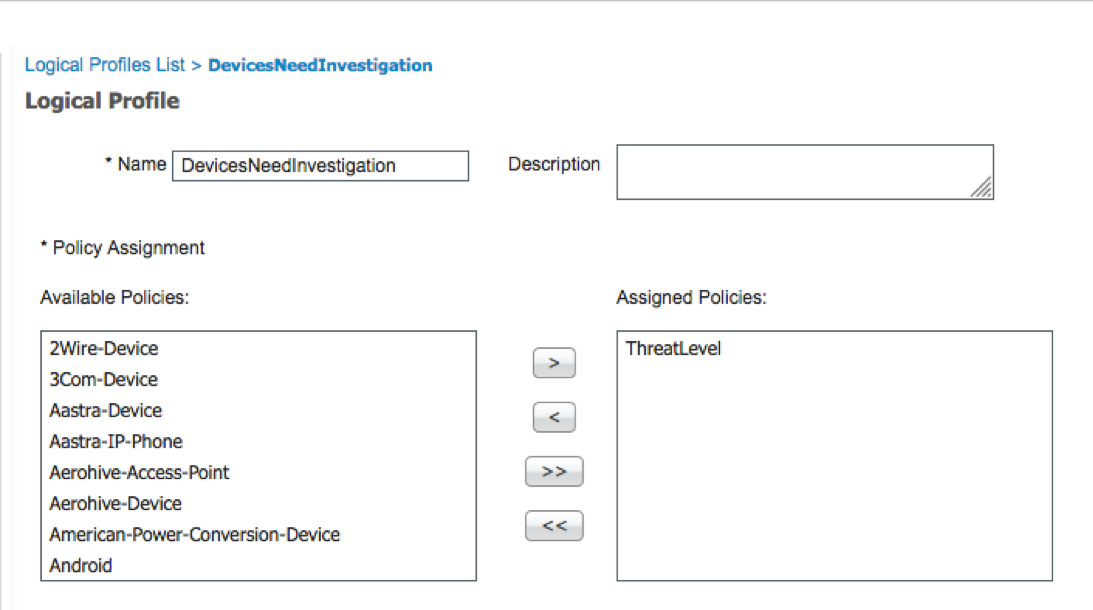
Select Policy->Profiling->Profiling Policies->Add name, add the Custom Attribute ThreatLevel with a combination of the endpoint MAC address

Select Policy->Logical Profiles->Add DevicesNeedInvestigation and assign the ThreatLevel policy
when you run the code you should see the following output:
------ config ------
hostname = ise24fc3.lab10.com
nodename = SecurityABC
password = (not specified)
description = (not specified)
keystorefilename = /Applications/sdk24/pxgrid-sdk-2.0.0.14/samples/bin/sdk24.jks
keystorepassword = Cisco123
truststorefilename = /Applications/sdk24/pxgrid-sdk-2.0.0.14/samples/bin/sdk24root.jks
truststorepassword = Cisco123
--------------------
10:18:47.956 [main] INFO com.cisco.pxgrid.samples.ise.PxgridControl - AccountActivate request={}
10:18:48.721 [main] INFO com.cisco.pxgrid.samples.ise.PxgridControl - AccountActivate response={"accountState":"ENABLED","version":"2.0.0.13"}
10:18:48.721 [main] INFO com.cisco.pxgrid.samples.ise.ContextInPublishing - pxGrid controller version=2.0.0.13
10:18:48.726 [main] INFO com.cisco.pxgrid.samples.ise.PxgridControl - ServiceRegister request={"name":"com.cisco.endpoint.asset","properties":{"wsPubsubService":"com.cisco.ise.pubsub","assetTopic":"/topic/com.cisco.endpoint.asset"}}
10:18:48.900 [main] INFO com.cisco.pxgrid.samples.ise.PxgridControl - ServiceRegister response={"id":"1d4104cf-bfa0-4644-89f0-9e9a6ec2ecf4","reregisterTimeMillis":300000}
10:18:48.904 [main] INFO com.cisco.pxgrid.samples.ise.PxgridControl - ServiceLookup request={"name":"com.cisco.ise.pubsub"}
10:18:48.917 [main] INFO com.cisco.pxgrid.samples.ise.PxgridControl - ServiceLookup response={"services":[{"name":"com.cisco.ise.pubsub","nodeName":"ise-pubsub-ise24fc3","properties":{"wsUrl":"wss://ise24fc3.lab10.com:8910/pxgrid/ise/pubsub"}}]}
10:18:48.917 [main] INFO com.cisco.pxgrid.samples.ise.ContextInPublishing - wsUrl=wss://ise24fc3.lab10.com:8910/pxgrid/ise/pubsub
10:18:48.918 [main] INFO com.cisco.pxgrid.samples.ise.PxgridControl - AccessSecret request={"peerNodeName":"ise-pubsub-ise24fc3"}
10:18:49.081 [main] INFO com.cisco.pxgrid.samples.ise.PxgridControl - AccessSecret response={"secret":"FyXCIMdlntNqBkz2"}
10:18:49.942 [Grizzly(1)] INFO com.cisco.pxgrid.samples.ise.StompPubsubClientEndpoint - WS onOpen
10:18:49.965 [main] INFO com.cisco.pxgrid.samples.ise.StompPubsubClientEndpoint - STOMP CONNECT host=ise24fc3.lab10.com
10:18:49.973 [Grizzly(1)] INFO com.cisco.pxgrid.samples.ise.StompPubsubClientEndpoint - STOMP CONNECTED version=1.2
10:18:50.003 [pool-1-thread-1] INFO com.cisco.pxgrid.samples.ise.StompPubsubClientEndpoint - STOMP SEND topic=/topic/com.cisco.endpoint.asset
press <enter> to disconnect...
