IP Address Management (IPAM)
IPAM centralized management solutions provide capabilities in the allocation, tracking, changing and analyzing of information associated the IP address space throughout the enterprise. These systems consolidate the global inventory of IP addresses and reduce the need for manual and error prone traditional methods.
SD-Access offers a validated integration with InfoBlox IPAM. APIC-EM also has API services for IPAM which enables any 3rd party IPAM solution to integrate with the IPAM capabilities within Cisco SD-Access.

To summarize, some of the key benefits of SD-Access integration with IPAM solutions include:
- Centralized IP Management - Consolidate the management of IP addresses for the full network life cycle of planning, deployment, operations and issue resolution.
- IP Address Analytics - Collect information on how IP addresses have been allocated and utilized for both security and operational purposes
- Consolidation and Sharing across Systems – Integration with other functions such as DHCP and DNS provides consolidation and sharing of overall network IP Addressing to improve users’ onboarding to the network.
Network Orchestrators
Customers who have standardized on the NSO solution as part of their SDN strategy can use NSO solution to orchestrate the Cisco SD‑Access deployment through the APIs provided as part of SD‑Access, through a Network Element Driver (NED) for NSO developed for SD-Access.
The key benefits of SD-Access integration with Network Orchestrators include:
- Consistency across networks: Same solution for current and NFV/SDN networks
- Agile Service Management: Reduces time to market for deploying new services
- Best-in-industry multi-vendor support
All the functions required to provision and operationalize an SD-Access are available through northbound APIs from APIC-EM, ISE and NDP, and are available for external Network Orchestrators to leverage and build custom orchestration solutions on.
Policy Orchestrators
Policy orchestrators provide single pane of glass to manage security policies across the enterprise, leveraging best practices for the full life cycle of security policies including design, provisioning, and operations and auditing. An important feature of Policy orchestrators is the ability to manage security configuration for systems from multiple vendors’ enabling open APIs while significantly reducing the time it takes to deploy and change policy configurations.
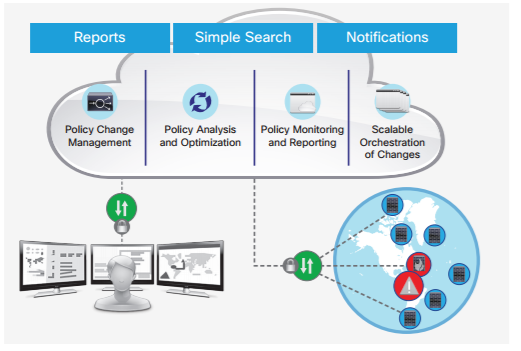
Cisco SD-Access supports AlgoSec and Tufin as the key Policy Orchestration platforms to develop a cross-domain view of policy across the enterprise. This helps network and security teams enhance operations through improved network and security policy visibility.
Cisco SD-Access constituient platforms of APIC-EM, ISE and NDP offer the necessary path tracing and policy APIs that can be used by policy orchestration solutions to build this end-to-end view of network and policy in a simplified manner.
To summarize, some of the key benefits of SD-Access integration with Policy Orchestration solutions include:
- Single Pane of Glass Policy Management - Providing a single point of management for the full life cycle of security policies across the network which includes Firewalls and other security devices.
- Open and Secure Best Practices – Leveraging security best practices enables the management of systems from multiple vendors while providing a rich common API for integration with other management systems.
- Security Assurance - Visualize and track the implementation and operations of security policies across the enterprise to reduce breaches and ensure a secure network.
Security Analytics
As cyber security challenges become more difficult and targeted attacks become more sophisticated, it is imperative for enterprises to have deeper insights on the advanced threats that can compromise their network. Advanced Security Analytics solutions not only provides threat detection technology but it also provides a consolidated view of the entire security incident by automatically linking all relevant events from other security sources in the network. This empowers network and security teams to accelerate incident response and focus their time on more critical issues. Our current partnerships includes integration with security analytics solutions such as StealthWatch that enables simplified collection of telemetry or packet data through controller-based operations. Through the Rapid Threat Containment capabilities of ISE as part of Cisco SD‑Access, hosts identified as being compromised or exhibiting suspect behavior through StealthWatch can be easily quarantined or blocked on the network.
