Stream sensor data
Alert: Cisco has made the end-of-life (EOL) announcement for the Cisco Industrial Asset Vision (IAV).
The Cisco Industrial Asset Vision(IAV) product allows streaming telemetry and alert data to customer's external MQTT (Message Queuing Telemetry Transport) and telemetry data to Microsoft Azure IoT nodes. The telemetry data from the IAV application can be used by the customer for analytics, larger capacity storage, and so on as applicable. The integration of the external applications with the IAV dashboard can be done using the Integration feature.
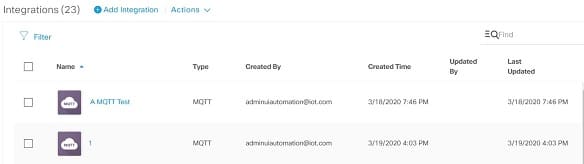
The Integrations list view displays the list of integrations with Name, Type, Created By, Created Time, Updated By, and Last Updated details of each Integration.
Add integration
An external application should meet the following prerequisites before it can be integrated with the IAV dashboard.
- The destination server should be configured with user credentials. (If basic authentication is used for MQTT, then, the destination broker should be configured with password-based authentication.)
- For an SSL (Secure Sockets Layer) connection, the destination server should have a trusted CA (Certificate Authority) signed SSL certificate and not self-signed SSL certificates.
- For creating a new integration, the user should be aware of the Connection Details of the destination server, such as Host IP/name , Port number, user credentials, and Topic Pattern in case of an MQTT server.
- The destination server should be reachable from the IAV SaaS solution deployed in the AWS (Amazon Web Services) cloud.
Perform following steps to add a new integration to the system.
Add an MQTT Server Integration
To add an MQTT Server Integration, complete the required fields and click Add.
- From the left menu, click Administration > Integrations.
- In the right pane, click Add Integrations and select MQTT Server.
| Field | Description |
|---|---|
| Destination Details | |
| Name | The name for the MQTT Server Integration. |
| Description | The optional description for the MQTT Server Integration. |
| Connection Details | |
| Host | IP or hostname of the destination MQTT server where the telemetry data has to be published. Note: Private IP range as defined in RFC1918 is not allowed. |
| Port | Port number of the destination MQTT server. It can range from 1-65535. MQTT (non-TLS (Transport Layer Security)) port is typically 1883. Standard MQTT (TLS) port is typically 8883. |
| Client ID | The unique identifier for the client server. This is an optional field. If this is specified then the system internally suffixes the Client ID with: * -data for telemetry data * -alert for alert data Example: If clientID is "iavclient", then the unique clientIDs will be "iavclient-data" and "iavclient-alert". |
| Choose publishing options | Select an option from the drop-down list based on the publishing type and enter the Topic Pattern for the selection. The dynamic topic patterns are supported for MQTT integrations. To use the Dynamic topic pattern, use the ${DEVEUI} placeholder value in the topic path. At run time, this value will be replaced by the DevEUI value for Sensors and by the Serial Number for Network devices. Note: The value of the DevEUI or Gateway Serial number will always be in upper case while subscribing to the Topic in MQTT on the server side. The topic is configurable. For example, cisco/${DEVEUI}/data. Note: This dynamic topic pattern value can be used only once within the topic path. The dynamic pattern is supported for both the Data and Alerts Topic paths. * Data Only — Only telemetry data is sent out over MQTT. * Alerts Only — Only alert data is sent out over MQTT. * Data and Alerts — Both telemetry and alert data are sent out over MQTT. |
| Enable SSL/TLS | This should be enabled when using Cert-based auth. When enabled, the connectivity between the IAV and the customer's MQTT broker will be over TLS. In this case, the SSL certificate on the broker will need to be from a well-known CA. |
| Choose the credential type | Select the type of authentication. If you choose Basic, then enter your Username and Password. If you choose Cert based auth, then drag and drop to upload Server CA Certificate, Client Certificate, and Client Private Key. Note: Only .crt, .pem and .key files are accepted. |
| Connection Timeout (sec) | The time duration for which a connection attempt will be made between the MQTT node and the destination MQTT server, after which, the timeout error will appear. |
| Advanced Settings | |
| Clean Session | If enabled, then the connection between the MQTT node and the destination MQTT server is not persistent and any subscription details or undelivered message is deleted from the node. If not enabled, then a persistent connection exists between the node and the destination server, and the same session is reused for delivering the next set of messages. |
| Test Connection | Click this to verify your connection. * If you get an error message, check whether the details entered are correct, and the MQTT server is up and running. * If you get a success message, go to the next step. |
Add a Microsoft Azure IoT Integration
Before adding a Microsoft Azure IoT Integration, perform the following steps:
- Sign up for an Azure account if needed.
- Create an IoT hub.
- Add a device
- Specify the Auth as SAS token. In this release, SAS token-based authentication is supported.
- Generate a token.
To add a Microsoft Azure IoT Integration, complete the required fields and click Add.
- From the left menu, click Administration > Integrations.
- In the right pane, click Add Integrations and select Microsoft Azure IoT.
| Field | Description |
|---|---|
| Destination Details | |
| Name | The name for the Microsoft Azure IoT Integration. |
| Description | The optional description for the Microsoft Azure IoT Integration. |
| Connection Details | |
| Host | IP or hostname of the destination Microsoft Azure IoT where the telemetry data has to be published. You can get this information from the Azure IoT Hub Overview page. Note: Private IP range as defined in RFC1918 is not allowed. |
| Device ID | The ID for the device. The device is used as a service account and the telemetry data is sent to Azure from the sensors present in IAV using the Device ID. |
| Choose publishing options | Select an option from the drop-down list based on the publishing type. * Data Only — Only telemetry data is sent out over Azure IoT. * Alerts Only — Only alert data is sent out over Azure IoT. * Data and Alerts — Both telemetry and alert data are sent out over Azure IoT. Note: The Topic Pattern for the publishing options is pre-populated and not editable. |
| Choose the credential type | Select the type of authentication. * If you choose Shared Access Signature, then enter the SAS Key. Then, drag and drop or upload the CA Certificate. * If you choose Cert based auth, then drag and drop to upload Server CA Certificate, Client Certificate, and Client Private Key. Note: Only .crt and .pem files are accepted. |
| Test Connection | Click this to verify your connection. * If you get an error message, check whether the details entered are correct, and validate them using Azure CLI tools. * If you get a success message, go to the next step. Note: Do not use the same SAS token in other applications since Azure allows only one connection per Device. |