WiFi Hawk Features
- Quick Index view
- Event Flow
- Histograms - Client
- Histograms - AP
- Detecting easy to miss problems
- Sleeping Patterns
- Client Probing
- Client High Retries
- Client Bi-directional traffic
- Protocol Errors
- Easily detect Radio Hangs
- Malformed beacons
- Association Mismatch
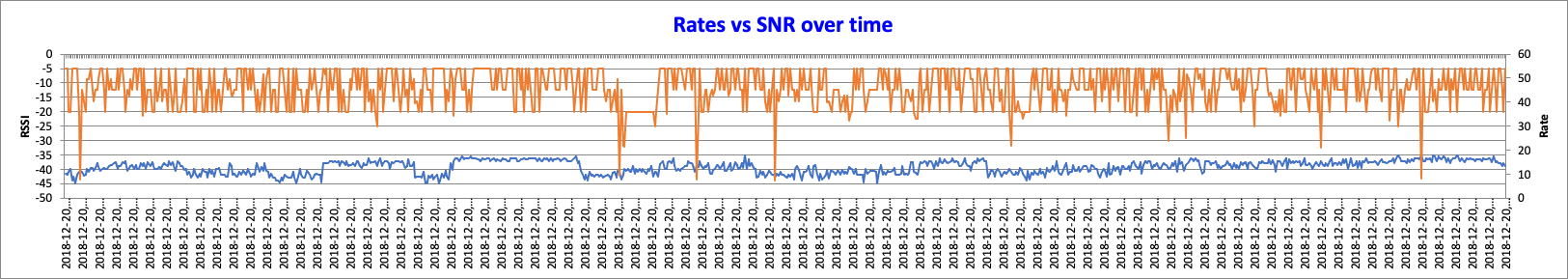
- Data rates vs SNR
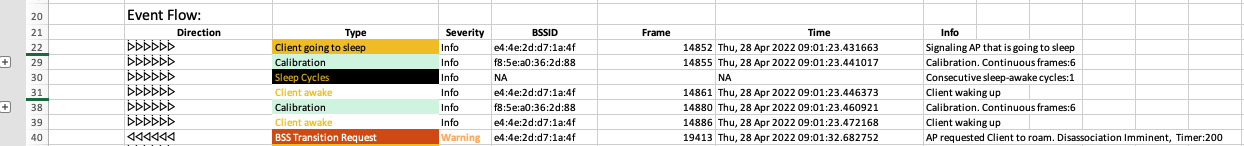
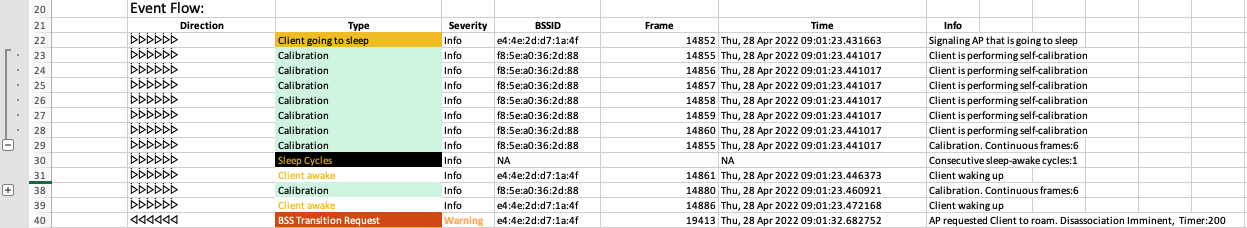
- Collapsed view of repetitive frames
- Interesting action frames highlighted
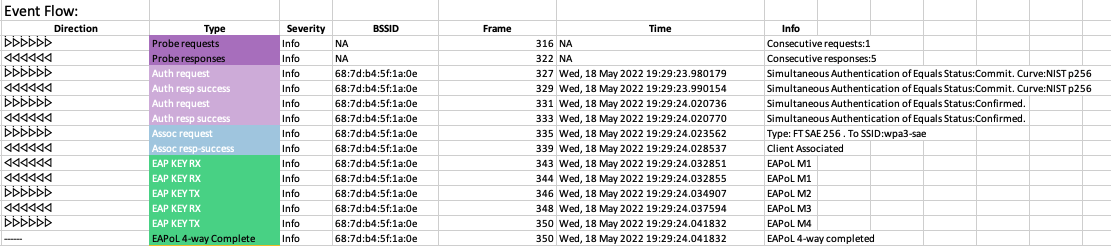
- SAE Support
- PMKID count sent on association/reassociation requests
- Per TID bidirectional traffic notification
- Detection of unprotected Action frames when PMF is in use
- Radar Event
- Alert for RTS floods
- EAP Identity displayed
Quick Index view
List of BSSIDs (APs) and clients active during the capture
Quick glance on who is having problems
Last known state for each client (probing, auth, full traffic, etc)
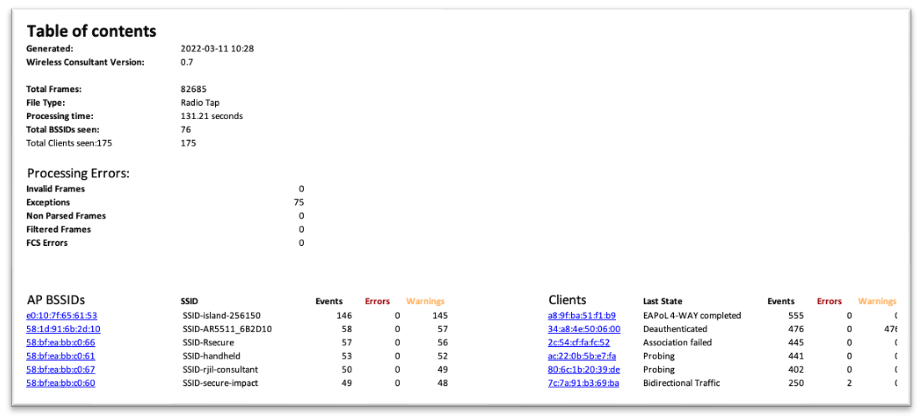
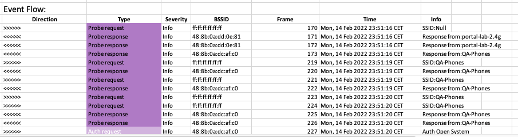
Event Flow
Color coded events registered per device
Summary of repeated items for a more concise view
Quick location in capture of important issues (frame/time)
Added information for better understanding
Translation of reason codes, failures, EAP types, etc
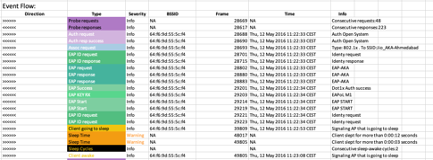
Histograms - Client
Get quick glance on signal levels, rates and QoS marking received and transmitted by client
Supported on Radiotap and Peekremote (AP sniffer) file formats
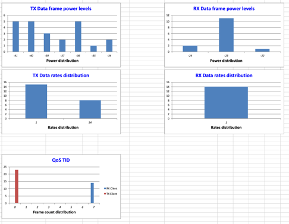
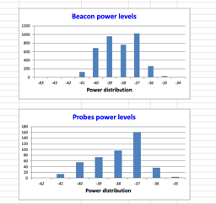
Histograms - AP
- Compare beacon vs probe power levels to detect anomalies