Architectural view of SD-Access integration with StealthWatch
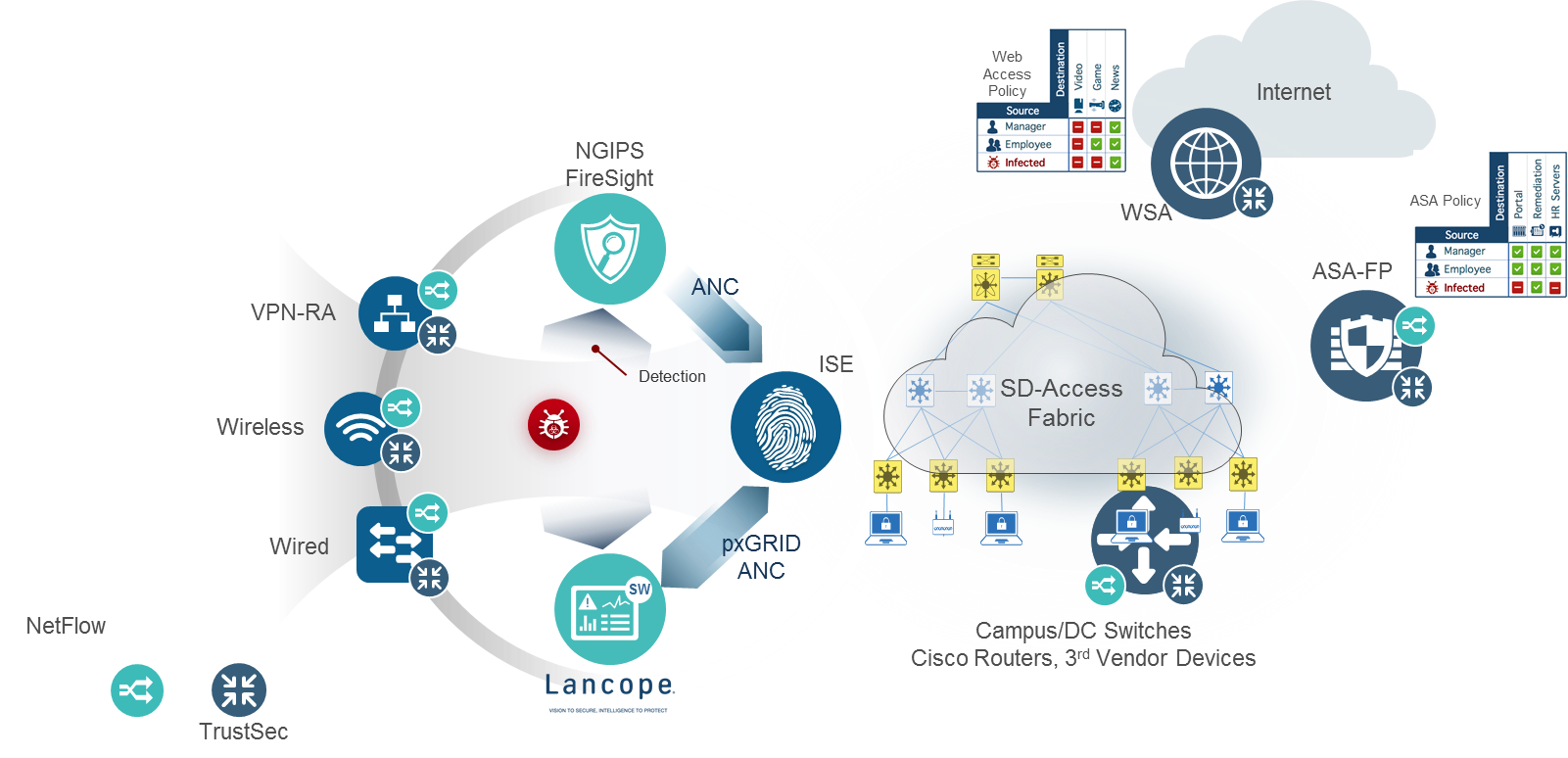
To summarize, some of the key benefits of SD-Access integration with Advanced Security Analytics solutions include:
- Proactively identifying and reporting potential security threats
- Segmenting or isolating the network to contain threats
- Automating security and network operations
Firewalls
As enterprises grow and evolve into multifaceted collections of resources providing many different functions for separate lines of business, multiple user constituents, and varied platforms, security needs to evolve to be able to protect these more dynamic, richer resources against more focused threats. The modern enterprise needs to evaluate how to deploy its intrusion detection and prevention systems as well as its firewall segmentation to determine where existing controls should be re-deployed and whether new capabilities need be added to cover for the "east" and "west" communications. As more controls are deployed throughout the enterprise network, centralized management capabilities become a key requirement. Also, as the resources being protected become increasingly dynamic in their location and use, security functions need to adapt to the new architectures.
