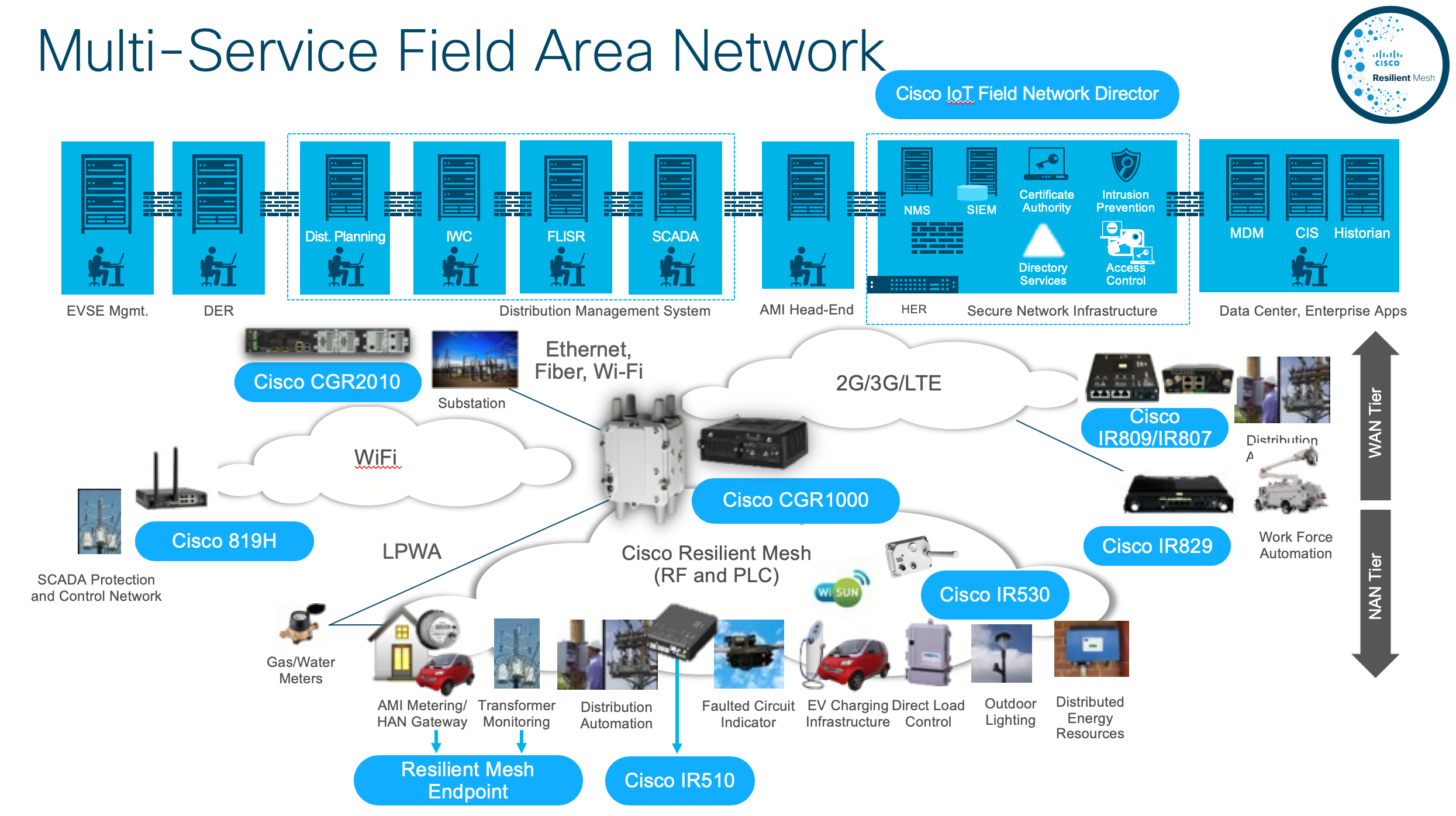
Architecture
The FAN is a two-tier architecture that includes a Neighborhood Area Network (NAN) that interconnects, either directly through Ethernet or Serial interfaces or through IEEE 802.15.4g/e RF Mesh, a range of devices such as a cluster of smart meters. These devices interconnect with a series of FAN routers, and a Wide Area Network (WAN). The WAN connects the FAN routers directly to a system control tier or through the substation network.
End-to-End Architecture
The Cisco FAN portfolio consists of outdoor and indoor Cisco 1000 Series Connected Grid Routers (CGR 1000 Series) and the Connected Grid RF Mesh (IEEE 802.15.4g/e) standards-based IPv6 reference designs to enable large-scale IP connectivity for endpoints such as smart meters, sensors, and EV charging stations.