Detecting easy to miss problems
Simplify finding issues across large captures
Unencrypted traffic leak (client/AP)
Beacon loss
High co-channel
Incorrect data rates
![]()

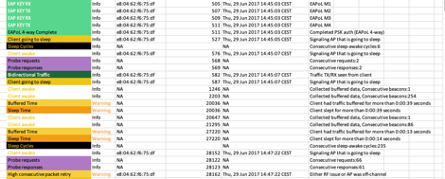
Sleeping Patterns
Follow sleeping/awake cycles for each client
Detect when there is buffered data (beacons/AID)
Get warning when client has not received traffic for a long time
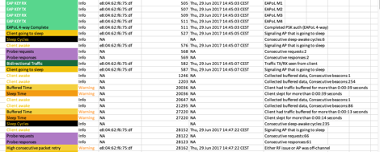
Client Probing
Get what the client is "interested in"
Probe activity is summarized by default
Verbose option to get all details

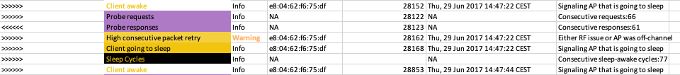
Client High Retries
Event reported when there are more than 10 consecutive retries
Detect if it is happening on regular intervals
Useful for Spectrum Intelligence impact or bad RF scenarios
Client Bi-directional traffic
Get the point when traffic to and from client has been detected
Independent of client auth state machine: needs to work on incomplete captures or frame loss scenarios
Limitations: Peekremote (ap sniffer) may not see MCS traffic
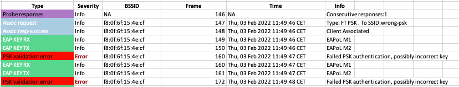
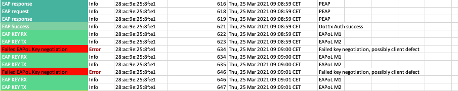
Protocol Errors
Detect invalid TID TX/RX
Wrong CCMP key index
EAPoL Negotiation errors
Failed PSK authentications (wrong key)
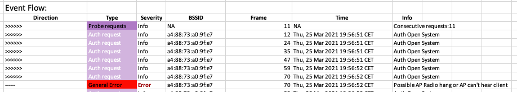
Easily detect Radio Hangs
- AP is beaconing, but no responses to client
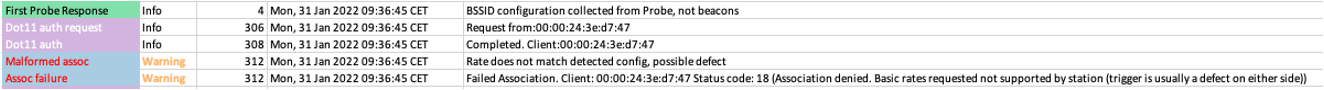
Malformed beacons
Detect spot errors that can trigger client disconnects
No Rate IE
No SSID IE
Interval variations
![]()
Association Mismatch
- Data rates not matching between probes, beacons and association response
- Controller side defect
Data rates vs SNR
