Generating Certificates
In this example, we will create the pxGrid client certificate in PKCS12 format. You will also want to test in PEM format, when you go for your pxGrid certification.
- Select Administration->pxGrid Services->Certificates-> provide the following information
Note: CN name should be Fully Qualified Domain Name (FQDN) resolvable. PKCS12 format is not supported using Python libraries.
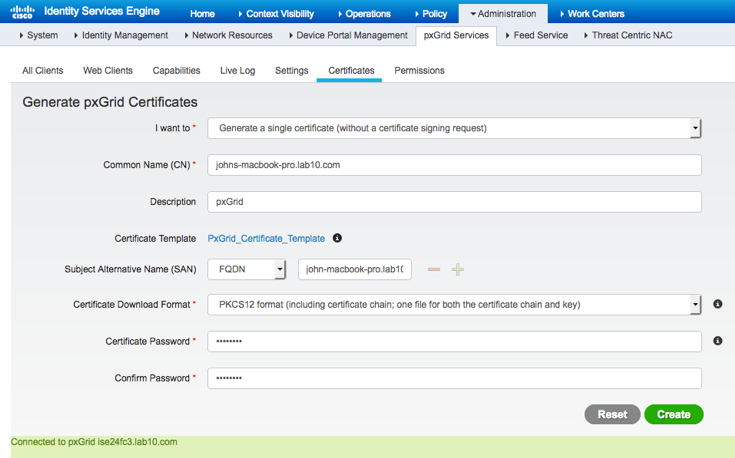
Select Create
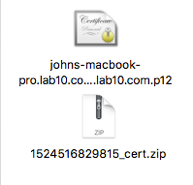
Download the zipped file You should see:
- Note, if using PEM format, when you unzip the file you will see the following:
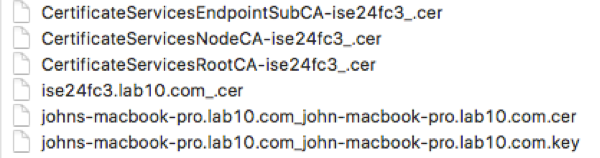
Note: Please refer to https://communities.cisco.com/docs/DOC-71928 , using iSE 2.2 Internal CA to deploy to pxGrid clients (java keystores), for Productional ISE deployments, please refer to: https://communities.cisco.com/docs/DOC-68284
Converting Certificates to JKS format
The PKCS12 certificate is converted into the keystore filename and truststore filename.
openssl pkcs12 -export -out session.p12 -inkey Johns-Macbook-Pro.lab10.com_Johns-Macook-Pro.lab10.com.key -in Johns-Macbook-Pro.lab10.com_Johns-Macook-Pro.lab10.com.cer -chain -CAfile CA1.cer
Enter pass phrase for Johns-Macbook-Pro.lab10.com_Johns-Macook-Pro.lab10.com.key:
Enter Export Password: Cisco123
Verifying - Enter Export Password: Cisco123
keytool -importkeystore -srckeystore session.p12 -destkeystore session1.jks -srcstoretype PKCS12
Enter destination keystore password: Cisco123
Re-enter new password: Cisco123
Enter source keystore password: Cisco123
Entry for alias 1 successfully imported.
Import command completed: 1 entries successfully imported, 0 entries failed or cancelled
openssl x509 -outform der -in CA1.cer -out CA1.der
keytool -import -alias session1 -keystore rootsession.jks -file CA1.der
Enter keystore password: Cisco123
Re-enter new password: Cisco123
Owner: CN=Certificate Services Endpoint Sub CA - ise24fc3
Issuer: CN=Certificate Services Node CA - ise24fc3
Serial number: 589713fe8d1d4c99b580aae99e862c4f
Valid from: Thu Apr 12 22:42:16 EDT 2018 until: Thu Apr 13 22:42:14 EDT 2028
Certificate fingerprints:
MD5: 8E:B3:9F:92:B8:E4:80:51:64:68:4C:72:44:51:15:3F
SHA1: 5D:EF:20:E1:9C:CA:5D:F7:15:28:FA:1D:4D:4F:A9:79:CD:E5:A6:FC
SHA256: FB:C5:84:4B:30:D3:8E:95:B9:FE:28:54:EC:60:A7:E4:4B:A7:6D:1C:8D:8C:0C:15:C0:4B:2C:37:4A:43:8F:0C
Signature algorithm name: SHA256withRSA
Version: 3
Extensions:
# 1: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 10 B0 23 A7 DF 3C F7 9D 54 F7 B2 34 12 21 DE 91 ..#..<..T..4.!..
0010: A4 6D 33 CE .m3.
]
[CN=Certificate Services Root CA - ise24fc3]
SerialNumber: [ 6f56a636 30094fa4 b4b85ac9 4f5def5b]
]
# 2: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:true
PathLen:2147483647
]
# 3: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
Key_CertSign
]
# 4: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 33 47 E4 40 4B 5E 0C 08 77 DE A2 77 30 50 E9 3C 3G.@K^..w..w0P.<
0010: 12 78 92 39 .x.9
]
]
Trust this certificate? [no]: yes
Certificate was added to keystore
keytool -import -alias session2 -keystore session1.jks -file Johns-Macbook-Pro.lab10.com_Johns-Macook-Pro.lab10.com.cer Enter keystore password: Cisco123
Certificate already exists in keystore under alias <1>
Do you still want to add it? [no]: yes
Certificate was added to keystore
keytool -import -alias session3 -keystore rootsession.jks -file CA1.cer
Enter keystore password: Cisco123
Certificate already exists in keystore under alias <session1>
Do you still want to add it? [no]: yes
Certificate was added to keystore
keytool -import -alias session4 -keystore rootsession.jks -file CertificateServicesRootCA-ise24fc3_.cer
Enter keystore password: Cisco123
Owner: CN=Certificate Services Root CA - ise24fc3
Issuer: CN=Certificate Services Root CA - ise24fc3
Serial number: 23471fb4679a4836b6023da18e312e3e
Valid from: Thu Apr 12 22:42:14 EDT 2018 until: Thu Apr 13 22:42:14 EDT 2028
Certificate fingerprints:
MD5: 94:EA:6F:D5:E6:D6:A4:53:D2:69:7E:C6:6F:02:AB:2D
SHA1: F8:8A:36:C8:45:F0:A5:01:32:32:E0:8D:59:E4:F9:A2:24:A6:71:47
SHA256: 19:2F:41:EC:93:C7:EE:BB:CC:22:AB:44:24:FF:95:AF:E0:5F:5F:30:F9:D4:7C:84:43:91:93:A6:47:1C:67:97
Signature algorithm name: SHA256withRSA
Version: 3
Extensions:
# 1: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:true
PathLen:2147483647
]
# 2: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
Key_CertSign
]
# 3: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: AE 42 CE AB 57 30 7C 75 F8 10 94 25 0E DC DF FA .B..W0.u...%....
0010: 9E 7F 3A 57 ..:W
]
]
Trust this certificate? [no]: yes
Certificate was added to keystore