Integration of Cisco’s ASA and Firepower Threat Defense Firewalls with Cisco SD-Access, an evolving software-defined architecture for enterprise networks, is a move to provide more centralized control. Access context information from SD‑Access can now be shared with firewalls so that the firewall have full access context information, including the security group context that the host access needs to be classified into. This enables simplified administration and monitoring of traffic through firewalls such as ASA and Firepower Threat Defense Firewalls. Additionally, this enables access policy definitions in firewalls such as Cisco ASA to be based on the endpoint’s security group classification, to simplify policy administration on the firewalls and seamlessly enable user and application mobility.
Deployment modes for Firewall integration in SD-Access
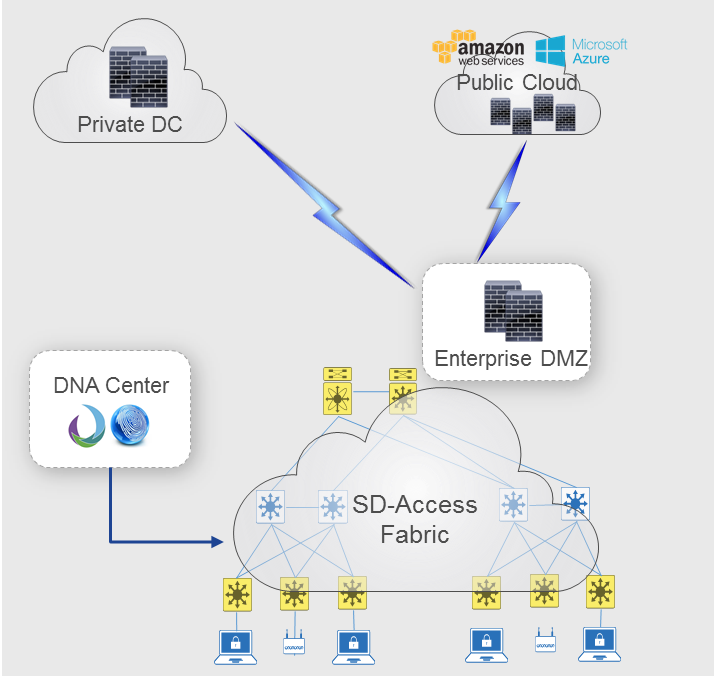
To summarize, some of the key benefits of SD-Access integration with Firewalls such as ASA and Firepower Threat Defense include:
- Security across the enterprise network as the SD-Access fabric can now enforce security policies with consistency across wired and wireless networks.
- Centralized management and automation through APIC-EM controller simplifies the operational complexity associated with pervasive security policy enforcement and provides system-wide visibility of security-aware applications and tenants.
- Built-in security policy lifecycle management enables business agility by rapidly responding to application network and security requirements.
Public and Private Cloud Integration
Enterprises are widely adopting Public Clouds such as Amazon Web Services and Microsoft Azure and Hybrid Clouds especially leveraging hyper converged infrastructure. Enterprise will have Campus, Branch and remote users that would typically consume applications hosted in the public or hybrid cloud. This integration addresses the requirements to address both the Policy and Data plane domains to enable secure application access while ensure high quality user experiences.
The current integration supports Cisco ACI APIC and DCNM for the Data Center with work in progress for Public Cloud Integration such as AWS and Azure.