- Visualize how data rates evolve over time compared to SNR value
- There are some limitations, depending on the file type, that may limit the information displayed
Collapsed view of repetitive frames
- Special summarisation handling of probe request/responses and calibration frames to show summary event
- Full details available if needed, just by clicking the + sign on the summary row
Interesting action frames highlighted
- Key Action frames, like Neighbour reports and client steering are displayed in client flow table

SAE Support
- Displays SAE auth process
- Information on Curve type negotiated
PMKID count sent on association/reassociation requests
- Useful to detect OKC/SAE, etc fast roaming scenarios
- Error report in case the PMKID is rejected by authenticator

Per TID bidirectional traffic notification
- Displays the point when bidirectional traffic for specific TIDs is seen
- Useful for voice traffic analysis
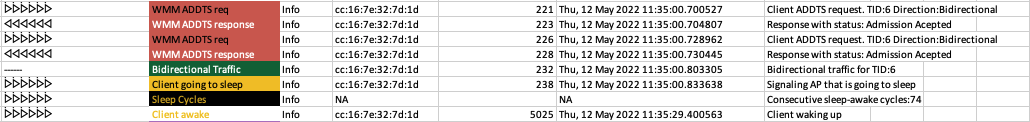
Detection of unprotected Action frames when PMF is in use
- Generates warning if client is sending Action frames without encryption, even when PMF was negotiated
- This is to spot client side defect, that was causing severe performance problems as Block ACK policies were not properly negotiated
- Detection also works for AP sent frames, and it will use 802.11 list of "what should be protected" to flag it per action frame type
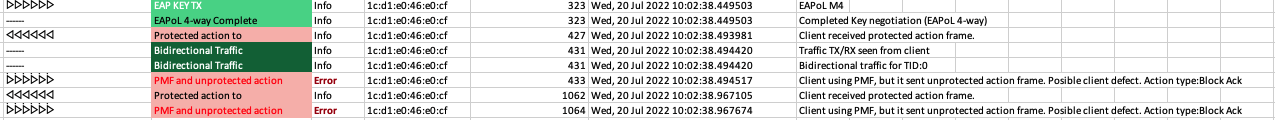
Radar Event
- Detects Channel Switch Announcement, typically generated during radar event
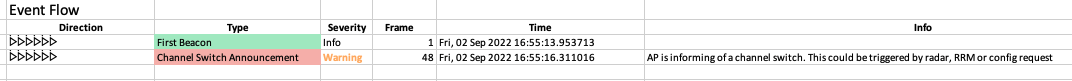
EAP Identity displayed
- For EAP ID request and response, we now include the external identity provided by the devices