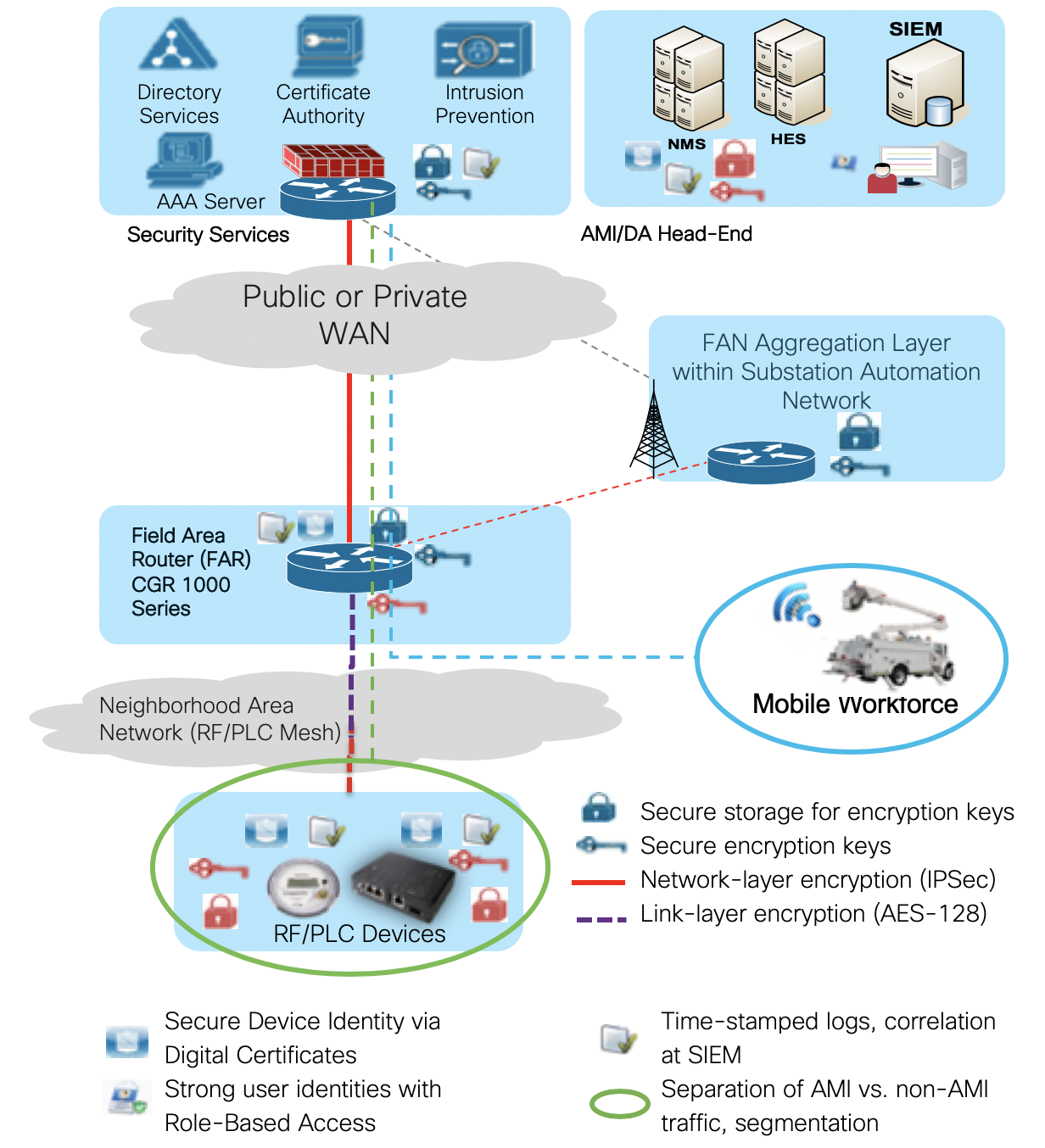
Security Architecture
Cisco’s vision for Smart Grid FAN security is based on principles learned from years as the leader in building secure data networks:
- Maximize visibility into the network environment, devices and events
- Control network users, devices, and traffic
These principles are detailed in Cisco’s Secure Architecture for Enterprise (SAFE) and must be considered when designing and testing the FAN architecture. Two key points to highlight: - Security is a multi-layer challenge requiring different mechanisms between different network locations and devices
- The FAN is dual stack; security policies must apply to both IPv4 and IPv6
The security aspects and protocols covered by the FAN architecture are:
- Secure identity: CGR 1000 and CG-Endpoints (IEEE 802.1AR)
- Network access control: 802.1x-based access control for meters, routers, grid devices
- Authentication, Authorization, and Accounting (AAA): Application servers, IoT FND, HERs, CGR 1000, CG-Endpoints and users
- Data confidentiality: Layer-2 (AES-128), Layer-3 (IPsec), and Layer-7 (ANSI C12.22, DLMS/COSEM, and so on)
- Cryptographic key management
- Network and WAN security: IPv4 and IPv6 route and traffic filtering, including Internet and Utility
- Segmentation and traffic prioritization: VLANs in NOC, potentially different tunnel aggregation endpoints, and so on.
- Physical security: Alerts generated when CGR 1000 physical access is compromised
- Device hardening with 802.1AR and ACT2 security chip