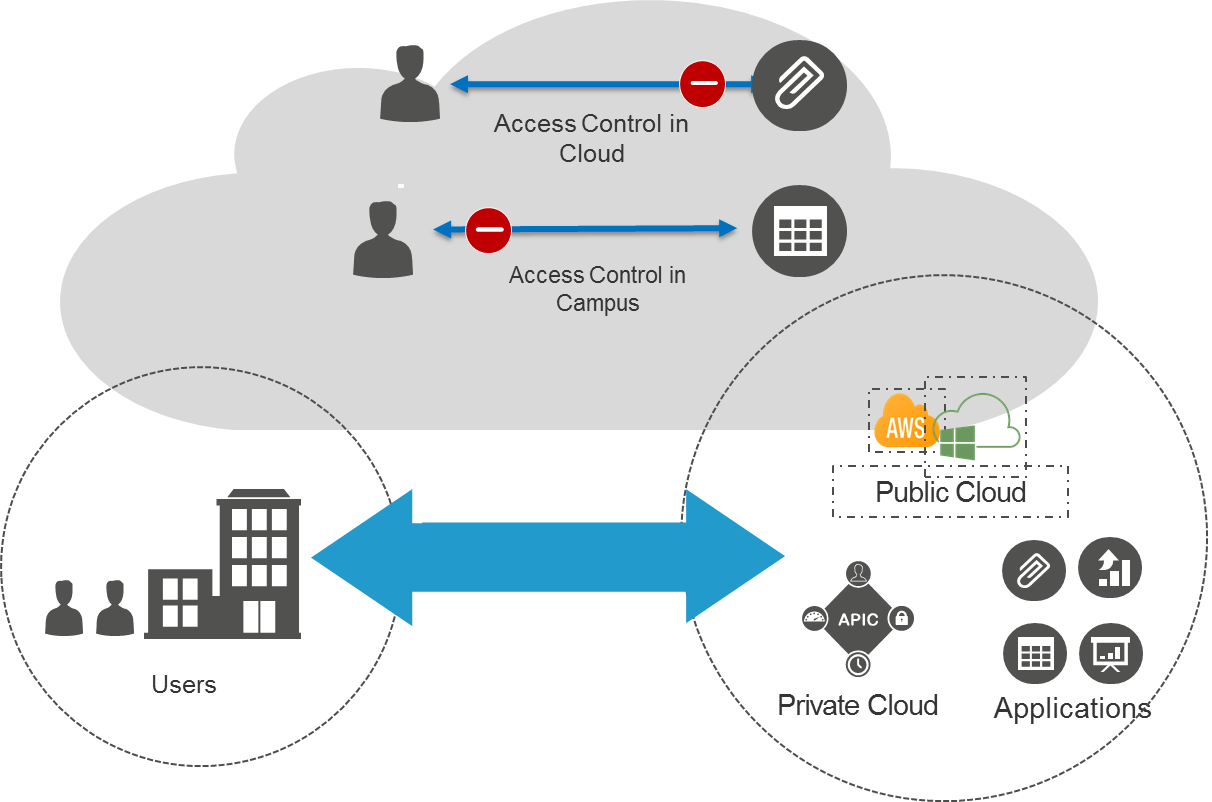
To summarize, some of the key benefits of SD-Access integration with Public and Private Cloud solutions include:
- Sharing of Policy Information – Bridging the policy domain of Users and applications, Administrators have the leverage for protecting corporate data by setting precise access policies around cloud application including contextual data and custom attributes
- Access Control to Cloud Applications - Prevent unauthorized users from accessing important cloud applications and data with the creation of strict policy controls for sensitive data and applications that reside in the cloud
- Application Usage Assurance - Improve the visibility and analysis of the cloud access infrastructure which allows tracking of anomalous traffic patterns in cloud usage with a specific user
IT Services Management (ITSM) - Coming soon
Through our open and extensible SD-Access architecture that also consists of the Network Data Platform, Cisco will be providing strategic, pre-packaged solutions with key ITSM vendors in the future. For example, by streamlining and collecting contextualized network relevant data and sharing it with mature ITSM platforms, IT will be able to utilize the full power of the SD-Access solution as part of its standard IT processes. Streaming telemetry, network assurance, network automation and SD-Access data, and other pertinent data sets through a network database will provide the right level of granularity to create deep insights to rapidly diagnose and remediate the top problems in IT.