10:18:55.004 [pool-1-thread-1] INFO com.cisco.pxgrid.samples.ise.StompPubsubClientEndpoint - STOMP SEND topic=/topic/com.cisco
Select Operations->RADIUS->Livelogs

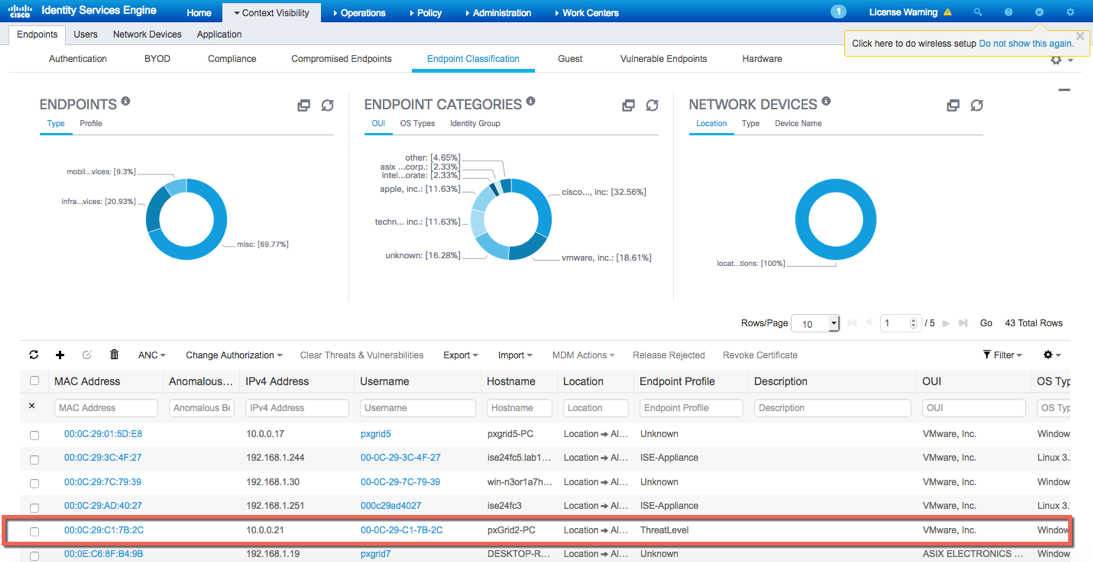
Select Context Visibility->Endpoints->Endpoint Classification
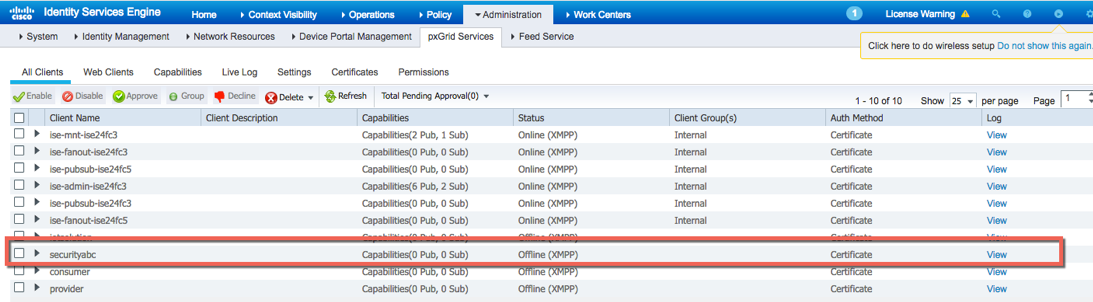
Select Administration->pxGrid Services, see the SecurtiyABC vendor register
Select Administration->pxGrid Services->Web Clients